Alex sighed at his third energy drink of the night shift, watching another batch of security alerts flood his SIEM dashboard.
As a Level 2 threat analyst at a mid-sized financial firm, he was drowning in false positives and spending precious hours manually investigating each suspicious hash, IP address, and domain.
Then everything changed during one particularly brutal 3 AM investigation. While researching a suspicious executable that had triggered multiple endpoint alerts, Alex stumbled upon a threat intelligence lookup service that connected him to insights from thousands of other security operations centers.
Within seconds, the verdict was clear: sophisticated banking trojan, multiple C2 communications, credential harvesting capabilities.
What would have taken Alex two hours of painstaking analysis was resolved in under five minutes. More importantly, he had the confidence and evidence needed to escalate immediately to the incident response team. By morning, a potential breach had been contained.
Why Speed is the Key: How Faster Alert Management Transforms Analyst’s World
In the high-stakes arena of cybersecurity, speed isn’t a luxury. It’s survival. Threat actors evolve in hours, not days, and every delayed response risks escalation. But mastering alerts and artifacts at lightning speed doesn’t just fend off attacks; it supercharges your efficiency, effectiveness, KPIs, and career trajectory while safeguarding the business and nailing SOC/MSSP goals:
1. Boosts Personal Efficiency: Rapid triage means handling 2-3x more alerts per shift without the mental fog of endless rabbit holes. Solutions that deliver instant context, like Threat Intelligence Lookup, free up brainpower for creative hunting, not rote googling.
See how it works: a domain search returns an instant “Malicious” verdict, a last-seen date to evaluate a threat’s relevance, a list of additional IOCs, and a selection of sandbox analyses of malware samples featuring the domain.
domainName:”randomuser.me”
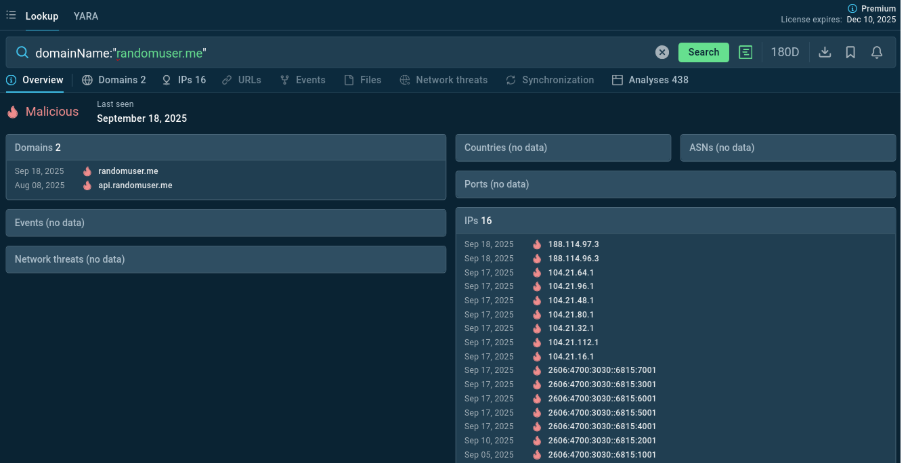
Domain lookup results with contextual data
Try TI Lookup to make quick actionable decisions on possible threats.
Just sign up to start
2. Enhances Effectiveness in Threat Hunting: Quick IOC validation uncovers hidden patterns across incidents, turning isolated pings into proactive takedowns. You’ll spot campaigns early, disrupting attackers before they burrow deep.
3. Skyrockets KPIs Like MTTR and Resolution Rates: Shave minutes off each investigation and watch metrics soar. MTTR drops by up to 10x, resolution rates climb, and alert fatigue plummets. With ANY.RUN’s TI Lookup 88% of threats are detected within 60 seconds of analysis. Happy metrics mean rave performance reviews.
4. Accelerates Career Growth: Analysts who resolve threats faster stand out. Faster validations lead to high-impact contributions, mentorship opportunities, and that senior role you’ve eyed. Speed builds reputation as the go-to expert.
5. Fortifies Business Protection: Swift artifact checks minimize dwell time, reducing breach costs. Early detection prevents data leaks, downtime, and regulatory fines, keeping the C-suite smiling.
See how it works: a quick lookup shows a strong correlation of an IP with Lumma, one of the most dangerous malware families.
destinationIP:”195.82.147.188″

IP search results: now we know that it’s a symptom of Lumma stealer in the system
6. Drives SOC Team Morale and Retention: When alerts aren’t a Sisyphean slog, burnout fades. Teams collaborate better on validated intel, fostering a culture of wins over exhaustion since this is the key for retaining top talent in a field desperate for skilled hands.
7. Achieves SOC/MSSP KPIs with Ease: Hit SLAs on response times, exceed client expectations, and scale services without ballooning headcount. Faster ops mean more billable hours and glowing testimonials, fueling business growth. 90% companies report higher threat detection rates after integrating TI Lookup.
See how it works: if your logs contain a suspicious PowerShell command, just submit it to LI Lookup.
imagePath:”powershell” AND commandLine:”$codigo”

Malware samples with steganography, with sandbox analyses showing attack chains
This search results expose malware that utilizes steganography: the practice of hiding malicious code in the source code of images or other benign objects to avoid detection.
Upgraded to the Premium plan, Threat Intelligence Lookup supports over 40 search parameters, additional search operators, and an assortment of wildcards. Comprehensive queries for deeper research become available.
Uncover TI Lookup full potential for rapid threat detection, escalation, and mitigation: choose you plan.
Speed isn’t about rushing — it’s about precision. When speed meets accuracy, both the analyst and the business win.
ANY.RUN’s Threat Intelligence Lookup: Your Window into 15,000 SOCs
The breakthrough Alex experienced wasn’t luck, it was the power of community-driven threat intelligence. ANY.RUN’s Threat Intelligence Lookup provides instant access to analysis results from over 15,000 security operations centers worldwide who use ANY.RUN’s Interactive Sandbox for malware analysis.
Every day, security professionals across the globe upload suspicious files, URLs, and other artifacts to ANY.RUN’s Interactive Sandbox for analysis. These investigations happen in real-time, creating a constantly updated database of threat intelligence from actual security incidents and investigations.
When you query an IOC through the Threat Intelligence Lookup, you’re not just getting static reputation data. You are accessing fresh insights from recent sandbox sessions where other analysts investigated the same indicators you’re seeing in your environment. When a hash shows up in your alerts, you can instantly see:
- Whether other SOCs have recently analyzed this file
- What behaviors were observed during sandbox analysis
- Network communications and C2 infrastructure
- File system modifications and persistence mechanisms
- Screenshots and process trees from actual execution
- IOCs associated with the same campaign or threat actor
Interactive sandbox sessions capture the complete attack chain, helping you understand not just what you’re dealing with, but how it operates and what additional IOCs to hunt for in your environment.
Conclusion
Validating alerts no longer has to be a slow, painful process. With threat intelligence from a global community of SOC analysts, you can turn alert overload into actionable security insights.
For threat analysts striving to excel in an ever-evolving cyber landscape, ANY.RUN’s Threat Intelligence Lookup offers an unparalleled opportunity to transform investigative efficiency and impact.
By integrating it into your workflow, you can significantly reduce mean time to respond (MTTR), enhance detection accuracy, and achieve KPIs with greater consistency, directly bolstering your professional reputation and career trajectory.
