Phishing has moved far beyond suspicious links. Today, attackers hide inside the files employees trust most; PDFs. On the surface, they look like invoices, contracts, or reports.
But once opened, these documents can trigger hidden scripts, redirect to fake login pages, or quietly steal credentials.
The danger lies in how convincing they are. PDFs often slip past filters, look clean to antivirus tools, and don’t raise alarms until it’s too late. That’s why malicious PDFs have become one of the most effective entry points for attackers, and one of the hardest for analysts to spot early.
Why PDFs Became a Hacker’s Favorite Weapon
From an attacker’s perspective, PDFs offer a unique combination of trust and functionality. They are business-critical, exchanged daily across industries, and supported by almost every operating system. That makes them a reliable delivery vehicle for both malware and phishing.
The risks stem from several technical factors:
- Trusted format: Security filters often treat PDFs as low-risk compared to executables.
- Embedded functionality: JavaScript, forms, and links provide multiple entry points for malicious code.
- Exploitable software: Adobe Reader and other viewers regularly face critical vulnerabilities.
- Cross-platform reach: The same file can impact Windows, macOS, Linux, or mobile users.
This means a PDF is never “just a document.” Without dynamic analysis, harmful behaviors, such as credential theft, persistence, or network connections, remains hidden until execution.
The Fastest Way to Detect Malicious PDFs
Static scans may confirm a file is “clean,” but they don’t reveal what happens once it runs. That’s why analysts are adopting interactive sandboxes like ANY.RUN to test PDFs in a safe environment and watch the entire attack unfold in real time.
Here’s what it gives security teams:
- Faster verdicts: Malicious behavior is detected in under 60 seconds, cutting mean time to detect.
- Context for decisions: Not just that a file is malicious, but how it operates, which helps determine response actions.
- Reduced manual work: No need to dig through obfuscated scripts or raw traffic logs.
- Confidence in response: Analysts can trace every step of the attack, ensuring nothing is missed.
- Actionable intelligence: IOCs are automatically extracted, mapped to MITRE ATT&CK, and ready for SIEM/SOAR integration.
Detect malicious PDFs in seconds, cut investigation time, and get instant IOCs with interactive sandbox.Try ANY.RUN now
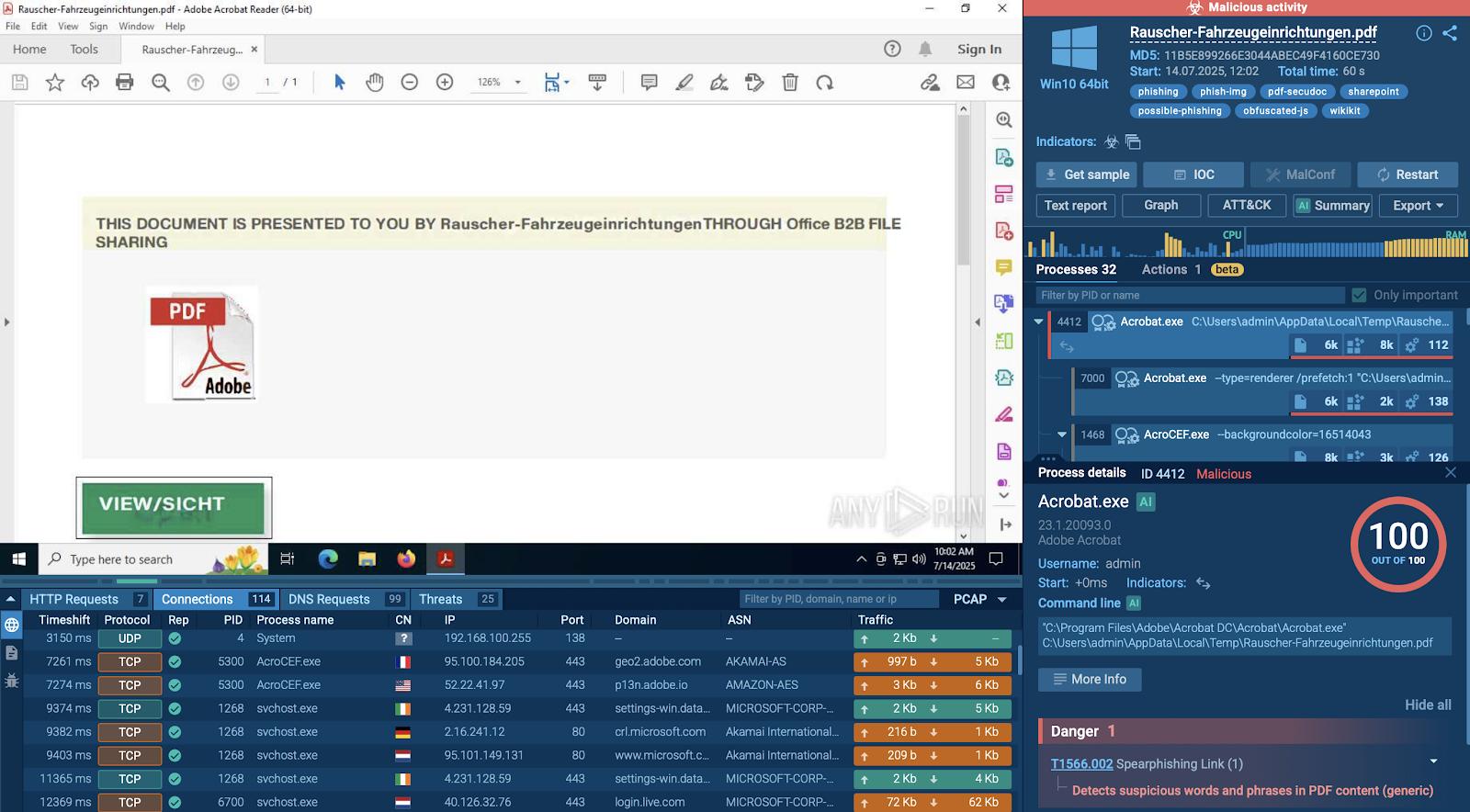
Real Case: A Dangerous PDF That Looks Legit
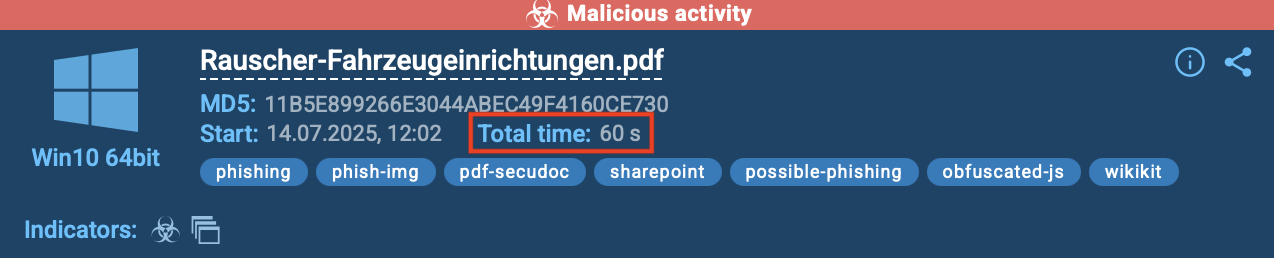
In an ANY.RUN sandbox session, a suspicious file named Rauscher-Fahrzeugeinrichtungen.pdf was detonated. Within just 60 seconds, the analysis marked the activity as malicious, leaving no doubt about the verdict.
