A critical security vulnerability has emerged in Azure Active Directory (Azure AD) configurations that exposes sensitive application credentials, providing attackers with unprecedented access to cloud environments.
This vulnerability centers around the exposure of appsettings.json files containing ClientId and ClientSecret credentials, effectively handing adversaries the keys to entire Microsoft 365 tenants.
The vulnerability was identified during recent cybersecurity assessments, where Azure AD application credentials were discovered in publicly accessible configuration files.
Key Takeaways
1. Exposed Azure AD secrets in config files allow attackers to impersonate applications.
2. Enables data theft from Microsoft 365 and malicious app deployment.
3. Bypasses security controls and can compromise entire cloud tenants.
This exposure allows threat actors to authenticate directly against Microsoft’s OAuth 2.0 endpoints, masquerading as trusted applications and gaining unauthorized access to sensitive organizational data.
Client Credentials Flow Exploit
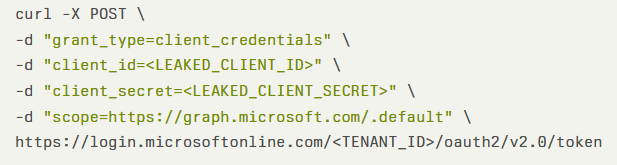
Resecurity reports that the attack vector exploits the Client Credentials Flow in OAuth 2.0, where attackers leverage exposed credentials to generate valid access tokens.
Using the leaked ClientId and ClientSecret, malicious actors can execute HTTP POST requests to Azure’s token endpoint:
Once authenticated, attackers can access the Microsoft Graph API to enumerate users, groups, and directory roles.
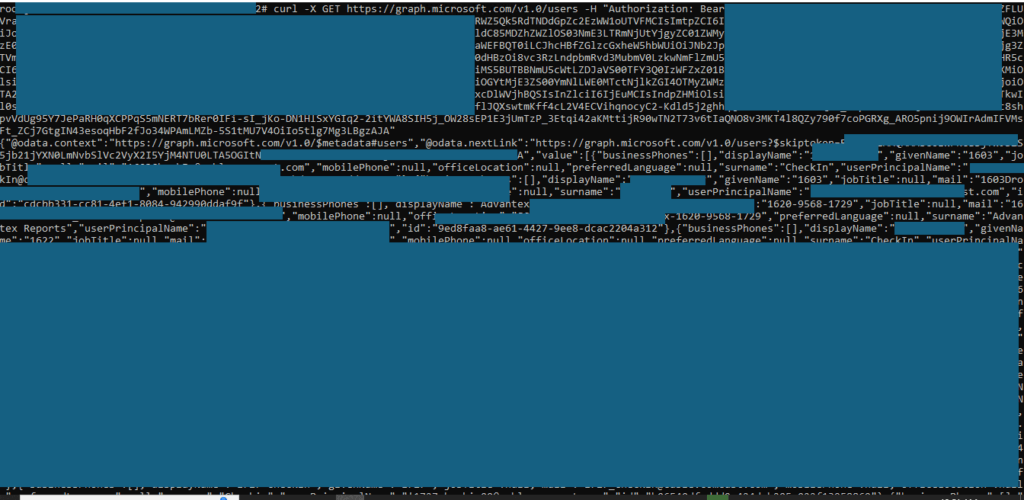
The vulnerability becomes particularly dangerous when applications have been granted excessive permissions such as Directory.Read.All or Mail.Read, allowing comprehensive data harvesting across SharePoint, OneDrive, and Exchange Online.
The exposed appsettings.json file typically contains critical Azure AD configuration parameters including the Instance URL (https://login.microsoftonline.com/), TenantId for directory identification, RedirectUri for callback handling, and most critically, the ClientSecret that serves as the application’s authentication password.
This vulnerability enables multiple attack scenarios that pose significant risks to organizational security.
Attackers can perform comprehensive reconnaissance by querying Microsoft Graph endpoints to map organizational structures, identify high-privilege accounts, and locate sensitive data repositories, reads the report.
The ability to enumerate OAuth2PermissionGrants reveals which applications have access to what resources, providing attackers with a roadmap for further exploitation.
More concerning is the potential for application impersonation, where threat actors can deploy malicious applications under the compromised tenant.
Using the legitimate application’s identity, attackers can request additional permissions, potentially escalating from limited read access to full administrative control.
This technique bypasses traditional security controls because the requests appear to originate from trusted, pre-approved applications.
The vulnerability also enables lateral movement across cloud resources. Suppose the exposed configuration file contains additional secrets such as storage account keys or database connection strings. In that case, attackers can directly access production data, modify critical business information, or establish persistent backdoors within the cloud infrastructure.
Organizations face severe compliance implications, as unauthorized access to user data can trigger GDPR, HIPAA, or SOX violations.
This Azure AD vulnerability underscores the critical importance of proper secrets management in cloud environments.
Organizations must immediately audit their configuration files, implement secure credential storage solutions like Azure Key Vault, and establish monitoring for suspicious authentication patterns.
The consequences of exposed application credentials extend far beyond simple data breaches, potentially compromising entire cloud ecosystems and enabling sophisticated, long-term attacks that can remain undetected for months.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
