A cybersecurity researcher has discovered that hundreds of publicly accessible TeslaMate installations are exposing sensitive Tesla vehicle data without authentication, revealing GPS coordinates, charging patterns, and personal driving habits to anyone on the internet.
The vulnerability stems from misconfigured deployments of the popular open-source Tesla data logging tool, which connects to Tesla’s official API to collect comprehensive vehicle telemetry data.
Key Takeaways
1. Hundreds of TeslaMate installations leak real-time Tesla data.
2. The researcher used masscan and httpx to scan port 4000 internet-wide, mapping vulnerable vehicles on teslamap.io.
3. Tesla owners must add authentication, firewalls, and VPN access.
GPS and Location Data Leak
Security researcher Seyfullah KILIÇ conducted an extensive internet-wide scan to identify exposed TeslaMate instances using sophisticated reconnaissance techniques.
The methodology involved deploying masscan across multiple 10Gbps servers to sweep the entire IPv4 address space for open port 4000, which hosts TeslaMate’s core application interface.
Following the initial discovery phase, the researcher utilized httpx to filter and identify genuine TeslaMate installations by detecting the application’s distinctive HTTP response signatures:
The scanning operation successfully identified hundreds of vulnerable instances exposing real-time Tesla vehicle data, including precise GPS coordinates, vehicle model information, software versions, charging session timestamps, and detailed location histories.
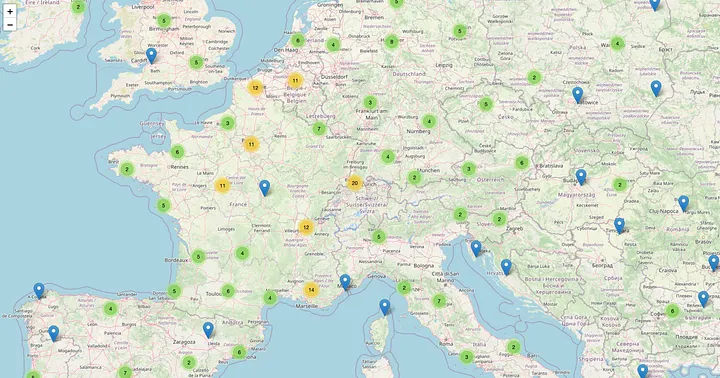
The researcher created a demonstration website at teslamap.io to visualize the geographical distribution of exposed vehicles, illustrating the severity of the privacy breach.
Mitigations
The fundamental security flaw lies in TeslaMate’s default configuration, which lacks built-in authentication mechanisms for critical endpoints.
When deployed on cloud servers with port 4000 exposed to the internet, the application becomes immediately accessible to unauthorized users worldwide.
Additionally, many installations run Grafana dashboards on port 3000 with default or weak credentials, creating multiple attack vectors.
Tesla owners operating TeslaMate instances must implement immediate security measures to protect their vehicle data. Essential protections include configuring reverse proxy authentication using Nginx:
Additional security measures include restricting access through firewall rules, binding services to localhost interfaces, and implementing VPN-based access controls.
The research highlights the critical importance of secure deployment practices for Internet of Things (IoT) applications, particularly those handling sensitive personal and location data from connected vehicles.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.
