A critical flaw in SUSE Rancher’s user management module allows privileged users to disrupt administrative access by modifying usernames of other accounts.
Tracked as CVE-2024-58260, this vulnerability affects Rancher Manager versions 2.9.0 through 2.12.1, enabling both username takeover and full lockout of the admin account.
Organizations running unsupported versions are urged to upgrade immediately or apply mitigations to prevent unauthorized disruption of cluster administration.
Rancher RBAC Privilege Escalation
Rancher’s RBAC system relies on unique usernames at login time, but fails to enforce immutability of this field after account creation.
An attacker with update permissions on any user resource can send a crafted request to change the username field of a target account.
When the admin account is targeted, the attacker’s new, unique identifier takes precedence, and the original admin user can no longer authenticate.Example exploit request using Rancher’s API:
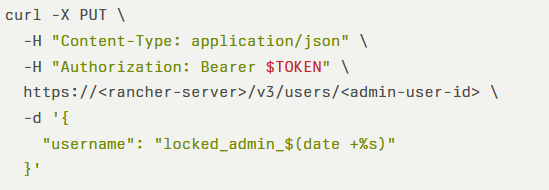
This payload renames the admin account, rendering the genuine administrator unable to log in. The flaw also permits arbitrary renaming of any user, leading to user takeover by assigning a high-privilege username to a malicious account.
| Risk Factors | Details |
| Affected Products | Rancher Manager v2.9.0–v2.9.11 v2.10.0–v2.10.9v2.11.0–v2.11.5v2.12.0–v2.12.1 |
| Impact | – Account lockout: prevents admin/UI login |
| Exploit Prerequisites | – Valid Rancher account with update permission on User API |
| CVSS 3.1 Score | 7.6 (High) |
Mitigations
SUSE Rancher has released patched versions that enforce server-side validation on the .username field.
Once set, usernames are immutable, preventing subsequent modification attempts. Affected versions and their patched counterparts include:
- 2.12.0–2.12.1 → 2.12.2
- 2.11.0–2.11.5 → 2.11.6
- 2.10.0–2.10.9 → 2.10.10
- 2.9.0–2.9.11 → 2.9.12
To upgrade, run:
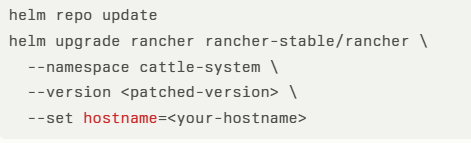
For environments where immediate upgrading is not possible, administrators should audit RBAC policies to limit update permissions on user resources to only fully trusted operators.
Additionally, enable detailed audit logging to detect and respond to suspicious PUT /v3/users API calls.
By addressing this high-severity issue, organizations protect the integrity of their Rancher UI and prevent potential denial-of-service against critical administrative accounts.
Continuous monitoring of global RBAC settings and prompt adoption of security patches remain essential best practices for securing container management platforms.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