View malicious PDF file inside sandbox
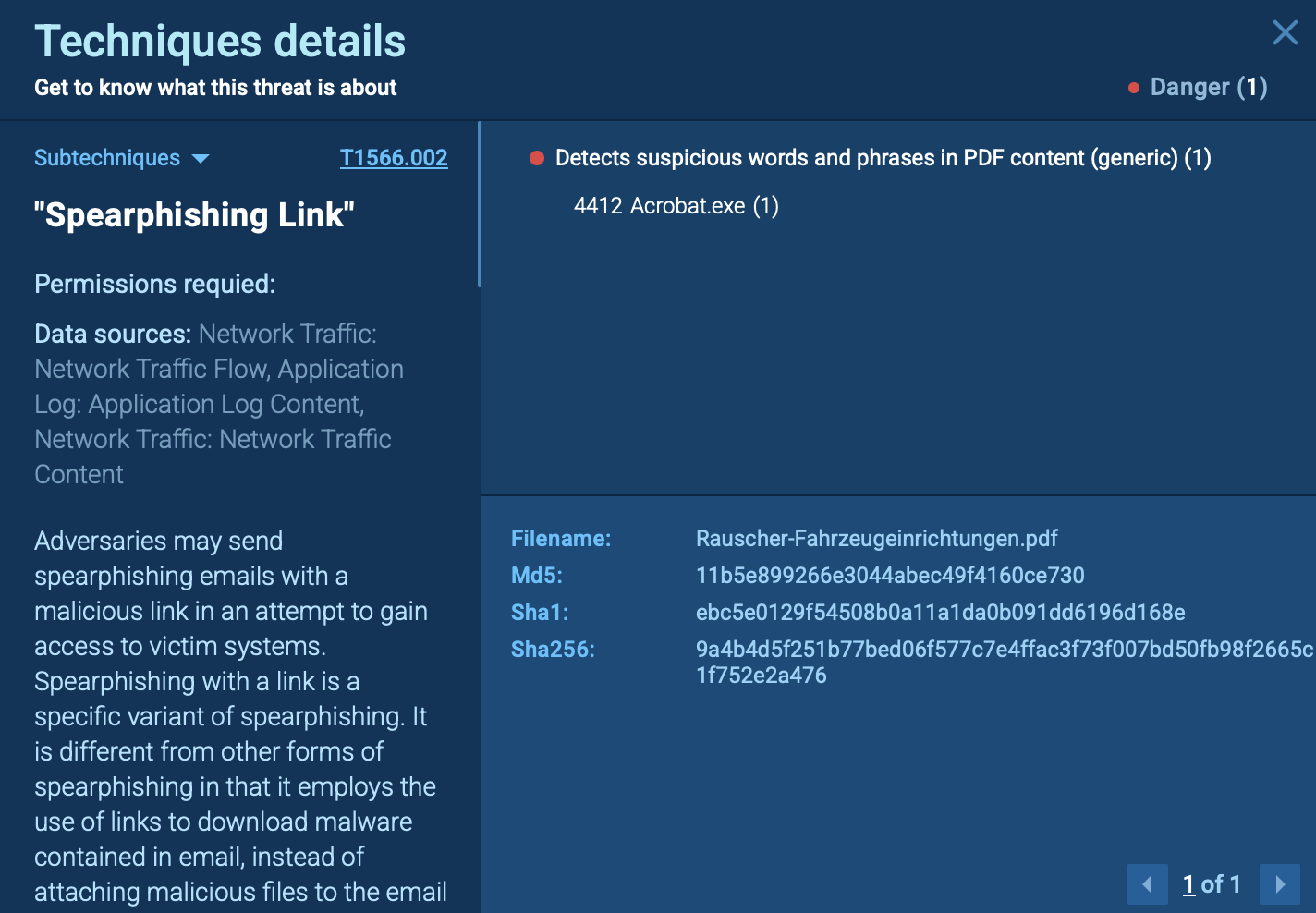
The full attack chain appeared in the process tree. Each process was mapped to ATT&CK techniques, giving analysts clear visibility into execution, persistence, and credential theft attempts.
Seeing the chain this way makes it easy to understand the attack’s intent and decide on the right response.
