Critical vulnerabilities in Sitecore Experience Platform allow attackers to achieve complete system compromise through a sophisticated attack chain combining HTML cache poisoning with remote code execution capabilities.
These flaws also enable attackers to enumerate cache keys and configuration details via the exposed ItemServices API, streamlining targeted exploitation.
Key Takeaways
1. CVE-2025-53693 lets attackers inject HTML via AddToCache.
2. CVE-2025-53691 abuses BinaryFormatter.Deserialize() for full code execution.
3. CVE-2025-53694 exposes cache key details, aiding targeted attacks.
Sitecore Experience Platform Vulnerabilities
The security research firm watchTowr Labs has identified three major vulnerabilities in Sitecore Experience Platform 10.4.1 that can be chained together for a devastating effect.
The primary vulnerability, CVE-2025-53693, enables HTML cache poisoning through unsafe reflection mechanisms in the XamlPageHandlerFactory handler.
The attack exploits the AjaxScriptManager.DispatchMethod() function, which uses reflection to dynamically invoke methods based on user-supplied parameters.
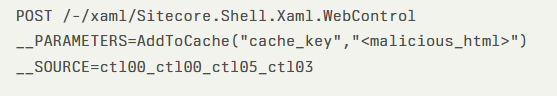
Attackers can target the vulnerable endpoint at /-/xaml/Sitecore.Shell.Xaml.WebControl with specially crafted POST requests containing malicious __PARAMETERS and __SOURCE values.
The core exploitation occurs through the AddToCache(string, string) method in Sitecore.Web.UI.WebControl, allowing attackers to inject arbitrary HTML into Sitecore’s cache system. A sample exploit request demonstrates the simplicity of the attack:
The second critical vulnerability, CVE-2025-53691, provides the pathway from cache poisoning to full remote code execution through insecure deserialization in the BinaryFormatter.Deserialize() method.
This vulnerability exists in the Sitecore.Convert.Base64ToObject() function, which processes base64-encoded objects without proper validation.
The attack chain leverages the ConvertToRuntimeHtml pipeline, specifically targeting iframe elements with embedded serialized payloads.
When the FixHtmlPage control processes malicious HTML containing iframe tags with id and value attributes, it triggers the vulnerable deserialization path.
Additionally, CVE-2025-53694 exposes sensitive information through the ItemServices API, enabling attackers to enumerate cache keys and system configurations.
This vulnerability allows unauthorized access to Sitecore item metadata, including caching settings and device configurations, facilitating targeted cache poisoning attacks.
| CVE | Title | Severity |
| CVE-2025-53693 | HTML Cache Poisoning | High |
| CVE-2025-53691 | Deserialization Remote Code Exec. | Critical |
| CVE-2025-53694 | ItemServices Metadata Disclosure | High |
Sitecore has released patches for these vulnerabilities in June and July 2025.
Organizations using Sitecore Experience Platform should immediately apply the available security updates and review their ItemServices API exposure to prevent exploitation of these critical security flaws that affect thousands of enterprise installations worldwide.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
