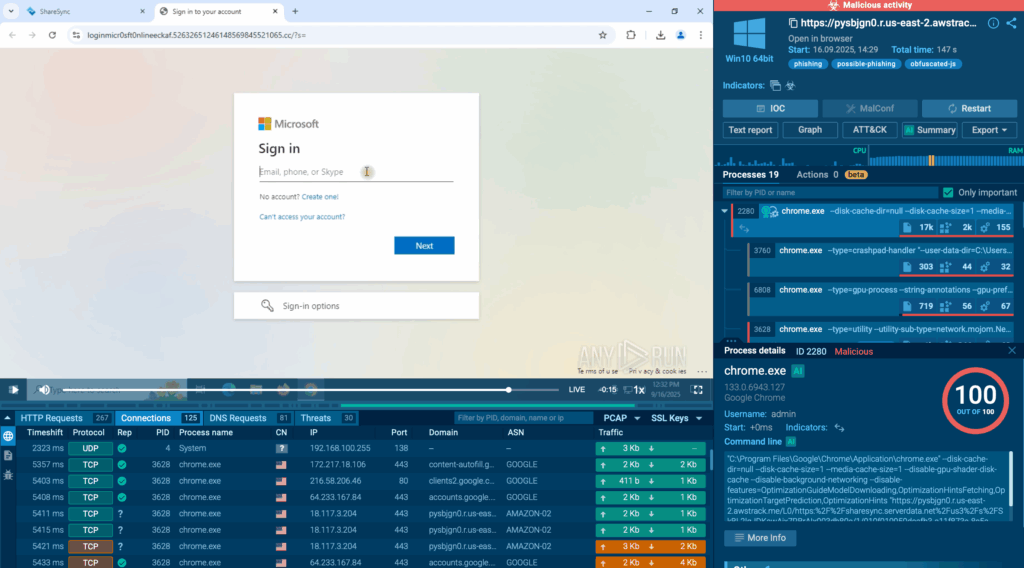
Phishing campaigns are getting harder to spot, sometimes hiding in files you’d never suspect. ANY.RUN’s cybersecurity analysts recently uncovered one such case: a malicious SVG disguised as a PDF, hosted on a legitimate domain and packed with hidden redirects. By mid-September, it scaled into a full spam wave with Microsoft-themed lures.
Let’s look at how it worked, and how analysts can gather the full chain of intel in a safe sandbox environment.
Inside the Recent SVG Attack
Here’s a sandbox session that shows the full behavior. Check the real case to watch the redirects and payload extraction live:
View the sandbox session (SVG attack)
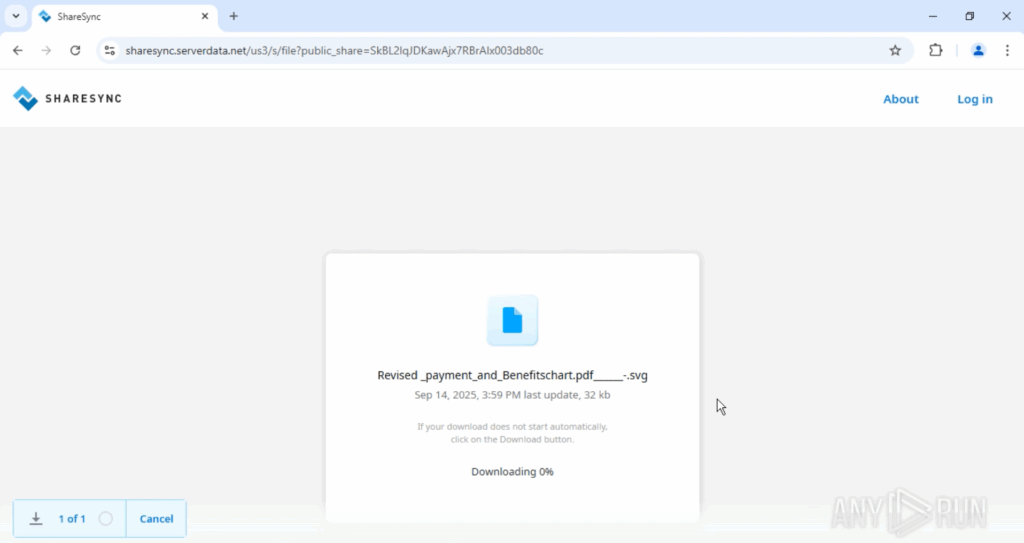
Delivery & disguise: The file arrives looking like a PDF attachment but is an SVG (XML) file. Because SVG supports scripts, attackers embed active content instead of static pixels.