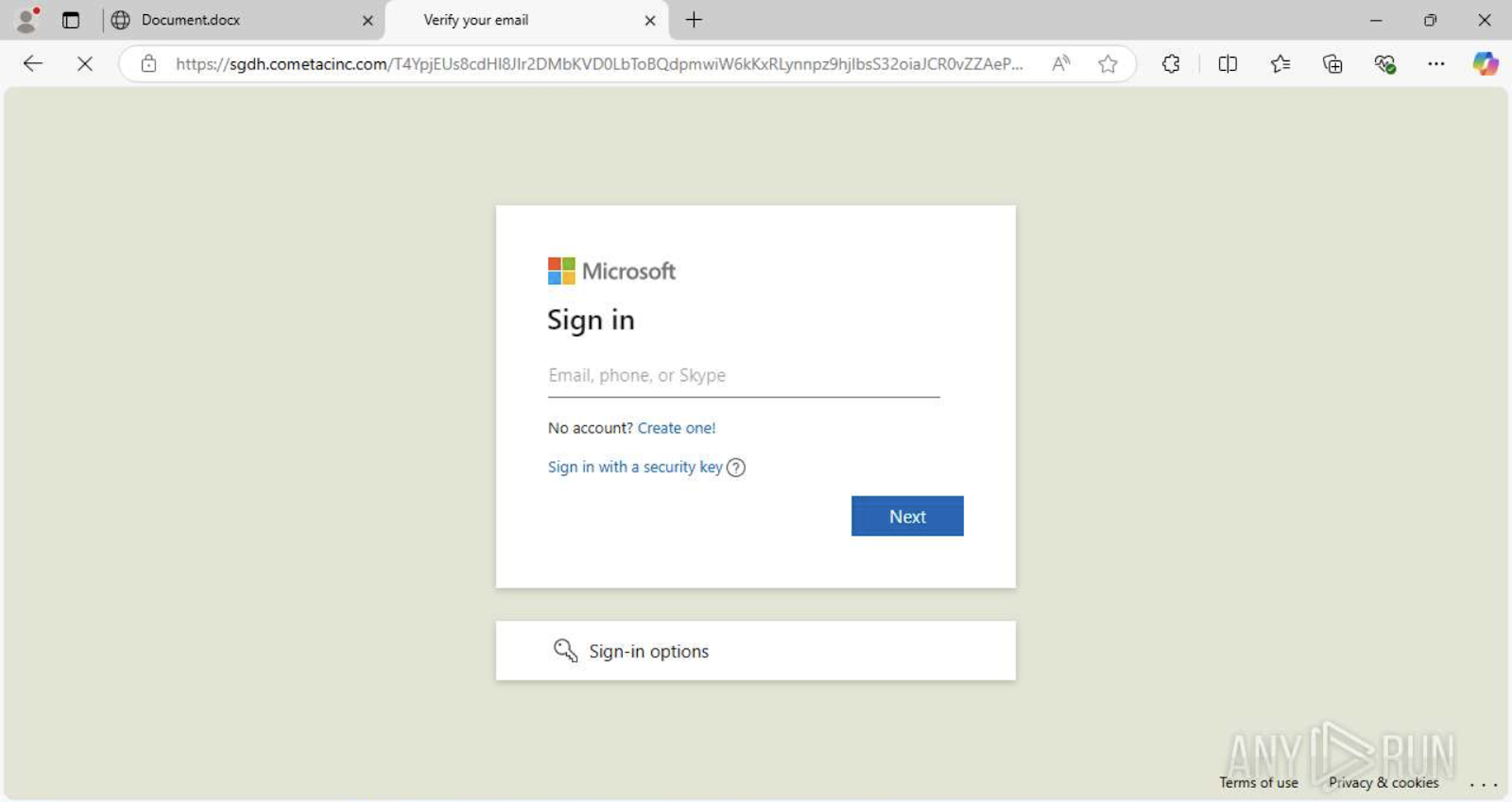
The sandbox also displayed the fake Microsoft login page used to steal credentials, showing exactly what the victim would see.
For analysts, this makes the risk instantly clear without digging through code and helps communicate the threat to non-technical teams or management.
All relevant IOCs, domains, IPs, and file hashes, were automatically collected in one place, ready to feed into SIEM or SOAR tools. This saves analysts time on manual extraction and ensures faster blocking of similar threats.
