Critical vulnerabilities in Xerox FreeFlow Core, a widely-used print orchestration platform, allow unauthenticated remote attackers to execute malicious code on vulnerable systems.
The flaws, tracked as CVE-2025-8355 and CVE-2025-8356, affect the JMF Client service and have been patched in FreeFlow Core version 8.0.5.
Key Takeaways
1. Two critical vulnerabilities in Xerox FreeFlow Core allow remote code execution attacks.
2. Print shops, universities, and government agencies using FreeFlow Core are at risk.
3. Upgrade immediately to patch vulnerabilities.
The vulnerabilities were initially discovered during an investigation of what appeared to be a false positive detection, ultimately revealing serious security weaknesses that could compromise systems handling sensitive pre-publication marketing materials and commercial printing operations.
XXE Injection Vulnerability
Horizon3.ai reports that the vulnerability, CVE-2025-8355, is an XML External Entity (XXE) injection flaw affecting the JMF Client service listening on port 4004.
This service processes Job Message Format (JMF) messages for managing print jobs and status reporting. The vulnerability exists in the jmfclient.jar binary, which contains an XML parsing utility that fails to properly sanitize or restrict XML External Entity usage.
Attackers can exploit this weakness by submitting specially crafted XML requests to perform Server-Side Request Forgery (SSRF) attacks.
The XML parser processes external entities without validation, allowing malicious actors to read local files, scan internal networks, or potentially access sensitive information from backend systems.
This vulnerability provides an entry point for reconnaissance activities and can be chained with other attacks to escalate privileges within the target environment.
Path Traversal Vulnerability
The more severe vulnerability, CVE-2025-8356, is a path traversal flaw discovered in the file processing mechanism of JMF commands.
Security researchers identified that the processIncomingRQEMessage() function fails to validate file paths during upload operations properly, enabling directory traversal attacks.
Attackers can craft malicious JMF command messages containing “../” sequences to escape the intended upload directory and write files to arbitrary locations on the server filesystem.
This capability allows placement of webshells in publicly accessible directories, leading to remote code execution.
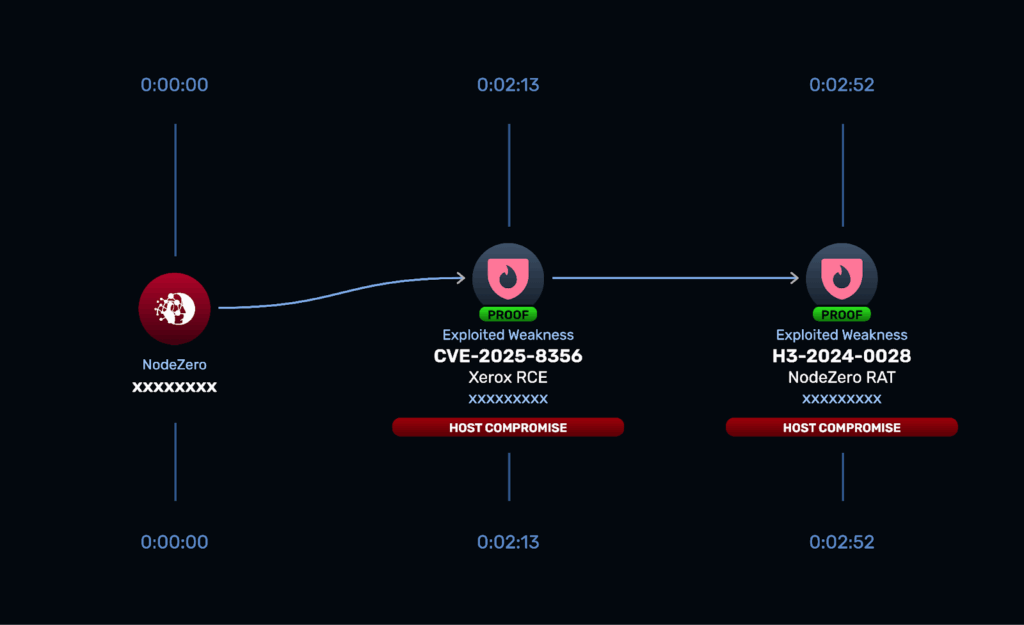
While the JMF Client service on port 4004 cannot directly serve uploaded files, the primary web portals provide the necessary functionality to execute malicious payloads, making this vulnerability particularly dangerous for organizations running FreeFlow Core installations.
| CVE ID | Title | CVSS 3.1 Score | Severity |
| CVE-2025-8355 | External XML Entity (XXE) Injection Vulnerability | 7.5 | High |
| CVE-2025-8356 | Path Traversal Vulnerability | 9.8 | Critical |
Both vulnerabilities pose significant risks to organizations using FreeFlow Core, particularly commercial print shops, universities, government agencies, and marketing providers who handle sensitive pre-publication materials.
Xerox has addressed these issues in FreeFlow Core version 8.0.5, and security experts strongly recommend immediate upgrades to prevent potential exploitation of these critical flaws.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.
