Malware persistence techniques enable attackers to maintain access to compromised endpoints despite system reboots, credential changes, or other disruptions. Common methods include altering configurations, injecting startup code, and hijacking legitimate processes.
These approaches ensure the malware or attacker remains active, allowing malicious activities to continue without the need for re-exploitation.
In this article, we will examine the nature of malware persistence techniques, their impact, and strategies for defending against them.
Common malware persistence techniques
The MITRE ATT&CK framework catalogs a range of techniques used by threat actors to maintain persistence. Below are examples of malware persistence techniques from the framework that allow attackers to sustain long-term access to compromised endpoints:
T1053 – Scheduled Task/Job
Adversaries abuse task scheduling features to run malicious code repeatedly or at set intervals. Built-in utilities such as Task Scheduler (Windows), cron (Linux), and launchd (macOS) can execute programs or scripts at specified times or in response to certain events.
T1037 – Boot or Logon Initialization Scripts
Attackers configure scripts to execute during system boot or user logon, ensuring persistence or privilege escalation. On Linux, mechanisms like rc.local, init.d, or systemd are commonly used to launch malicious code at startup.
T1543 – Create or Modify System Process
System-level processes such as Windows services, Linux daemons, or macOS launchd agents run automatically in the background. Threat actors can install or modify these processes to execute malicious payloads on startup or during system operation.
T1136 – Create Account
Adversaries may create new local, domain, or cloud user accounts on compromised systems to maintain access. With sufficient privileges, these accounts can be used for ongoing access without requiring persistent remote access tools.
T1098 – Account Manipulation
Account manipulation enables attackers to maintain or elevate access by modifying credentials, changing group memberships, or bypassing security policies. For example, adding an SSH key to ~/.ssh/authorized_keys enables persistent remote access without needing a password.
Impact of malware persistence techniques
Malware persistence techniques are designed to ensure attackers maintain long-term access to compromised systems. Below, we explore some impacts of malware persistence techniques.
Extended dwell time
Malware persistence techniques enable attackers to remain in a compromised environment for a prolonged period without requiring re-exploitation.
This extended presence, often lasting weeks or months, gives them time to explore the network, escalate privileges, and plan their next moves carefully before detection.
Remediation evasion
Even after initial removal, attackers can regain access using persistence mechanisms such as scheduled tasks, malicious services, or unauthorized user accounts.
This makes cleanup efforts ineffective unless all persistence mechanisms are identified and removed.
Data exfiltration
Persistent access is often used in Advanced Persistent Threats (APTs), where attackers gradually exfiltrate data over an extended period to maintain long-term infiltration and exploitation.
This allows sensitive information, such as credentials or business data, to be stolen over time.
Deployment of additional malware
With continuous access, attackers can introduce additional malicious tools, including ransomware, backdoors, or remote access trojans.
This can further compromise the system or expand the attack surface across the network.
Compromised regulatory compliance
Malware persistence techniques enable attackers to maintain unauthorized access to systems over an extended period.
This long-term access can lead to violations of regulatory standards, such as GDPR, HIPAA, and PCI DSS, which require strict data protection, system integrity, and breach notification.
Protect your systems against hidden threats. Learn how attackers use malware persistence techniques, and how Wazuh helps you detect and stop them.
Learn More About Wazuh
How to defend against malware persistence techniques
Defending against persistence techniques requires a layered approach that combines detection, prevention, and incident response.
Below are some key defense strategies:
1. Patch management: Several persistence techniques exploit known vulnerabilities in operating systems, applications, or drivers. By regularly applying patches to these components, you can significantly reduce the available attack surface.
2. File Integrity Monitoring (FIM): FIM helps detect unauthorized changes to critical files, such as startup scripts, scheduled task configurations, registry keys, or application binaries. By monitoring these sensitive files, you can identify when attackers attempt to gain persistence.
3. User account monitoring: Persistence often involves creating new user accounts, modifying existing ones, or escalating privileges. Continuous monitoring of account creation, deletion, and permission changes can reveal suspicious behavior.