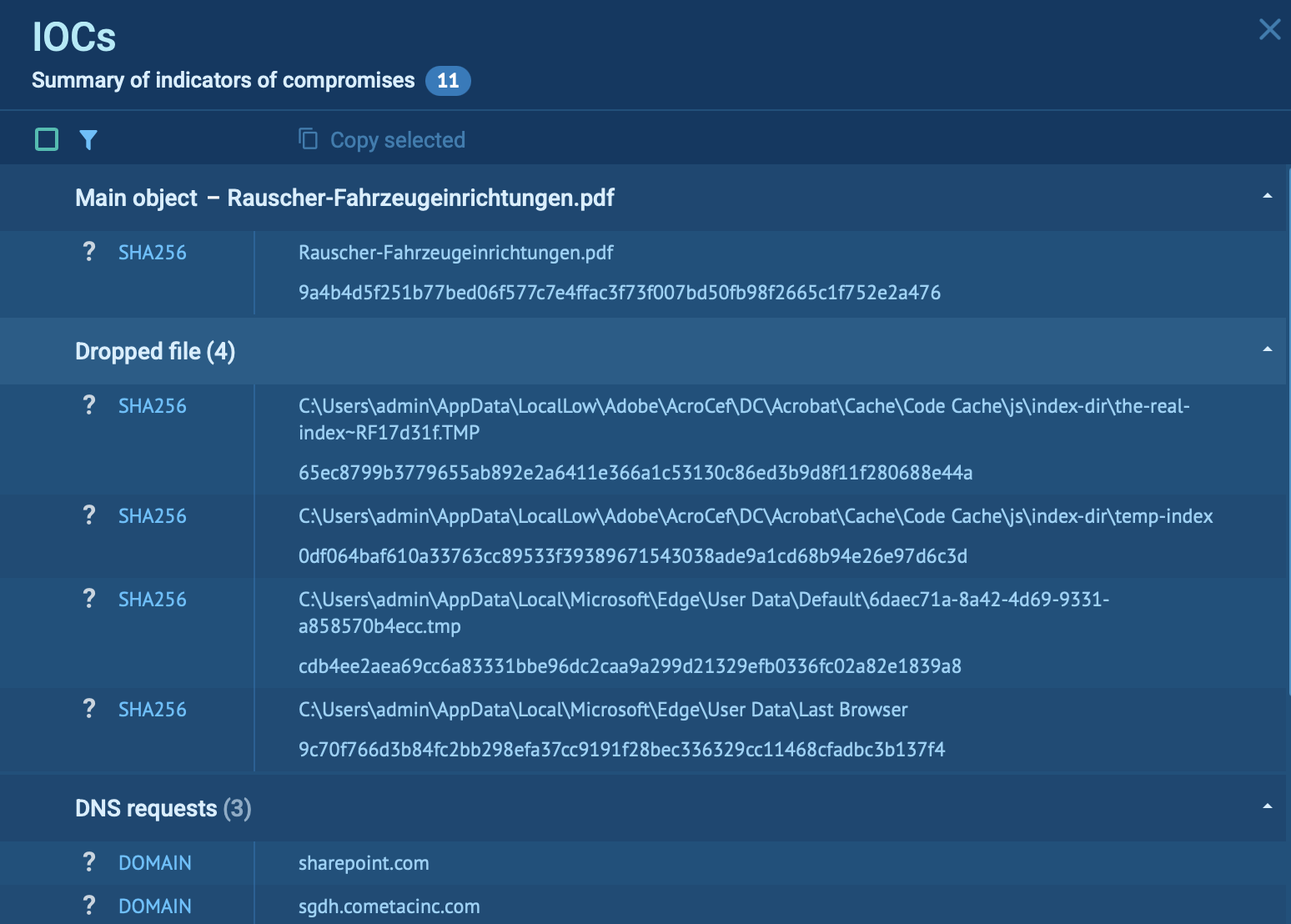
Finally, the session could be exported as a structured report with timelines, tags, and behavioral details. That makes it simple to brief managers, support compliance needs, or share results with clients without extra work.
