A sophisticated malware campaign that weaponizes a seemingly legitimate PDF editor to steal sensitive data and login credentials from unsuspecting users across Europe.
The attack uncovered by Truesec, dubbed “TamperedChef,” represents a new evolution in social engineering tactics that leverage trusted software categories to deploy information-stealing malware.
The malicious campaign centers around AppSuite PDF Editor, a free PDF editing tool promoted across multiple websites and distributed through Google advertising campaigns.

What makes this attack particularly insidious is its patient approach. The software initially appears harmless, functioning as advertised while secretly establishing persistence mechanisms and awaiting activation commands.
The campaign’s sophistication is evident in its execution timeline. Beginning on June 26, 2025, threat actors registered multiple domains and began promoting the PDF editor through at least five different Google advertising campaigns.
The malware remained dormant for 56 days strategically timed to coincide with typical Google advertising campaign durations—before activating its malicious capabilities on August 21, 2025.
Upon installation, the software establishes communication with command-and-control servers through specific URLs, including inst.productivity-tools.ai and vault.appsuites.ai.
The malware’s persistence mechanism involves creating registry entries that execute with various command-line arguments, including --install, --enableupdate, --fullupdate, and others.
When the --fullupdate argument is triggered, the software downloads and executes an obfuscated JavaScript file containing the core TamperedChef payload.
Data Theft Capabilities
Once activated, TamperedChef demonstrates sophisticated information-stealing capabilities. The malware queries web browser databases using Windows Data Protection API (DPAPI) to extract stored credentials and sensitive information.
It systematically terminates browser processes to access locked data files, ensuring comprehensive data harvesting from popular web browsers, Truesec said.
The malware also conducts system reconnaissance, identifying installed security products before proceeding with its data exfiltration operations. This behavior suggests the threat actors have invested significant effort in developing evasion techniques to bypass common security solutions.