4. Harden system configurations: Securing baseline configurations reduces the risk of attackers abusing system features for persistence. This includes disabling unused services, enforcing strong password policies, limiting administrative privileges, and using group policies to restrict autorun behavior.
5. Threat hunting: Conducting proactive threat hunts allows security teams to detect hidden persistence mechanisms that evade automated tools. This includes searching for suspicious behavior, such as unusual process executions, scheduled tasks, or long-dormant malware.
6. Endpoint security: Deploying robust endpoint protection tools such as XDR enables real-time monitoring of activity and blocks known persistence behaviors. Modern endpoint tools can detect and automatically respond to indicators like registry changes, service installations, and unauthorized script execution.
How Wazuh defends against malware persistence techniques
Wazuh is a free and open source enterprise-ready security solution that provides unified SIEM and XDR protection across several workloads.
It provides a centralized view for threat detection and security monitoring across virtualized, on-premises, cloud-based, and containerized environments.
Wazuh offers several capabilities to defend against malware persistence techniques. These capabilities include, but are not limited to:
- Active response
- File Integrity Monitoring (FIM)
- Security and Configuration Assessment (SCA)
- Log data analysis
- Vulnerability detection
Active response
The Wazuh Active Response module enables security teams to automate response actions based on predefined triggers, helping them efficiently manage security incidents. Automation ensures that high-priority events are addressed promptly and consistently.
Wazuh provides several built-in response scripts that can perform actions such as blocking malicious network traffic or removing infected files from monitored endpoints.
In the example below, the Active Response module disables a Linux account that has been targeted by brute-force login attempts.
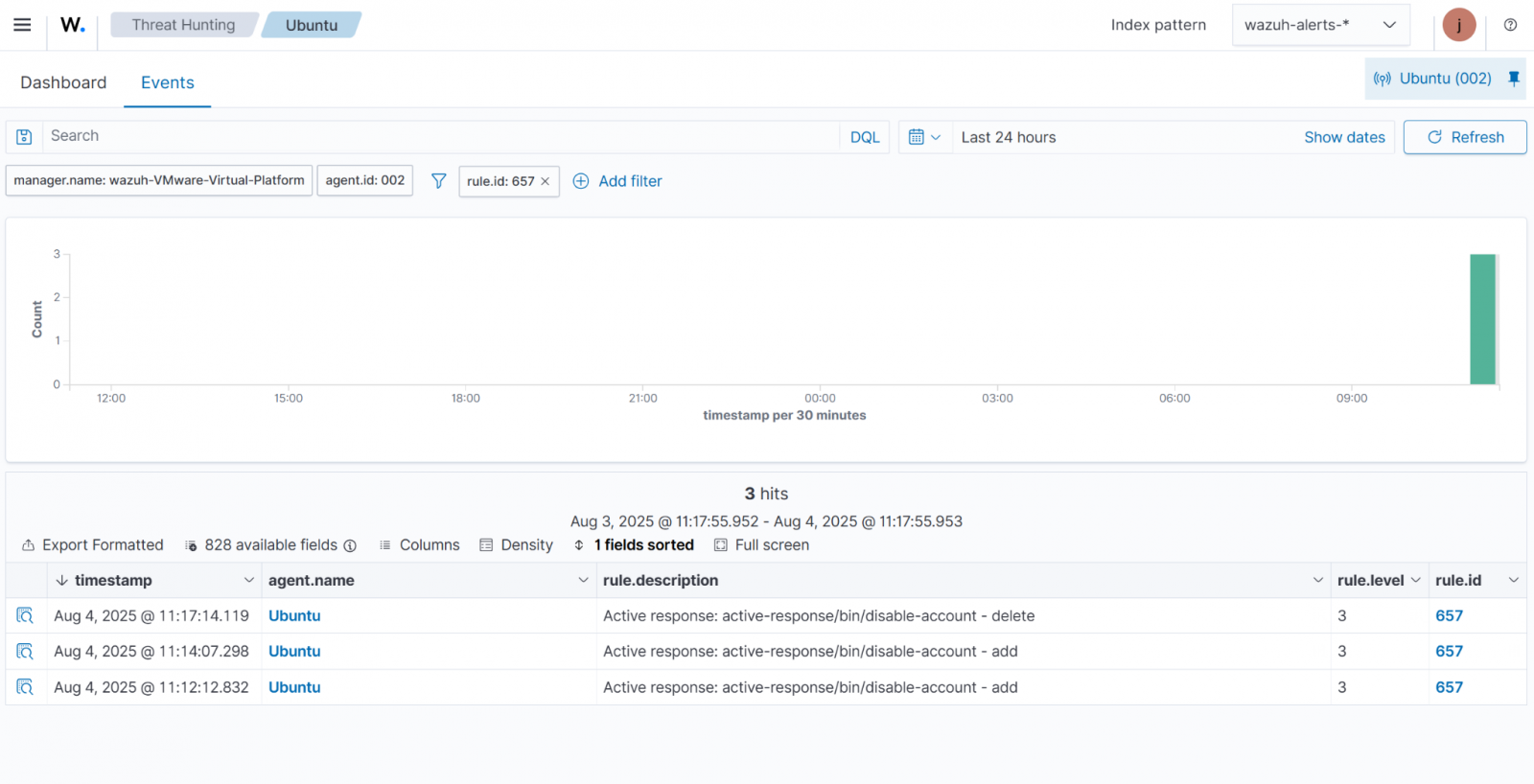
File Integrity Monitoring (FIM)
The Wazuh FIM module monitors files and directories, generating alerts when a user or process creates, modifies, or deletes monitored files. It builds a baseline by scanning and storing checksums and file attributes.
