Continuous Vulnerability Management: The New Cybersecurity Imperative
Security leaders are drowning in data but starving for actionable insights. Traditional penetration testing has become a snapshot of vulnerability that expires faster than milk in a hot car. What if there was a way to transform cybersecurity from a reactive cost center to a proactive business enabler?
Enter the world of continuous penetration testing – a revolutionary approach that’s rewriting the rules of enterprise security.
CJ McLaren, founder and CEO of Xcape, understands this challenge intimately. His company has developed a methodology that goes beyond point-in-time assessments, creating a dynamic, ongoing security partnership with organizations.
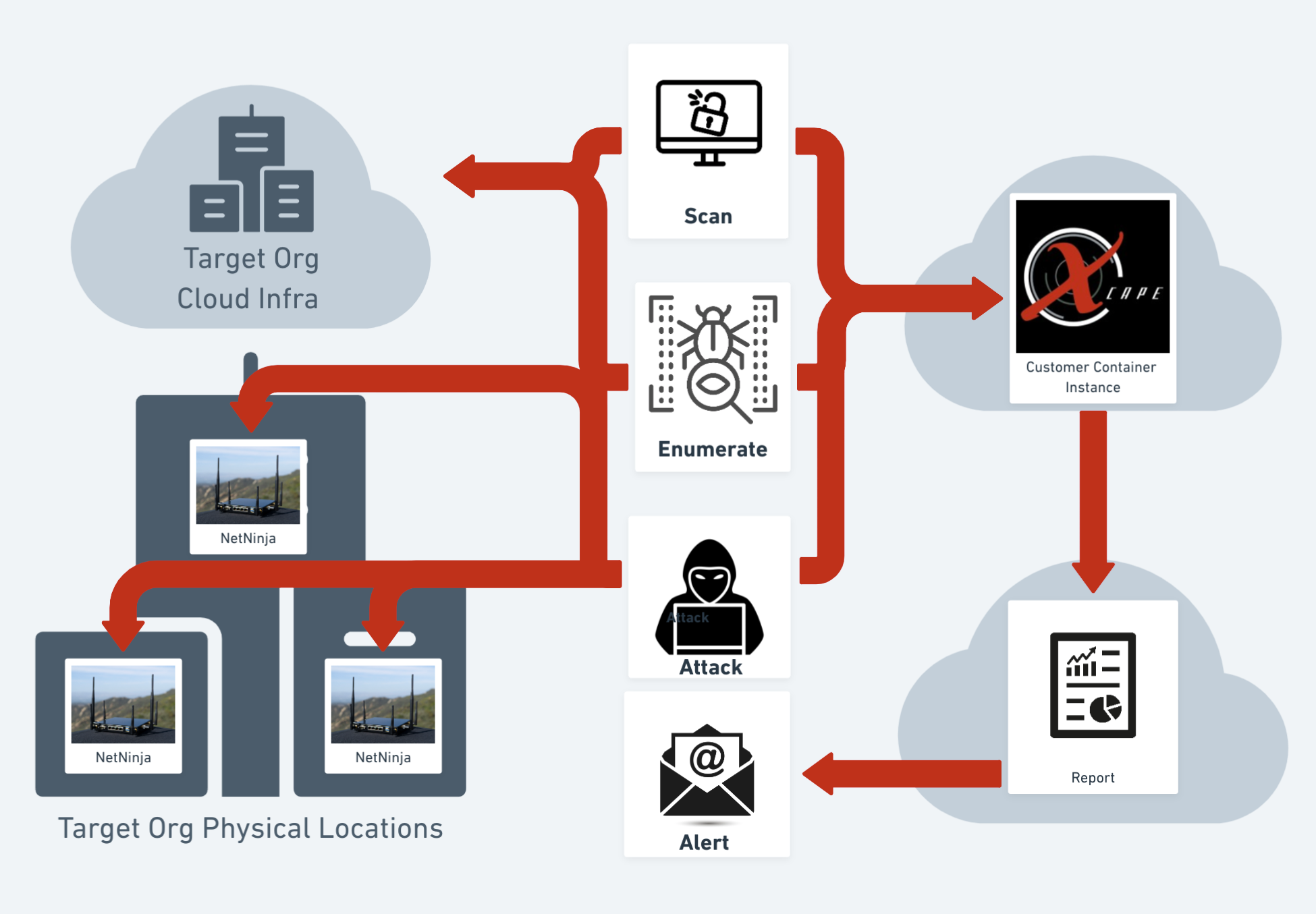
“The problem with traditional pen testing is how arduous and manual it becomes,” McLaren explains. “If you have multiple endpoints, scanning and enumeration can consume enormous resources before you even reach vulnerability assessment.”