The campaign’s legitimacy facade is reinforced through the abuse of digital certificates from multiple companies, including ECHO Infini SDN BHD, GLINT By J SDN. BHD, and SUMMIT NEXUS Holdings LLC.
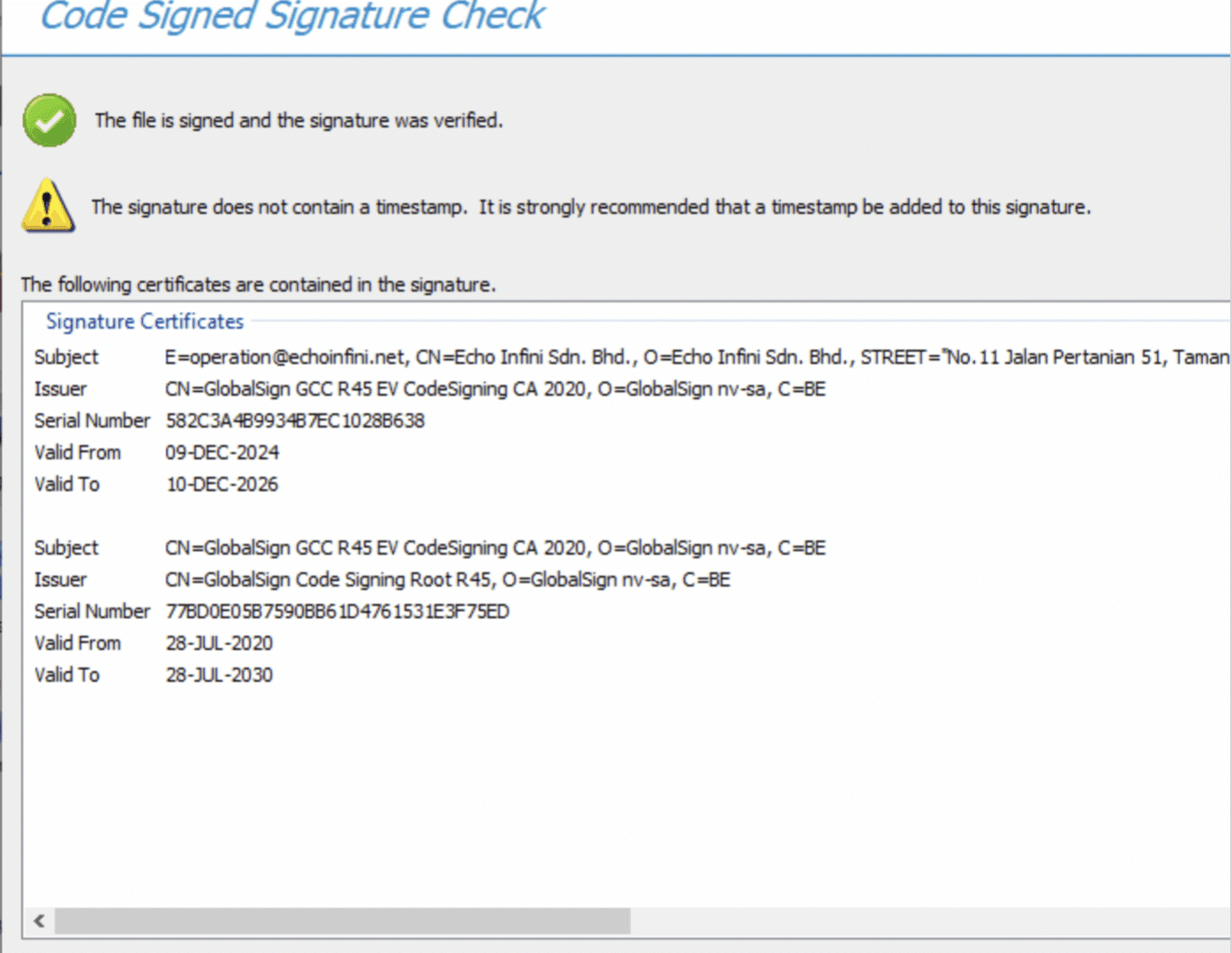
Investigation reveals these companies share suspicious characteristics, including generic websites with potentially AI-generated content and shared business addresses.
Particularly concerning is the discovery that certificates from these entities have been used to sign other malicious software, including the Epibrowser malware, indicating a broader certificate abuse operation supporting multiple malware families.
Campaign Scope and Impact
The threat actors behind TamperedChef have addressed long-term persistence in the threat landscape, with evidence suggesting activity dating back to August 2024.
For the company BYTE Media, there are also digital certificates used to sign malware, but another one called Epibrowser.
In several cases, we have observed a file called elevate.exe being installed together with the PDF Editor bundle.
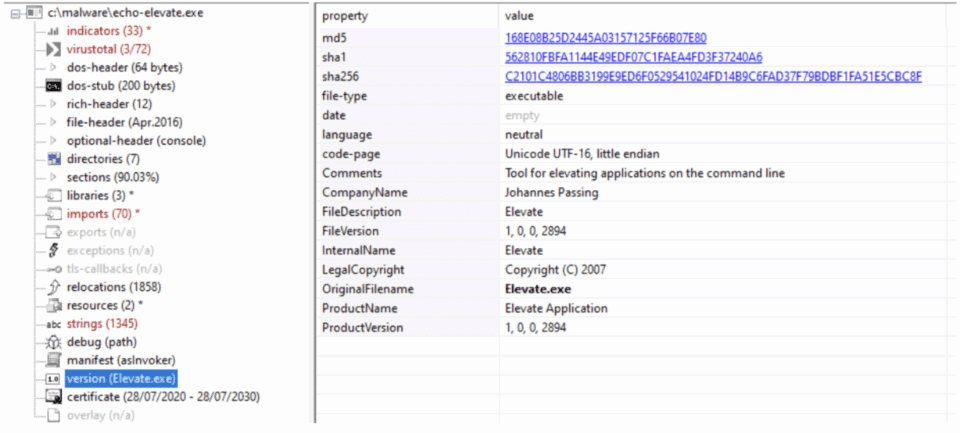
Their operations extend beyond the PDF editor to include other potentially unwanted programs like OneStart browser, all sharing common command-and-control infrastructure.
European organizations have been significantly impacted, with multiple companies reporting employee infections after downloading the malicious PDF editor.
The campaign’s success highlights the effectiveness of disguising malware as legitimate productivity tools—a category users typically trust and readily install.
This campaign represents a concerning evolution in malware distribution tactics. By leveraging legitimate advertising platforms and maintaining extended dormancy periods, threat actors can achieve widespread distribution before revealing malicious intent.
The use of AI-generated code and generic business fronts further demonstrates the industrialization of cybercrime operations.
The TamperedChef campaign serves as a stark reminder that even seemingly innocuous productivity tools can pose significant security risks. Organizations must implement robust software vetting procedures and maintain heightened awareness of free utilities from unknown sources, as today’s helpful application could become tomorrow’s security nightmare.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.