When a user or process changes a file, the module compares its checksum and attributes with the baseline and triggers an alert if a mismatch is detected.
The blog post Detecting Common Linux Persistence Techniques with Wazuh highlights how the Wazuh FIM module detects malware persistence on Linux endpoints.
We use the FIM module to monitor changes to systemd services and timers on a monitored endpoint. Since systemd manages services and startup tasks, monitoring its configuration files is important for detecting unauthorized changes.
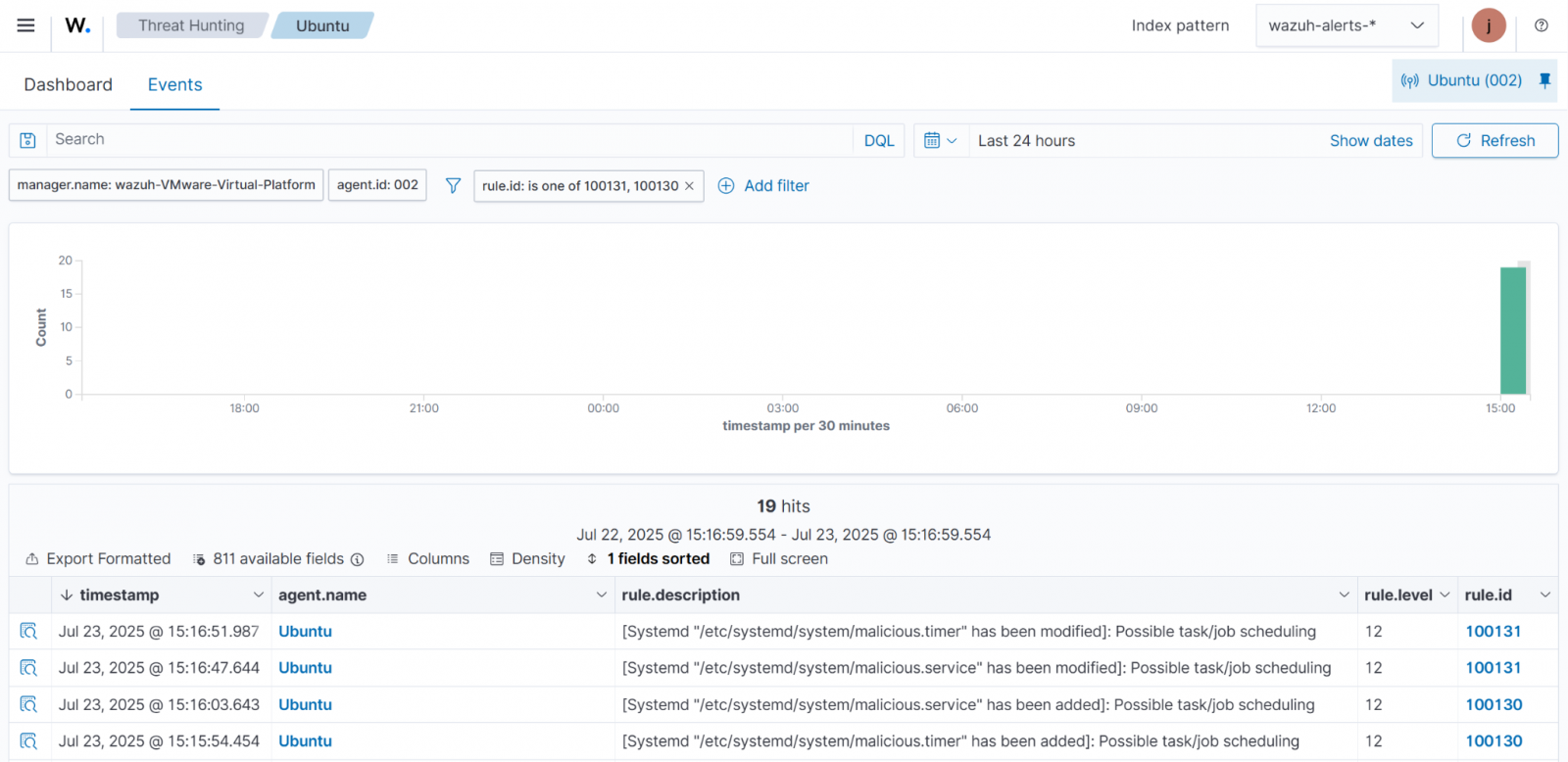
Security and Configuration Assessment (SCA)
System hardening reduces the attack surface by eliminating misconfigurations and unnecessary components. The Wazuh SCA module helps improve system hardening by scanning monitored endpoints to detect misconfigurations and recommending remediation actions. It uses policy files to check system settings, files, processes, and registry entries.
