Microsoft has announced that the Windows Management Instrumentation Command-line (WMIC) tool will be removed after upgrading to Windows 11 25H2 and later.
WMIC is a legacy built-in Windows command-line tool that allows users to interact with the Windows Management Instrumentation (WMI) system using text commands.
In a Microsoft 365 message center update, Microsoft now advises IT administrators to switch to Windows PowerShell for WMI, scripts, and other tools because later Windows releases will no longer include WMIC by default.
“Microsoft recommends using PowerShell and other modern tools for any tasks previously done with WMIC. You can consider programmatic alternatives such as WMI’s COM API, .NET libraries, or scripting languages. Once you decide on your way forward, please update your internal IT documentation and processes,” the company said.
However, this change only applies to the outdated WMIC component, as the Windows Management Instrumentation (WMI) itself remains unaffected.
Further guidance for those who use WMIC for administrative tasks is available in this separate support document published by Microsoft on Friday.
Microsoft deprecated WMIC in Windows Server 2012 (in 2016) and in Windows 10 21H1 (2021). Redmond converted it into a Feature on Demand (FoD) starting with Windows 11 22H2 (in 2022) and announced in January 2024 that it would be removed altogether after first disabling it by default.
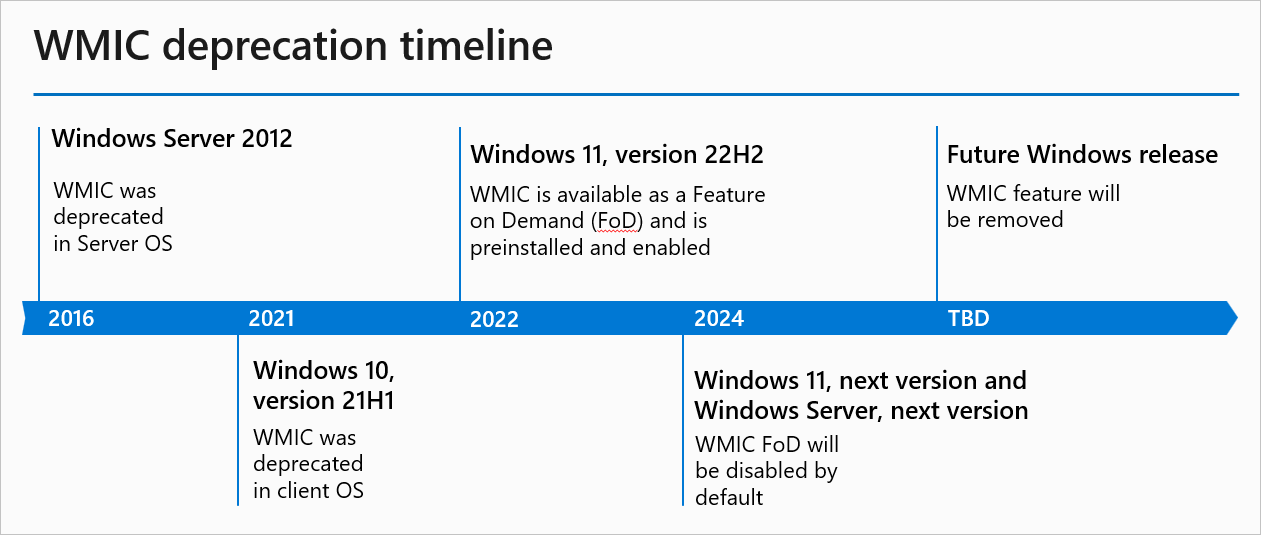
“We’ve been heavily investing in PowerShell in the past few years. The new tools provide a more efficient way of querying WMI. Removing a deprecated component helps reduce complexity while keeping you secure and productive,” Microsoft said in January 2024.
WMIC’s removal will also boost overall security by thwarting a wide range of malware and attack tactics that will no longer function correctly.
The tool has long been considered a LOLBIN (living-off-the-land binary), a Microsoft-signed executable that threat actors exploit for a wide range of malicious activities during attacks.
For instance, ransomware encryptors commonly use the WMIC command to delete Shadow Volume Copies, ensuring that victims can’t use them to recover encrypted data. Other threat actors have used WMIC to query for the list of installed antivirus software and uninstall it.
Malware has also been observed using WMIC to add exclusions to Microsoft Defender, evading detection when launched.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