Uncover hidden threats, cut investigation time from hours to minutes, and stay ahead of evolving attack techniques.Try ANY.RUN now
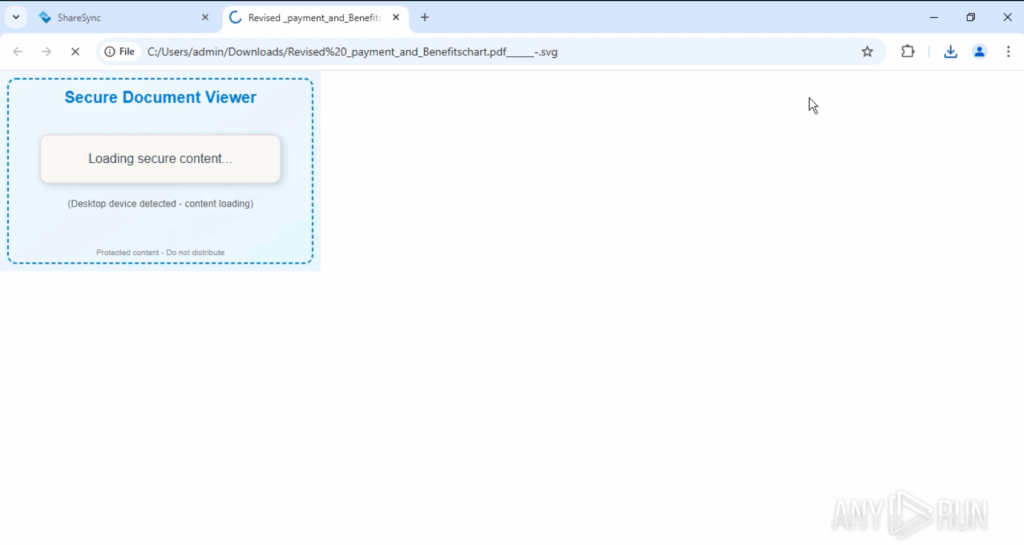
Fake prompt shown: Opening the file in a browser displays a “protected document” message to social-engineer the user into clicking or waiting.
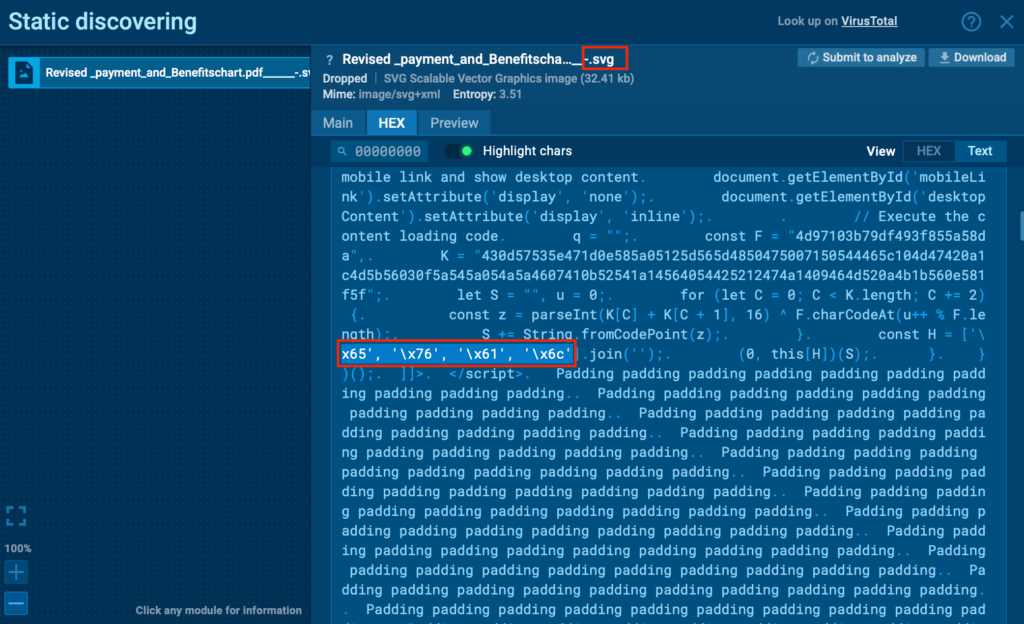
Script execution (XOR decoder): The embedded JavaScript runs an XOR decode routine that reconstructs the true redirect code and then executes it (via eval).