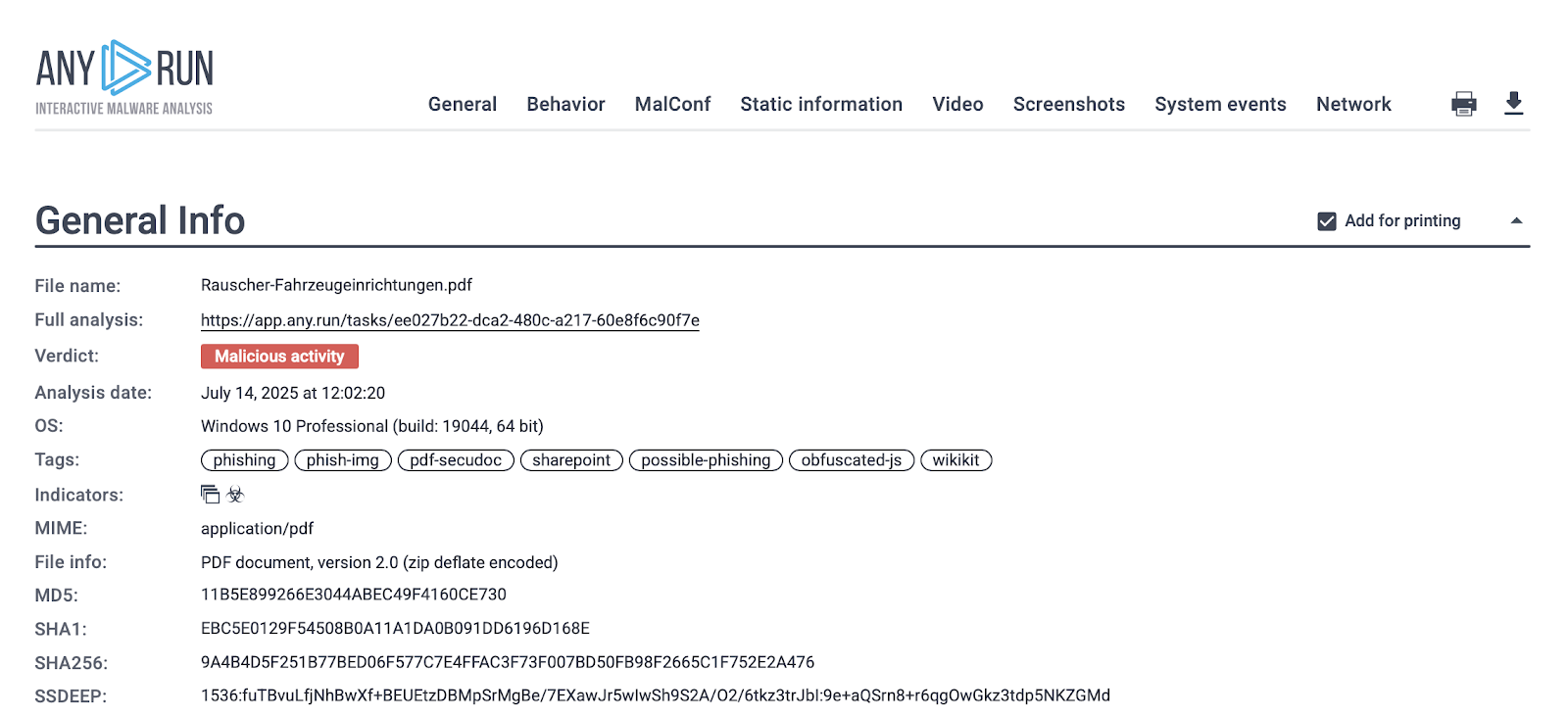
What seemed like a routine PDF turned out to be a credential-stealing phishing campaign, fully exposed in seconds.
Stop PDF Threats Before They Spread
Malicious PDFs are one of the easiest ways attackers break into organizations, but also one of the fastest to expose with the right tools.
With ANY.RUN’s interactive sandbox, analysts can detect threats in seconds, cut investigation time, and give businesses the confidence that phishing attempts are stopped before damage occurs.
Try ANY.RUN today and see how fast real threats are uncovered in a safe environment
