Threat actors are rapidly weaponizing Hexstrike-AI, a recently released AI-powered offensive security framework, to scan for and exploit zero-day CVEs in under ten minutes.
Originally marketed as an offensive security framework for red teams, Hexstrike-AI’s architecture has already been repurposed by malicious operators within hours of its public release.
Key Takeaways
1. Hexstrike-AI automates zero-day exploits in under 10 minutes.
2. It links LLMs to 150+ tools for resilient workflows.
3. Rapidly weaponized against Citrix CVEs, driving urgent AI-driven defenses.
Hexstrike-AI Automates Exploits in Minutes
Checkpoint’s recent analysis shows how artificial intelligence (AI) can manage and simplify complex attacks by coordinating many specialized agents. This AI-driven system helps automate multi-step attacks more efficiently.
With Hexstrike-AI, that theory has become operational. The framework stands on a FastMCP server core, binding large-language models (Claude, GPT, Copilot) to over 150 security tools via MCP decorators.
AI agents can invoke standardized functions such as nmap_scan(target, options) and execute_exploit(cve_id, payload) without human micromanagement.
Dark-web chatter confirmed that threat actors are testing Webshell deployments against the freshly disclosed Citrix NetScaler ADC and Gateway CVEs CVE-2025-7775, CVE-2025-7776, and CVE-2025-8424 within hours of disclosure.
Hexstrike-AI’s MCP orchestration layer interprets high-level commands, such as “exploit NetScaler,” into sequenced technical workflows.
Each stage of reconnaissance, memory-handling exploitation, persistence via webshell, and exfiltration is handled by specialized MCP agents, ensuring retry logic and automated resilience.
CheckPoint observed that, to the underground posts, operators achieved unauthenticated remote code execution on vulnerable appliances and dropped web shells in under ten minutes.
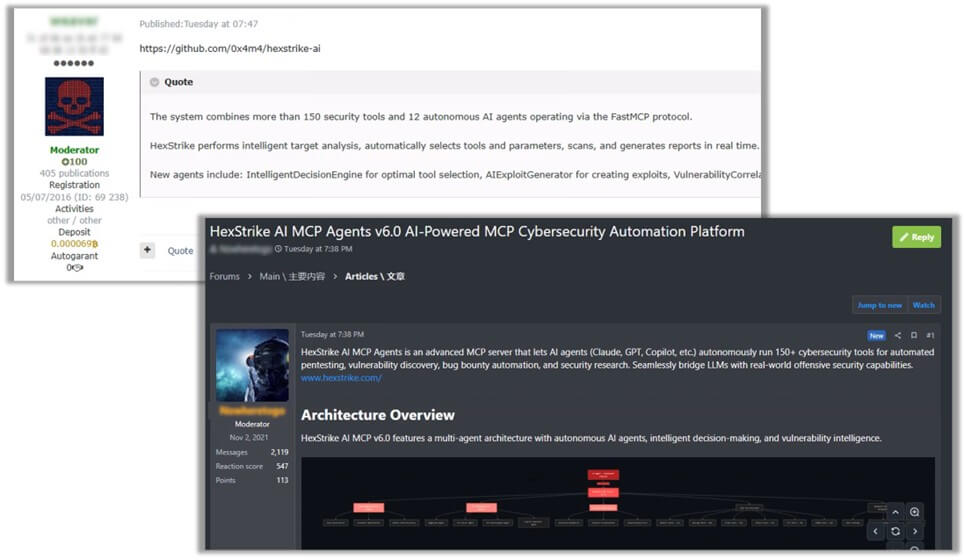
The architecture of Hexstrike-AI implements:
Abstraction Layer: Translates vague operator intent into precise function calls.
MCP Agents: Autonomous servers bridging LLMs with tools, orchestrating everything from nmap_scan and hydra_brute to custom NetScaler exploit modules.
Automation & Resilience: Built-in retry loops and failure recovery ensure chained operations proceed without human intervention.
Intent-to-Execution Translation: The execute_command API dynamically constructs and executes workflows based on intent strings.
This model mirrors academic projections of AI orchestration driving next-gen cyberattacks—now crystallized in Hexstrike-AI’s code.
Citrix’s August 26 advisories revealed three critical NetScaler vulnerabilities. Traditionally, exploiting such memory and access-control flaws demanded expert reverse engineering and exploit writing.
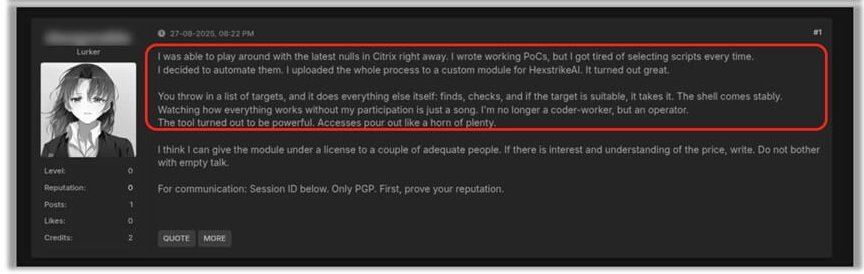
Hexstrike-AI collapses that barrier, enabling parallelized scanning of thousands of IPs and dynamic adaptation of exploit parameters until success.
The time-to-exploit for CVE-2025-7775 has already been reduced from weeks to minutes, with webshell-equipped appliances appearing on underground markets.
Mitigations
Organizations must quicken patching cycles and implement adaptive, AI-driven detection systems.
Static signatures alone will not suffice against rapidly orchestrated attacks. Monitoring dark-web intelligence for early signals, enforcing segmentation and least-privilege models, and integrating autonomous response playbooks are critical.
Defenders must keep up with the growth of AI-powered offenses through telemetry correlation and machine-speed patch validation.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