You can see this directly in ANY.RUN’s static/HEX view: the decoder variables, the hex/escaped bytes (for example ‘x65′,’x76’,…) and the reconstructed script are all exposed in the session. That view lets analysts dump the decoded payload and review the exact commands the SVG runs.
Layered redirects: The decoded code pushes the browser through multiple intermediary domains, obfuscating the trail. Examples observed in this chain include:
- loginmicrosft365[.]powerappsportals[.]com
- loginmicr0sft0nlineofy[.]52632651246148569845521065[.]cc
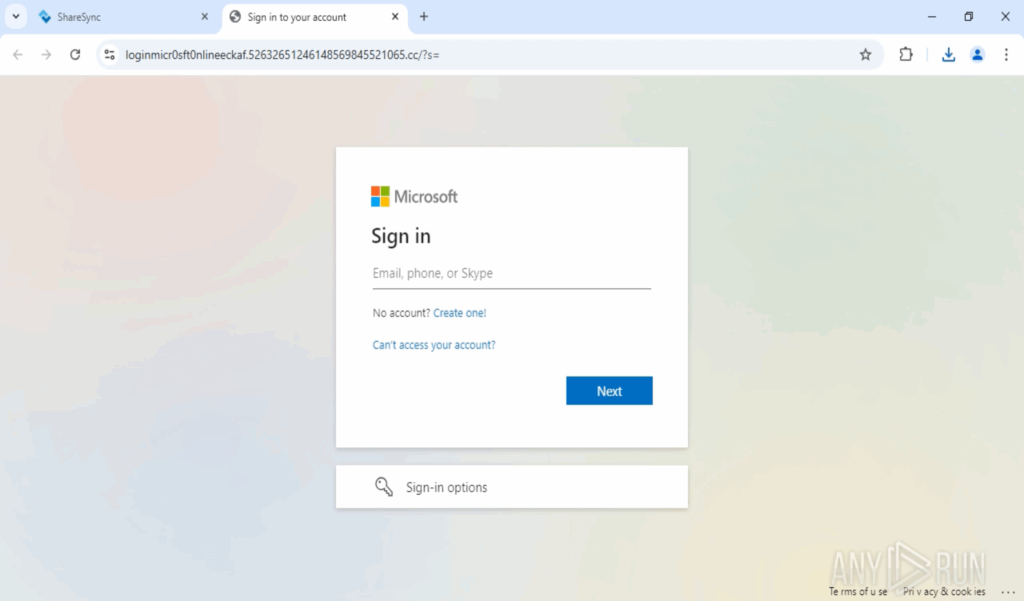
Final phishing page: The user lands on a Microsoft-branded credential page that even uses a Cloudflare Turnstile widget to look legitimate and bypass cursory checks. With ANY.RUN’s automated interactivity, these verifications are handled automatically, so analysts don’t waste time clicking through manually.
