A critical zero-day vulnerability affecting thousands of Cisco firewalls is being actively exploited by threat actors in the wild.
The vulnerability, tracked as CVE-2025-20333, poses an immediate risk to organizations worldwide with a CVSS score of 9.9, representing one of the most severe security flaws discovered in enterprise firewall infrastructure this year.
According to data from The Shadowserver Foundation, over 48,800 unpatched IP addresses were identified on September 29, 2025, with the United States having received the most exposure.
The vulnerability affects Cisco Secure Firewall Adaptive Security Appliance (ASA) Software and Cisco Secure Firewall Threat Defense (FTD) Software, specifically targeting the VPN web server component that millions of organizations rely on for remote access capabilities.
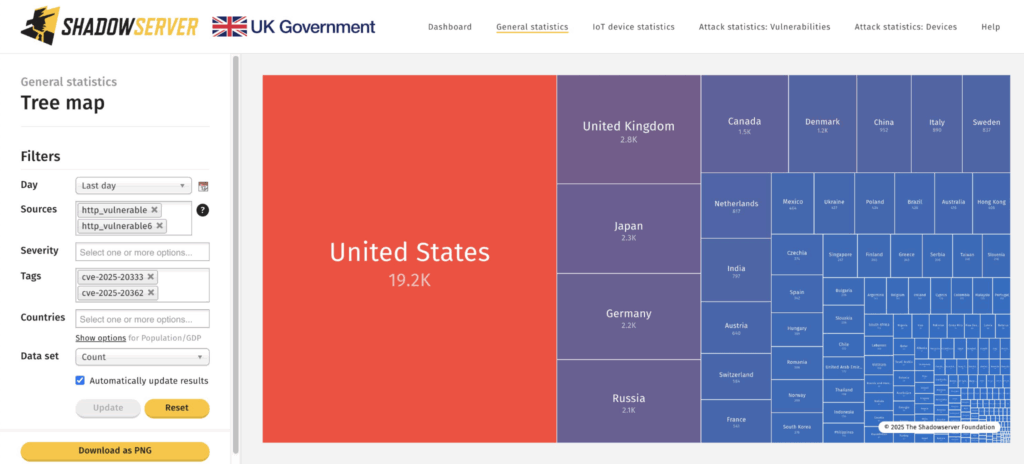
Cisco firewalls vulnerable
Buffer Overflow Vulnerability (CVE-2025-20333)
The vulnerability stems from improper validation of user-supplied input in HTTP(S) requests processed by the VPN web server.
Classified as a CWE-120 buffer overflow, the flaw allows authenticated remote attackers to execute arbitrary code with root privileges on affected devices.
This level of access essentially grants complete control over the firewall, enabling attackers to modify security policies, intercept network traffic, and establish persistent backdoors.
The attack vector requires valid VPN user credentials, which attackers can obtain through various methods including credential stuffing, phishing campaigns, or exploiting weak authentication mechanisms.
Once authenticated, attackers can send specially crafted HTTP requests containing malicious payloads that overflow memory buffers, allowing shellcode execution in the context of the root user.
Cisco’s Product Security Incident Response Team (PSIRT) has confirmed active exploitation attempts and warns that successful attacks could result in complete device compromise.
The vulnerability affects devices running vulnerable releases of ASA or FTD software with specific configurations enabled, including AnyConnect IKEv2 Remote Access, Mobile User Security (MUS), and SSL VPN services.
The affected configurations encompass critical enterprise features that organizations depend on for secure remote access. Vulnerable configurations include:
- AnyConnect IKEv2 Remote Access with client services enabled
- Mobile User Security (MUS) implementations
- SSL VPN deployments
These configurations are standard in enterprise environments, particularly those supporting remote workforce initiatives.
The vulnerability’s severity is compounded by the fact that Cisco has confirmed no workarounds exist to mitigate the risk without applying security patches.
Missing Authorization Flaw (CVE-2025-20362)
A secondary vulnerability, CVE-2025-20362 (CVSS 6.5), accompanies the primary flaw and enables unauthenticated attackers to access restricted VPN endpoints that should require authentication.
This unauthorized access vulnerability, classified as CWE-862 (Missing Authorization), can serve as a reconnaissance tool for attackers planning more sophisticated attacks.
| CVE | Title | CVSS 3.1 Score | Severity |
| CVE-2025-20333 | VPN Web Server Remote Code Execution Vulnerability | 9.9 | Critical |
| CVE-2025-20362 | VPN Web Server Unauthorized Access Vulnerability | 6.5 | Medium |
Cisco has released emergency security updates addressing both vulnerabilities and strongly recommends immediate patching.
Organizations should prioritize these updates given the active exploitation and the critical nature of affected systems.
The company also advises reviewing threat detection configurations for VPN services to enhance protection against authentication attacks and unauthorized connection attempts.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