The Traditional Vulnerability Landscape
Most security teams recognize the fundamental problem: infrastructure changes constantly. Cloud migrations, digital transformations, and rapid technological evolution mean that a security assessment completed today might be irrelevant tomorrow.
McLaren breaks down the core challenges:
“Companies run ephemeral infrastructure that changes multiple times per day. If you’re not testing at high enough intervals, you’re missing critical deployment windows and potential access points.”
The mathematics are stark. Many organizations face hundreds of potential remediation tickets after a traditional assessment. Development teams become overwhelmed, creating a backlog that grows faster than it can be addressed.
Continuous Testing: A Paradigm Shift
The solution isn’t more manual labor – it’s intelligent automation. Xcape’s approach leverages continuous scanning and intelligent threat modeling to provide real-time insights.
“Why haven’t we figured out how to automate the hard parts?” McLaren provocatively asks. “As computer scientists, we should make machines work for us.”
This isn’t just technical bravado. It’s a fundamental reimagining of security assessment. By running scans at staggered times and continuously probing infrastructure, organizations can develop a living, breathing understanding of their threat landscape.
Damon Small, a board member at Xcape, adds critical perspective:
“Vulnerability scanning technology has existed since the early 1990s. As an industry, we apparently haven’t learned much in that time.”
The Human Element of Security
Despite advanced automation, human expertise remains crucial. Xcape’s model ensures that technical experts spend more time developing sophisticated exploits and understanding complex attack vectors.
“Our team spends entire engagement periods poking at infrastructure and developing exploits,” McLaren notes. “We understand that real attackers might spend nine to twelve months understanding a system before executing an attack.”
This patient, methodical approach mirrors actual threat actor behaviors – a critical distinction from traditional assessment models.
Economic Implications of Continuous Testing
Security is no longer just a technical discipline – it’s a business strategy. By quantifying vulnerabilities and providing continuous insights, organizations can make more informed risk decisions.
Small emphasizes the economic perspective:
“Information assets have actual value. We help businesses make more informed decisions about protecting their digital crown jewels.”
Translating Technical Complexity
One persistent challenge remains: how do technical teams communicate complex security concepts to non-technical executives?
McLaren’s approach is refreshingly direct. “I focus on understanding what keeps executives up at night. By connecting technical findings to business outcomes, we transform security from a cost center to a revenue driver.”
This translation requires multilingual expertise – the ability to speak both technical and business languages fluently.
Call to Action for CISOs
Security leaders cannot afford complacency. The threat landscape evolves continuously, and your assessment methodology must match that dynamism.
Consider these immediate steps:
- Evaluate your current vulnerability management approach
- Explore continuous testing methodologies
- Develop metrics that connect security investments to business outcomes
- Foster a culture of continuous improvement
The Future of Security Testing
Continuous vulnerability management isn’t just a technological upgrade – it’s a strategic transformation. By embracing intelligent, automated, and persistent testing, organizations can stay ahead of emerging threats.
Learn more at: https://xcapeinc.com/
Author’s Note:
This exclusive interview was conducted live at the 2025 Black Hat Conference in Las Vegas, providing unprecedented insights into the future of cybersecurity assessment.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.
