Roughly 50,000 Cisco Adaptive Security Appliance (ASA) and Firewall Threat Defense (FTD) appliances exposed on the public web are vulnerable to two vulnerabilities actively leveraged by hackers.
The flaws, tracked as CVE-2025-20333 and CVE-2025-20362, enable arbitrary code execution and access to restricted URL endpoints associated with VPN access. Both security issues can be exploited remotely without authentication.
On September 25, Cisco warned that the issues were actively exploited in attacks that started before patches were available to customers.
No workarounds exist for either flaw, but temporary hardening steps could include restricting VPN web interface exposure and increasing logging and monitoring for suspicious VPN logins and crafted HTTP requests.
Today, threat monitoring service The Shadowserver Foundation reports that its scans discoveredmore than 48,800 internet-exposed ASA and FTD instances that are still vulnerable to CVE-2025-20333 and CVE-2025-20362.
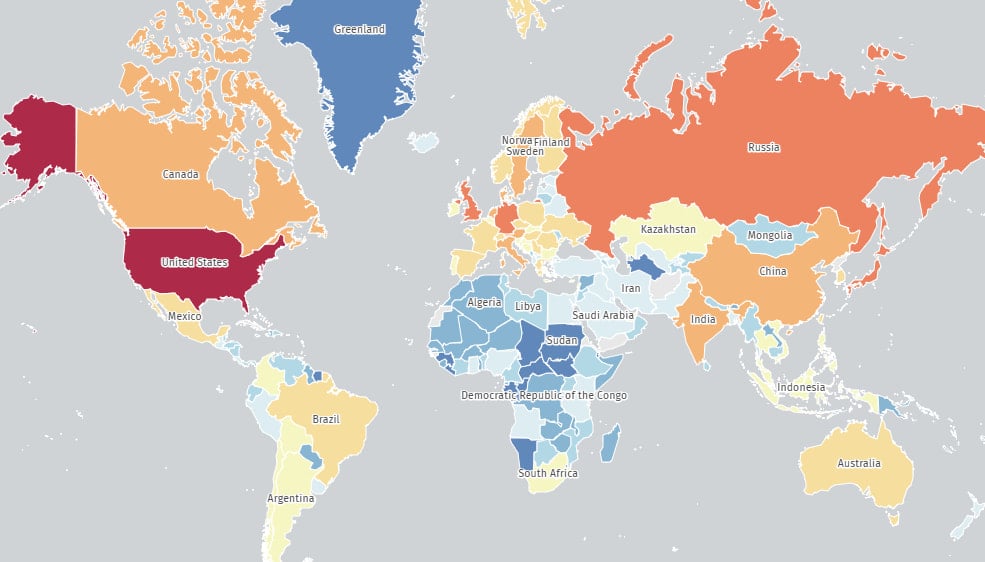
Most of the IPs are located in the United States (more than 19,200 endpoints), followed by the United Kingdom (2,800), Japan (2,300), Germany (2,200), Russia (2,100), Canada (1,500), and Denmark (1,200).
Source: The Shadowserver Foundation
These figures are as of yesterday, September 29, indicating a lack of appropriate response to the ongoing exploitation activity, as well as previous warnings.
Notably, Greynoise had warned on September 4 about suspicious scans that occurred as early as late August, targeting Cisco ASA devices. In 80% of the cases, these scans are an indication of upcoming undocumented flaws in the targeted products.
The risks associated with the two vulnerabilities are so severe that the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive that gave 24 hours to all Federal Civilian Executive Branch (FCEB) agencies to identify any compromised Cisco ASA and FTD instances on the network and upgrade those that would remain in service.
CISA also advised that ASA devices reaching their end of support (EoS) should be disconnected from federal organization networks by today (the end of the month).
A report from the U.K.’s National Cyber Security Centre (NCSC) shed more light on the attacks, noting that the hackers deployed a shellcode loader malware named ‘Line Viper,’ followed by a GRUB bootkit named ‘RayInitiator.’
Given that active exploitation has been underway for more than a week, administrators of potentially impacted systems are urged to apply Cisco’s recommendations for CVE-2025-20333 and CVE-2025-20362 [1, 2] as soon as possible.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
