A marked escalation in the abuse of ConnectWise ScreenConnect installers since March 2025, with U.S.-based businesses bearing the brunt of these incursions.
Adversaries are now deploying lightweight ClickOnce runner installers—devoid of embedded configurations—to evade static detection, fetching malicious components at runtime.
Post-installation, attackers automate the rapid deployment of two distinct remote access trojans (RATs): the publicly available AsyncRAT and a bespoke PowerShell-based RAT.
Within weeks, the campaign evolves further, leveraging batch and VBS loaders to deliver encoded .NET assemblies.
Distribution relies heavily on phishing lures masquerading as financial or official documents, while the reuse of preconfigured Windows Server 2022 VMs accelerates infrastructure rotation.
Defenders should rigorously monitor RMM tool usage and scrutinize all ScreenConnect deployments
Over recent months, Acronis TRU (Threat Research Unit) has documented a tracked multiple coordinated campaigns exploiting trojanized ConnectWise ScreenConnect installers to infiltrate corporate networks.
The attack is likely to have originated with a social engineering campaign, likely distributed via email phishing, but possibly through other means as well.
Although ScreenConnect abuse is not new, the current wave introduces significant refinements—most notably the shift to ClickOnce runner installers, which download their payloads dynamically, sidestepping signature-based defenses.
Once executed, these installers grant adversaries unfettered remote control, facilitating data exfiltration, lateral movement, and sustained persistence.
Evasive ClickOnce Installers
The breach chain commences with a malicious ClickOnce installer—often named to mimic genuine documents (e.g., agreement_support-pdf.Client.exe)—delivered through phishing emails.
Upon execution, this runner installer fetches ScreenConnect.ClientSetup.exe from attacker-controlled servers (e.g., morco.rovider[.]net) and establishes a connection to the adversary’s on-premises ScreenConnect instance.
Unlike prior attacks that embedded server details, this new method downloads configuration at runtime, rendering static detection checks ineffective.
The only dependable countermeasures include blacklisting known malicious domains—difficult to preconfigure—or outright blocking ScreenConnect installations.
Immediately following ScreenConnect installation, adversaries exploit its automation features to launch two RATs concurrently:
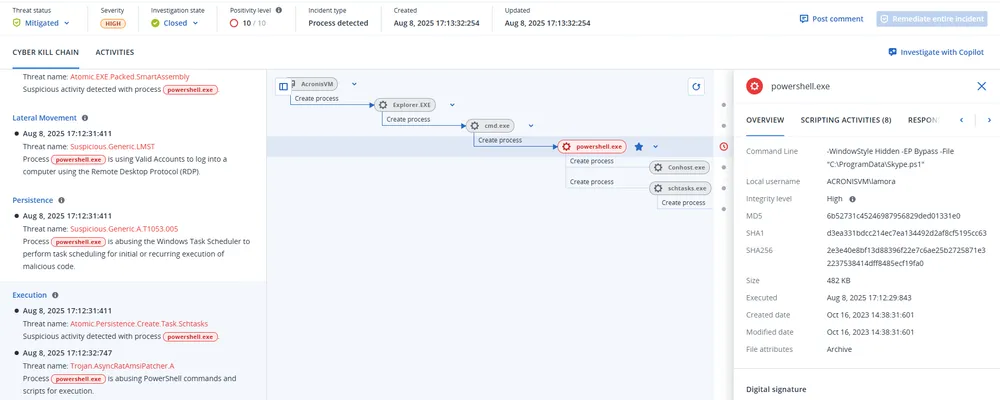
- AsyncRAT Deployment
A batch script (BypaasaUpdate.bat) drops and extracts AsyncRAT (1.txt) alongside an AMSI bypass and persistence stub (pe.txt). A PowerShell loader (Skype.ps1) dynamically loads both assemblies in memory, while a scheduled VBS task perpetuates execution every minute. AsyncRAT’s internal mutex prevents redundant instances. - Custom PowerShell RAT
Seconds later, a JavaScript-named script deploys a homemade PowerShell RAT. This tool disables AMSI, collects host reconnaissance (antivirus products, OS details, UUID), and exfiltrates data via Microsoft.XMLHTTP. A three-second polling loop processes commands—such as file download/execution, script injection, and persistence setup via VBS—using obfuscated code and randomized names to hinder analysis.
The concurrent RATs may reflect redundancy planning, tool testing, or a shared infrastructure sold to multiple operators.

Approximately two weeks post-compromise, attackers pivot to batch and VBS loaders that retrieve and execute encoded .NET assemblies (logs.ldr and logs.ldk).
An Obfuscator.dll loader decodes these assemblies in memory, establishing persistence via a “Skype Updater” scheduled task. The updated AsyncRAT communicates on new ports (4501–4503) under a fresh mutex string, while the core C2 IP remains constant.
Days later, a third RAT—PureHVNC—is delivered through WMI-driven PowerShell commands. A startup-folder VBS wrapper invokes a loader that process-hollows RegAsm.exe, injecting the PureHVNC payload, which connects to a separate C2 endpoint (169.156.208.185:8020).
Social Engineering and Infrastructure
Malicious executables masquerade as Social Security statements or business documents (e.g., Social_Security_Statement_Documents_386267.exe), underscoring heavy reliance on phishing.
Attackers deploy preconfigured Windows Server 2022 VMs—identifiable by hostnames like WIN-BUNS25TD77J and COPY-OF-VM-2022—allowing swift redeployment across campaigns.
Organizations must treat RMM software as high-risk attack vectors. Recommended measures include:
- Implementing granular allow-listing for ScreenConnect executables and blocking unauthorized ClickOnce installations.
- Continuously monitoring outgoing connections for anomalous ScreenConnect server addresses.
- Auditing scheduled tasks, startup items, and PowerShell script execution logs for persistence artifacts.
- Educating employees to recognize phishing lures disguised as financial or legal documents.
By integrating these controls, security teams can detect malicious RMM activity earlier and disrupt adversaries’ ability to leverage ScreenConnect for initial access.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.