For example, the Wazuh SCA can assess whether it is necessary to change password policies, remove unnecessary software, disable unnecessary services, or audit the network configurations.
In Figure 3 below, the Wazuh SCA scan result shows failed because the public key authentication for SSH is not enabled.
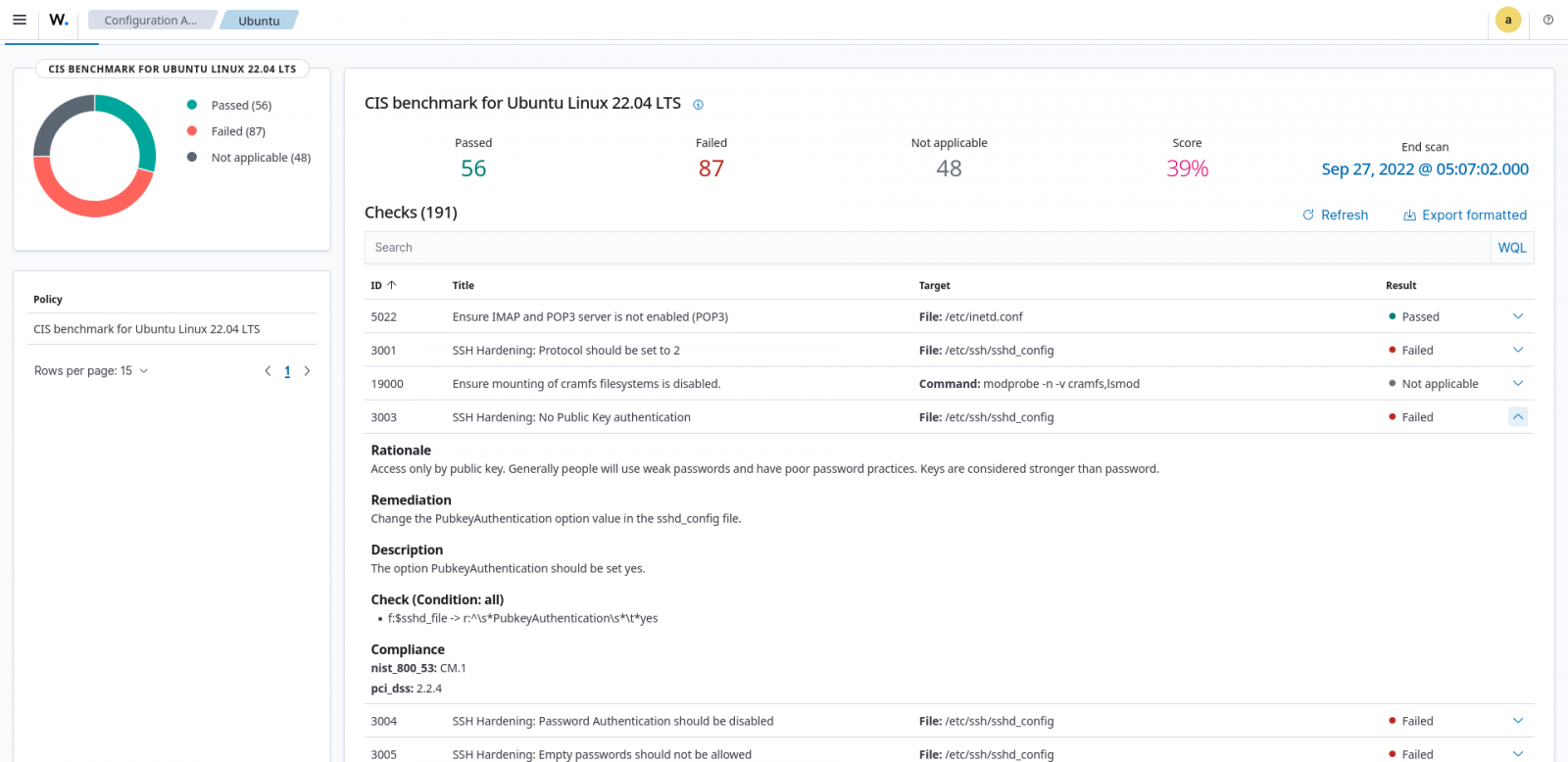
Log data analysis
Wazuh provides visibility into your IT infrastructure by collecting, analyzing, and storing logs from endpoints, network devices, and applications.
The Wazuh agent, running on a monitored endpoint, collects and forwards system and application logs to the Wazuh server for analysis. Log data analysis enables threat detection, performance monitoring, troubleshooting, compliance auditing, and the identification of anomalous activities.
In Detecting Windows persistence techniques with Wazuh, the Wazuh agent collects logs from a Windows endpoint and forwards them to the Wazuh server for analysis. This helps identify signs of malware persistence, such as unauthorized account creation, changes to startup folders or registry keys, and modifications to services.
Figure 4 below illustrates the detection of a modification to a Windows service.
