Confidential computing promised to protect sensitive workloads in the public cloud. Yet a new low-cost hardware attack, Battering RAM, demonstrates that even up-to-date memory-encryption schemes on Intel and AMD processors can be defeated with a simple interposer costing under 50 dollars.
Modern servers use DDR4 DRAM with hardware-backed encryption, such as Intel SGX’s Total Memory Encryption (TME) and AMD SEV-SNP, to guard private data.
Previous research on “BadRAM” exploited false SPD metadata at boot time; in response, vendors implemented stricter boot-time alias checks.
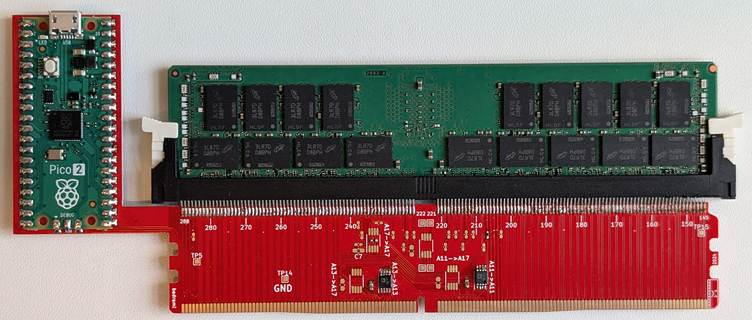
Battering RAM Attack
Battering RAM operates dynamically, where a custom interposer sits between the CPU and DIMM, transparent during POST, and evades SPD spoofing checks.
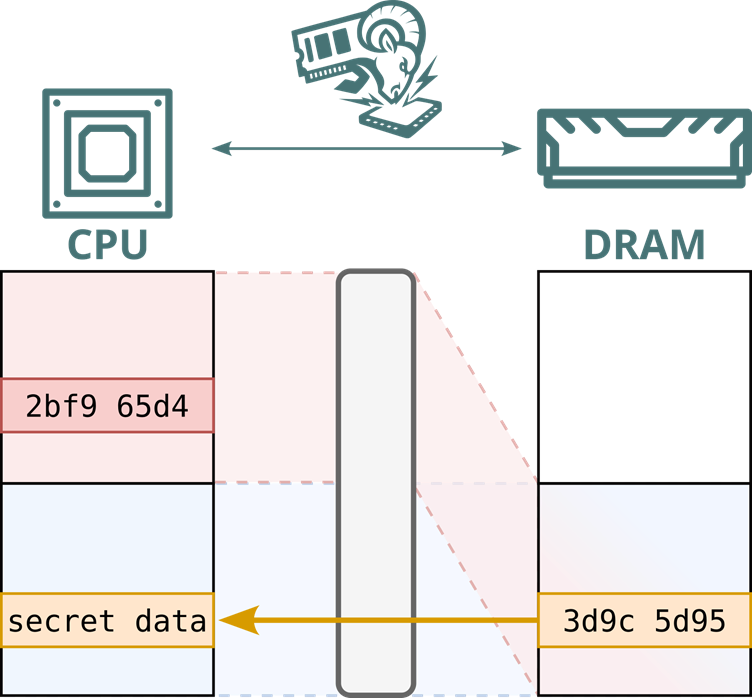
Once the system is online, an analog switch flips, redirecting encrypted traffic from victim addresses to an attacker-controlled alias buffer.
Captured ciphertext is then replayed into a controlled enclave, yielding arbitrary plaintext access. This attack fully compromises both SGX and SEV-SNP attestation on patched cloud platforms, enabling read/write of enclave memory.
The interposer design, shared on GitHub, uses two SPDT analog switches and a microcontroller to toggle aliasing at runtime.
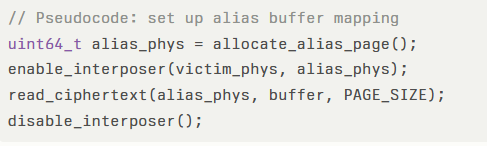
This code fragment illustrates the two-phase capture-and-replay process that yields decrypted enclave data.
Implications for Cloud Security
Battering RAM exposes fundamental flaws in static memory-encryption engines, which lack cryptographic freshness checks.
Because TME and SEV-SNP derive ciphertext solely from a fixed key and physical address, replayed data decrypts predictably, nullifying passive-attack defenses like cold-boot mitigation.
Key implications include:
- Physical-layer adversaries rogue cloud staff or supply-chain attackers require only brief access to install the interposer.
- Software or firmware patches cannot detect on-the-fly address remapping. True mitigation demands per-page nonce or integrity checks integrated into the DRAM encryption engine.
- At under $50, Battering RAM democratizes a class of attacks formerly limited to high-end DRAM interposers (> $100,000).
Academic teams at KU Leuven, University of Birmingham, and Durham University conducted the research and have published schematics, firmware, and proof-of-concept code under CC0.
Both Intel and AMD have issued security advisories acknowledging the findings, but note that physical interposer attacks are beyond the current product scope.
As public cloud adoption of SGX and SEV-SNP grows, covering services on AWS, Azure, Google Cloud, and IBM Cloud, organizations must reassess the physical security of datacenter infrastructure.
Without significant enhancements to memory encryption protocols, Battling RAM underscores that confidential computing is not indestructible.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