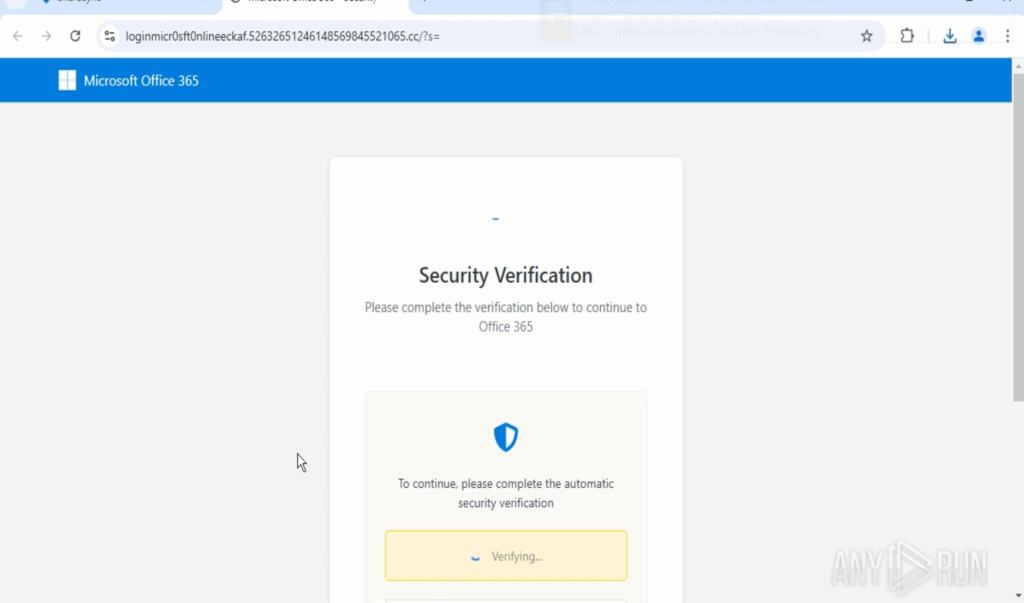
Credential collection & persistence: Entered credentials are captured and forwarded to attacker-controlled infrastructure built for scale (PhaaS-like), enabling mass harvesting.
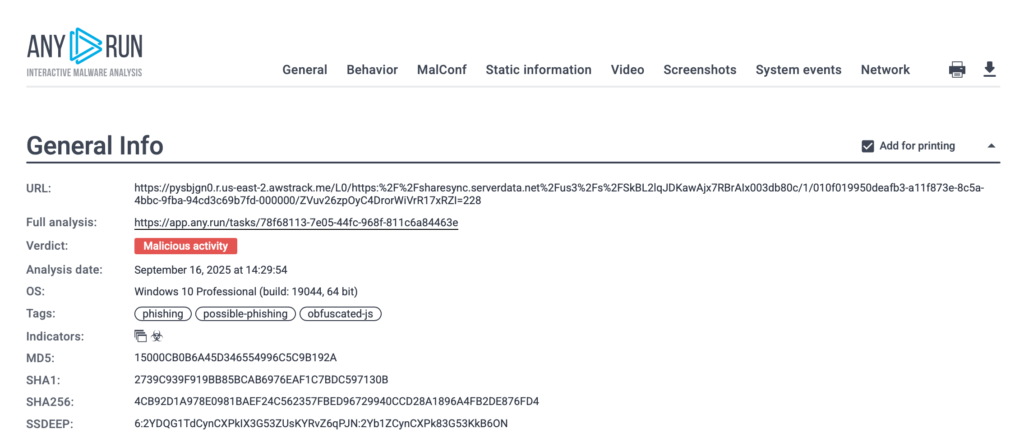
What the sandbox reveals: The interactive session shows every redirect and HTTP transaction, exposes the decoded JavaScript in HEX/Text, and captures runtime artifacts.
Exportable IOCs and reports can be directly integrated with SIEM, EDR, and threat-intel platforms, so analysts get the data inside the tools they already use, saving time and cutting extra steps.
The Sandbox Advantage: Fast Detection of New Attacks
As you can see, interactive sandboxes are especially valuable for spotting new and evasive attacks. Instead of waiting on static signatures or delayed alerts, they run the file in a live environment and surface malicious behaviors in real time.
With ANY.RUN, analysts can:
- Get malicious verdicts in under 60 seconds: 88% of threats are detected this quickly.
- Reveal the full attack chain instantly: every redirect, script, and payload mapped out without guesswork.
- Accelerate triage and response: teams report up to 94% faster triage and 3× higher SOC performance.
- Turn findings into action: export IOCs and TTPs directly into SIEM, EDR, or TI platforms to update detections and launch hunts immediately.
By transforming hours of manual work into minutes of automated visibility, sandboxes give analysts the speed, clarity, and context needed to stay ahead of new attack techniques.
Request your 14-day trial and see how fast you can catch new attacks with ANY.RUN’s sandbox.