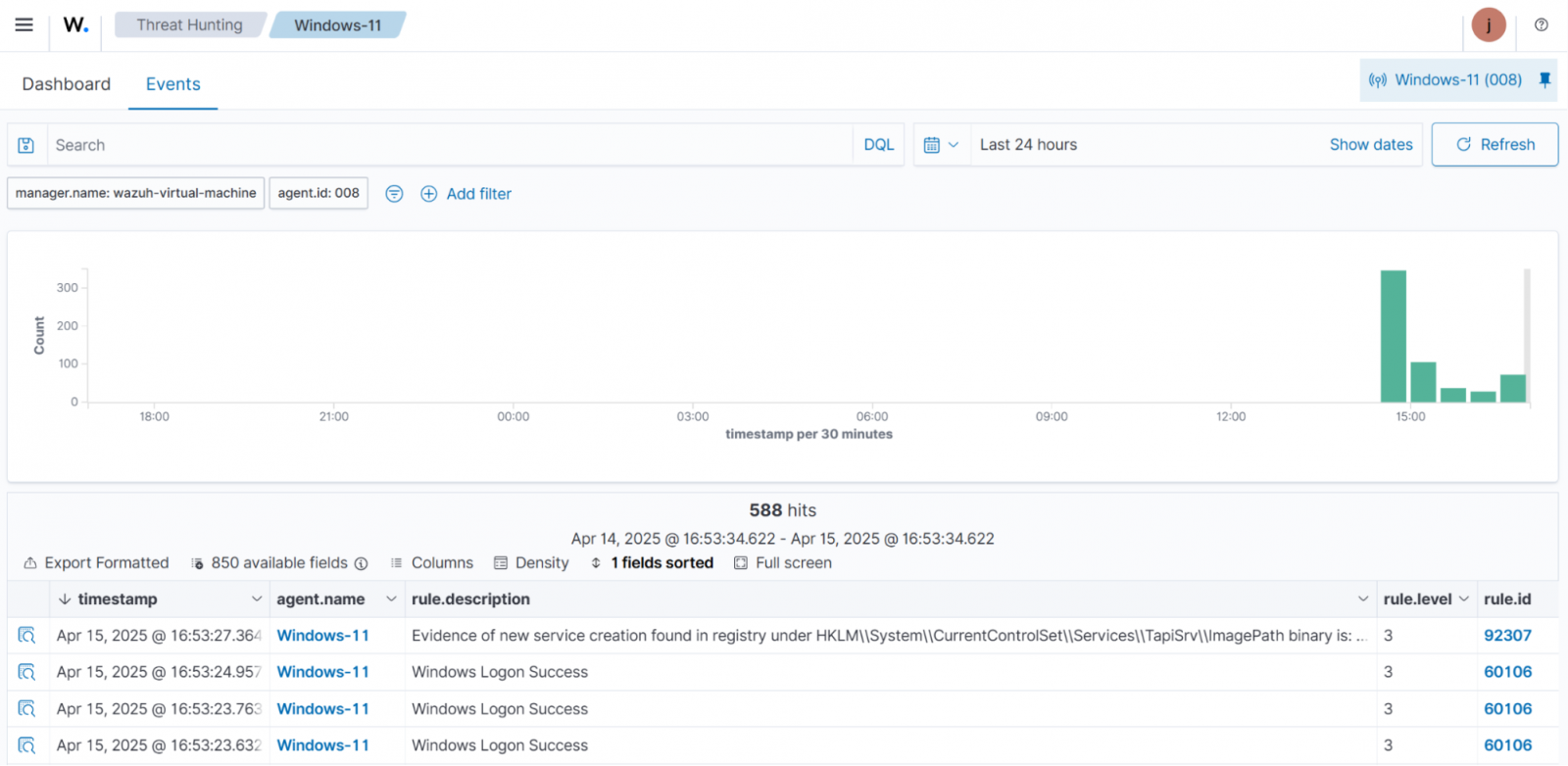
Vulnerability detection
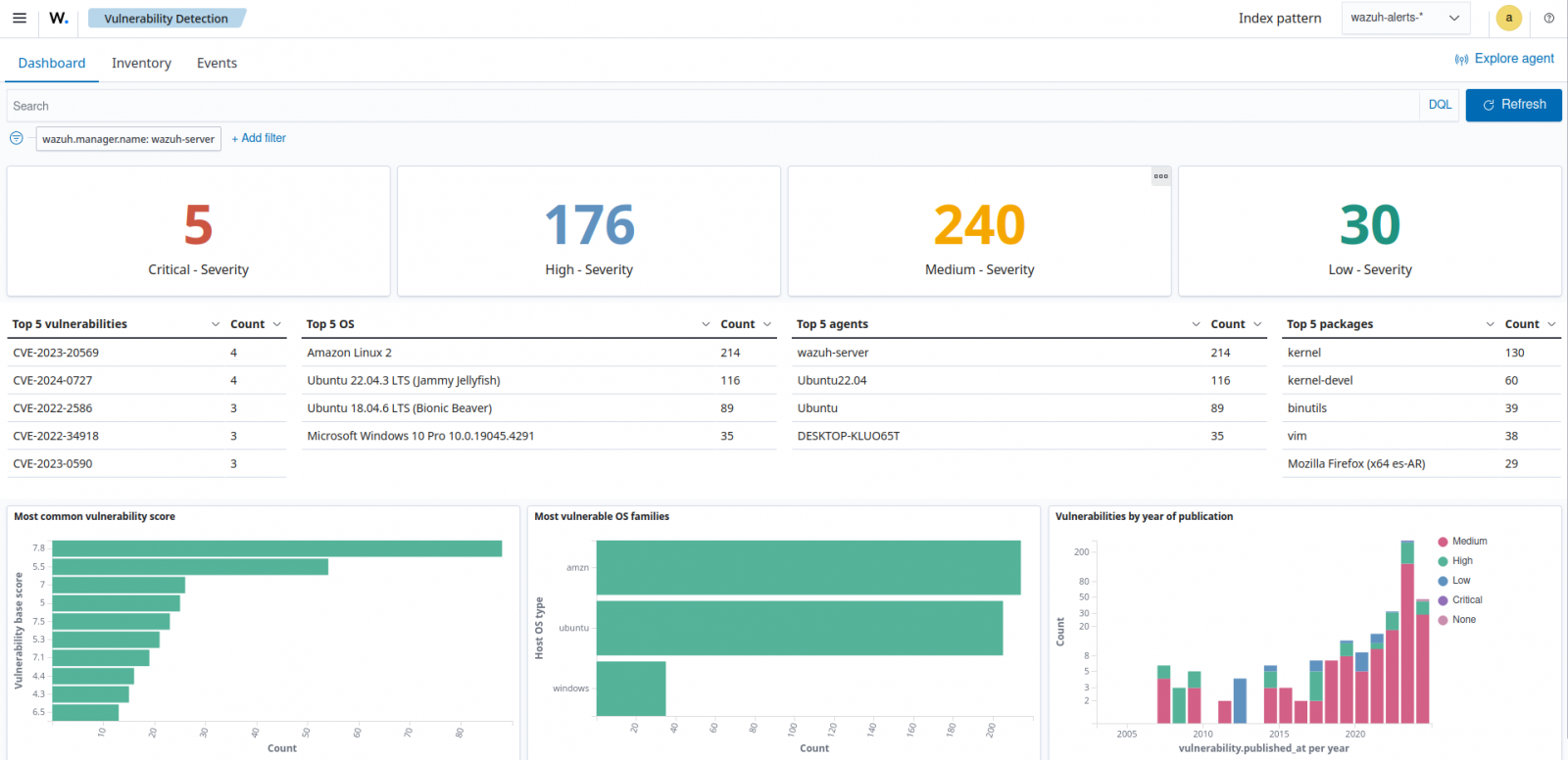
The Wazuh Vulnerability Detection module identifies vulnerabilities in the operating system and installed applications by correlating software inventory with known vulnerability data in the Wazuh CTI platform. It generates alerts displayed on the Wazuh dashboard, giving a clear view of vulnerabilities across all monitored endpoints.
This helps security teams take proactive measures to reduce risk and strengthen system defenses before exploitation occurs.
The vulnerability detection dashboard in Figure 5 below highlights the package name, OS, agent, vulnerability ID, and severity of detected vulnerabilities.
Conclusion
Malware persistence techniques enable attackers to maintain long-term access to compromised systems, posing significant risks to organizational security.
Defending against these techniques requires a multi-layered approach that combines proactive measures, such as system hardening, FIM, regular patching, threat hunting, and user monitoring.
Wazuh enhances threat defense by providing several capabilities to detect and respond to suspicious activity across monitored endpoints, including malware persistence techniques. It enables security teams to monitor for unauthorized changes, scheduled tasks, unusual processes, account modifications, and other indicators of compromise.
Start using Wazuh today to strengthen your organization’s defense strategy. You can also join their community for professional support.
Sponsored and written by Wazuh.
