A previously unseen malware campaign began circulating in early August 2025, through email attachments and web downloads, targeting users in Colombia and beyond.
By leveraging two distinct vector-based file formats—Adobe Flash SWF and Scalable Vector Graphics (SVG)—the attackers crafted a multiphase operation that evaded traditional antivirus detection.
Initial reports surfaced when a benign-looking SWF file named Sequester.swf triggered alerts in only a handful of antivirus engines, prompting deeper investigation.
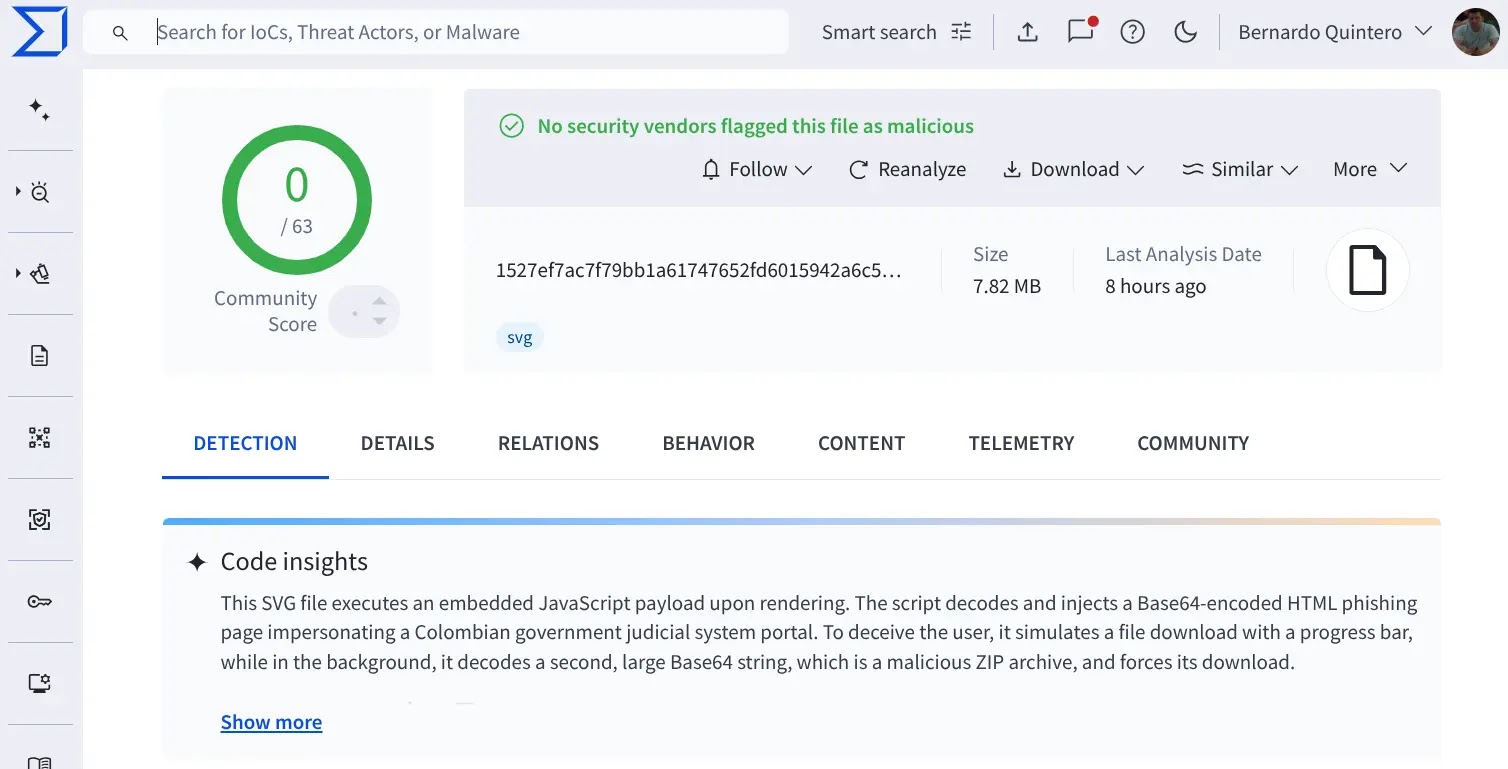
Within days, a companion SVG file emerged, embedding sophisticated JavaScript payloads designed to impersonate the Colombian Fiscalía General de la Nación portal.
The seamless pivot between legacy and modern formats caught many security teams off guard.
The SWF component masqueraded as a legitimate 3D puzzle game, complete with ActionScript modules for rendering, pathfinding, and cryptographic routines.
While antivirus engines flagged obfuscated classes and AES routines, they failed to recognize that this code served legitimate game mechanics rather than malicious behavior.
.webp)
Meanwhile, the SVG variant contained inline JavaScript that decoded a Base64 phishing page and silently dropped a ZIP archive containing additional payloads.
The combination of these two vectors created a multiheaded threat that slipped past detection barriers with alarming ease.
VirusTotal analysts noted that upon expanding support for SWF and SVG analysis in Code Insight, they were able to uncover dozens of related samples within hours of the initial submissions.
By searching for Spanish-language comments left by the attackers—strings such as "POLIFORMISMO_MASIVO_SEGURO" and "Funciones dummy MASIVAS"—researchers identified a cohesive campaign spanning more than 40 unique SVG files, none of which had raised flags in standard antivirus scans.
The early presence of these markers allowed rapid signature creation and retrohunt jobs, yielding over 500 matches when applied to submissions from the previous year.
The heart of the operation lay in its evasion tactics. By distributing large, obfuscated SWF files that blended game code with encryption routines, the attackers exploited heuristic thresholds.
At the same time, the SVG files embedded encrypted JavaScript in CDATA sections, evading simple pattern matching.
.webp)
When rendered in a browser, the script would decode and inject an HTML phishing interface, complete with progress bars and authentic-looking forms that mimicked official government communications .
Detection Evasion Techniques
Central to this campaign’s success was the layering of obfuscation and polymorphism. Each SWF sample employed variable renaming, garbage code insertion, and custom packing routines to defeat static analysis.
The following excerpt illustrates how the SVG payload concealed its primary logic within nested Base64 strings:-
// POLIFORMISMO_MASIVO_SEGURO: 2025-09-01T16:39:16.808557
var payload = atob("UE...VUM+Cg==");
document. Write(payload);Meanwhile, the YARA rule crafted by VirusTotal researchers targeted the consistent Spanish comments:-
rule svg_colombian_campaign {
strings:
$c1 = "Funciones dummy MASIVAS"
$c2 = "POLIFORMISMO_MASIVO_SEGURO"
condition:
uint16(0) == 0x3C3F and any of ($c*)
}This rule achieved over 523 detections when retrohunted against a year’s worth of submissions.
By combining heuristic bypasses, encrypted payloads, and intentional misdirection, the attackers demonstrated a refined understanding of both legacy and modern file formats—underscoring the urgent need for context-aware analysis in contemporary threat defense.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.
