A sophisticated new ransomware operation dubbed BlackLock has emerged as a significant threat to organizations worldwide, demonstrating advanced cross-platform capabilities and targeting diverse computing environments.
Originally operating under the name “El Dorado” since March 2024, the group rebranded to BlackLock in September 2024, establishing itself as a formidable player in the ransomware landscape with victims spanning multiple countries and industries.
BlackLock’s technical sophistication lies in its development using the Go programming language, enabling the malware to execute seamlessly across Windows, Linux, and VMware ESXi systems.
This cross-platform approach significantly expands the attack surface, allowing threat actors to compromise entire IT infrastructures simultaneously.
The ransomware operates under a Ransomware-as-a-Service (RaaS) model, actively recruiting skilled affiliates through Russian-speaking cybercrime forums, particularly RAMP.

Advanced Encryption and Cross-Platform Capabilities
ASEC reports that the ransomware implements robust cryptographic techniques, utilizing Go’s crypto package to perform file encryption through ChaCha20.NewUnauthenticatedCipher() with randomly generated 32-byte FileKeys and 24-byte nonces for each targeted file.
This approach ensures that every encrypted file receives a unique encryption key, making recovery virtually impossible without the attackers’ decryption tools.
BlackLock’s sophisticated key management system employs Elliptic Curve Diffie-Hellman (ECDH) key exchange to generate shared keys for metadata encryption.
The ransomware appends encrypted metadata containing the FileKey and victim information to each file, protected by secretbox.Seal() encryption.
This dual-layer encryption strategy prevents victims from independently recovering their data while ensuring the attackers can decrypt files upon ransom payment.
The malware supports extensive command-line arguments for operational flexibility, including -path for targeted encryption, -delay for timed execution, -threads for performance optimization, and -perc for partial file encryption to accelerate the attack process.
Notably, the ransomware includes provisions for VMware ESXi environments through the -esxi option, though this feature remains unimplemented in the analyzed samples.
BlackLock demonstrates advanced network propagation capabilities by utilizing open-source projects like go-smb2 to scan and access SMB shared folders across Windows networks.
The ransomware can authenticate using plaintext passwords or NTLM hashes specified through the -u, -p, and -h parameters, enabling lateral movement across corporate networks and simultaneous encryption of networked storage systems.
To eliminate recovery options, BlackLock employs sophisticated data destruction techniques targeting Volume Shadow Copy Service (VSS) and Recycle Bin contents.
Rather than executing obvious command-line instructions, the malware constructs COM object instances to execute WMI queries through shellcode loaded directly into memory, making detection significantly more challenging for security solutions.
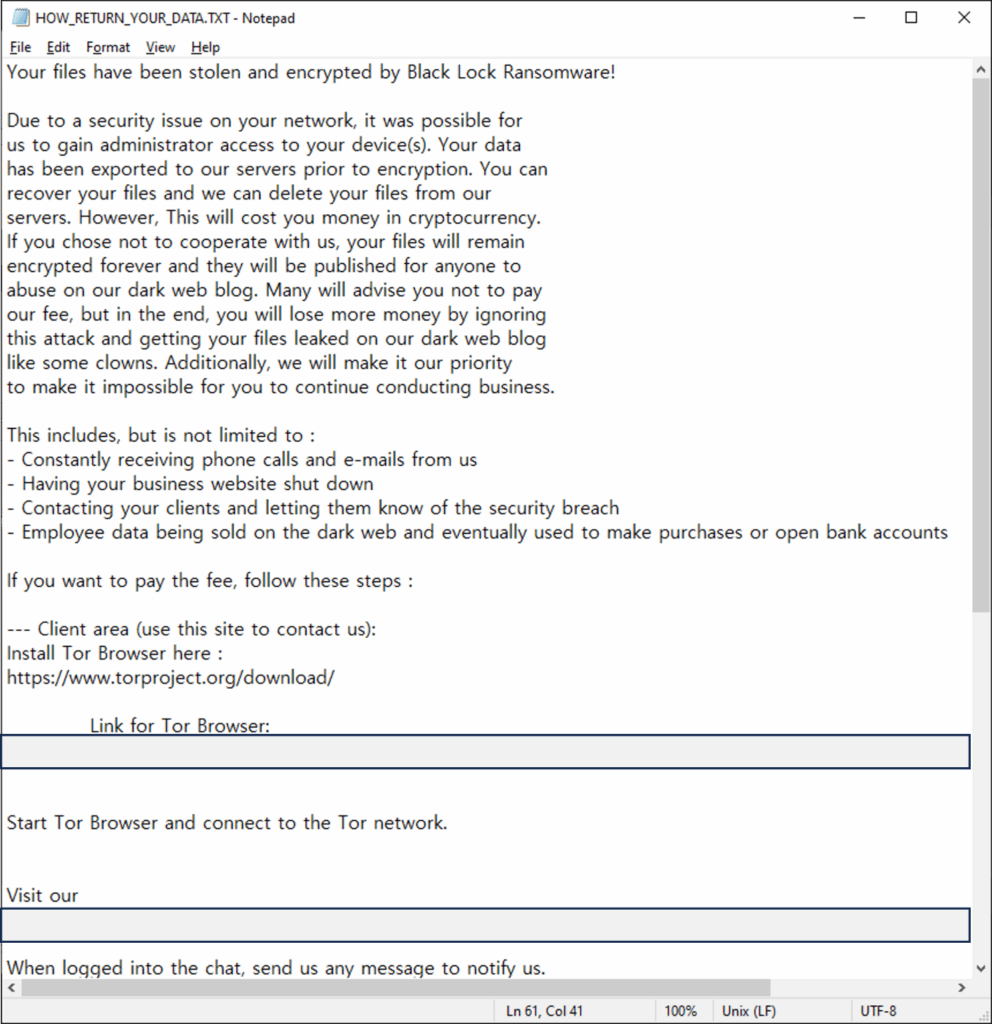
The ransomware creates ransom notes titled HOW_RETURN_YOUR_DATA.TXT in every encrypted directory, containing threatening language that warns victims of business disruption and data leakage to customers and the public if ransom demands are not met.
This psychological pressure tactic, combined with the technical impossibility of independent data recovery, creates substantial leverage for the attackers.
Organizations must implement comprehensive security strategies encompassing endpoint protection, network segmentation, and robust backup solutions to defend against this evolving threat landscape.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
