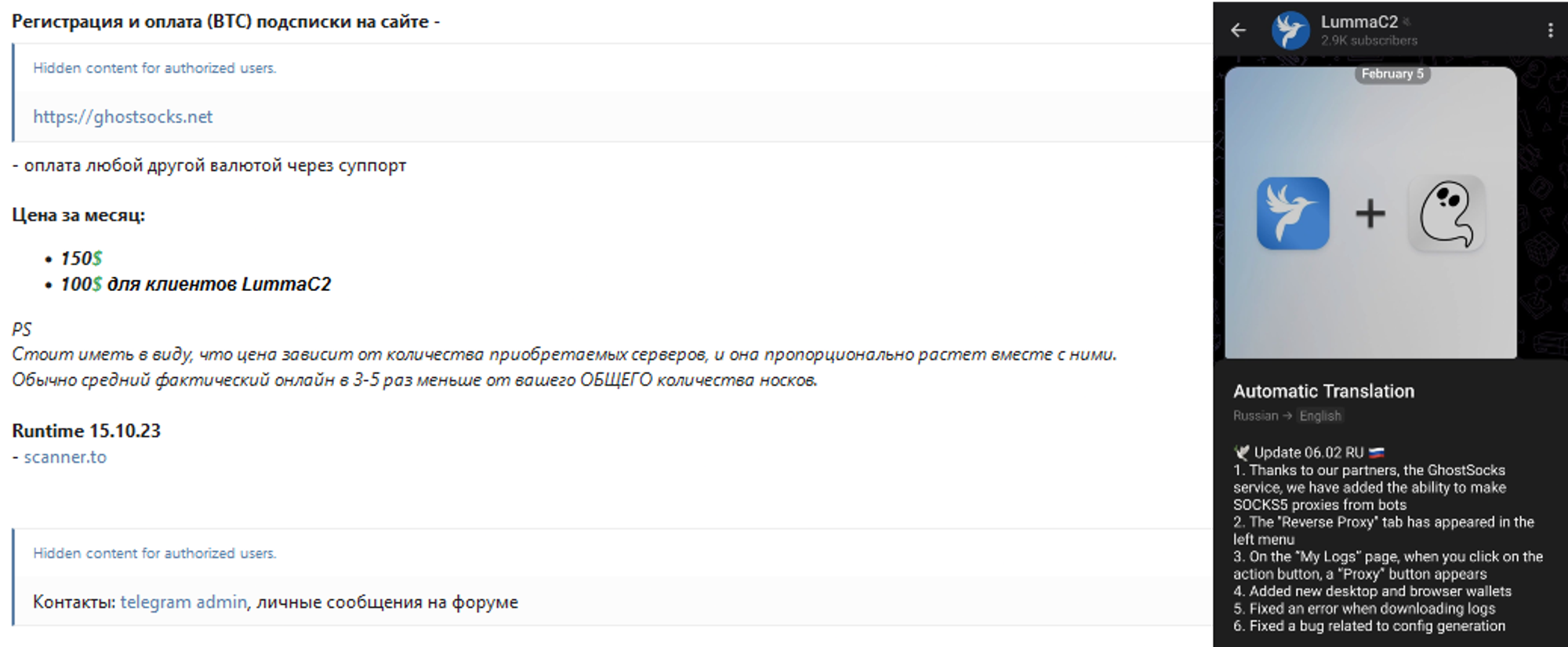
On October 15, 2023, a threat actor using the handle GhostSocks published a sales post on the Russian cybercrime forum xss[.]is advertising a novel Malware-as-a-Service (MaaS) offering.
The post introduced GhostSocks, a service designed to turn compromised Windows machines into residential SOCKS5 proxies, enabling cybercriminals to bypass anti-fraud defenses and monetize infected hosts.
The initial sales thread highlighted GhostSocks’ core functionality: transforming end-user devices into proxy nodes under threat-actor control.
Subsequent posts demonstrated the GhostSocks management panel, showcasing build creation, proxy assignment and real-time status monitoring.
The thread also featured weekly developer changelogs—detailing feature enhancements—and customer testimonials praising the reliability and low latency of GhostSocks proxies.
Adoption and Ecosystem Integration
Early interest in GhostSocks spanned a spectrum of cybercriminal operations—from low-level fraud rings to sophisticated ransomware groups.
In February 2025, leaked BlackBasta chat logs revealed the gang’s discussion of using GhostSocks alongside Lumma Stealer to ensure prolonged network access after initial compromise.
Although the user base remained limited through late 2023, adoption surged in February 2024 following an announced partnership with Lumma Stealer, allowing affiliate users to install GhostSocks automatically and channel stolen credentials through proxy infrastructure.
Despite law enforcement disruption of Lumma Stealer infrastructure later in 2025, GhostSocks continues active development and sales—even as the operators have migrated away from the new XSS forum. The service’s resilience underscores its role as a staple in the MaaS ecosystem.
GhostSocks is distributed as a 32-bit DLL or standalone executable, both authored in Go and obfuscated using the open-source garble project.
Strings and API symbols are encrypted at build time and decrypted at runtime via a custom routine. GhostSocks lacks persistence functionality, focusing solely on SOCKS5 proxy provisioning. Upon execution, a named mutex (“start to run”) prevents multiple instances from spawning.
During startup, GhostSocks attempts to locate a dynamic configuration in the user’s %TEMP% directory. If missing, it reverts to a hardcoded fallback config embedded in the binary.
Decryption of this config yields a list of defanged Command-and-Control (C2) URLs. The malware iterates through these endpoints until a successful connection is established, then generates random proxy credentials and registers with the C2 via an HTTP GET request.
An additional x-api-key header is appended once the build URL succeeds. Upon receiving a 200 OK response, GhostSocks spawns a bi-directional SOCKS5 tunnel using the go-socks5 and yamux libraries.
Mitigations
Personal Precautions: Avoid running untrusted executables and maintain endpoint protection with heuristics for Go-based obfuscators.
Organizational Defenses: Block known GhostSocks relay server IPs and monitor outbound SOCKS5 traffic to detect anomalous proxy usage. Enforce strict network segmentation and vet remote IP addresses—even if they appear residential—to prevent trust bypass.
Observables and Yara Rules are publicly available in the Synthient research repository for immediate deployment.
Once a server returns a 200 status code indicating that our client has been successfully initiated, GhostSocks will spawn a SOCKS5 connection.
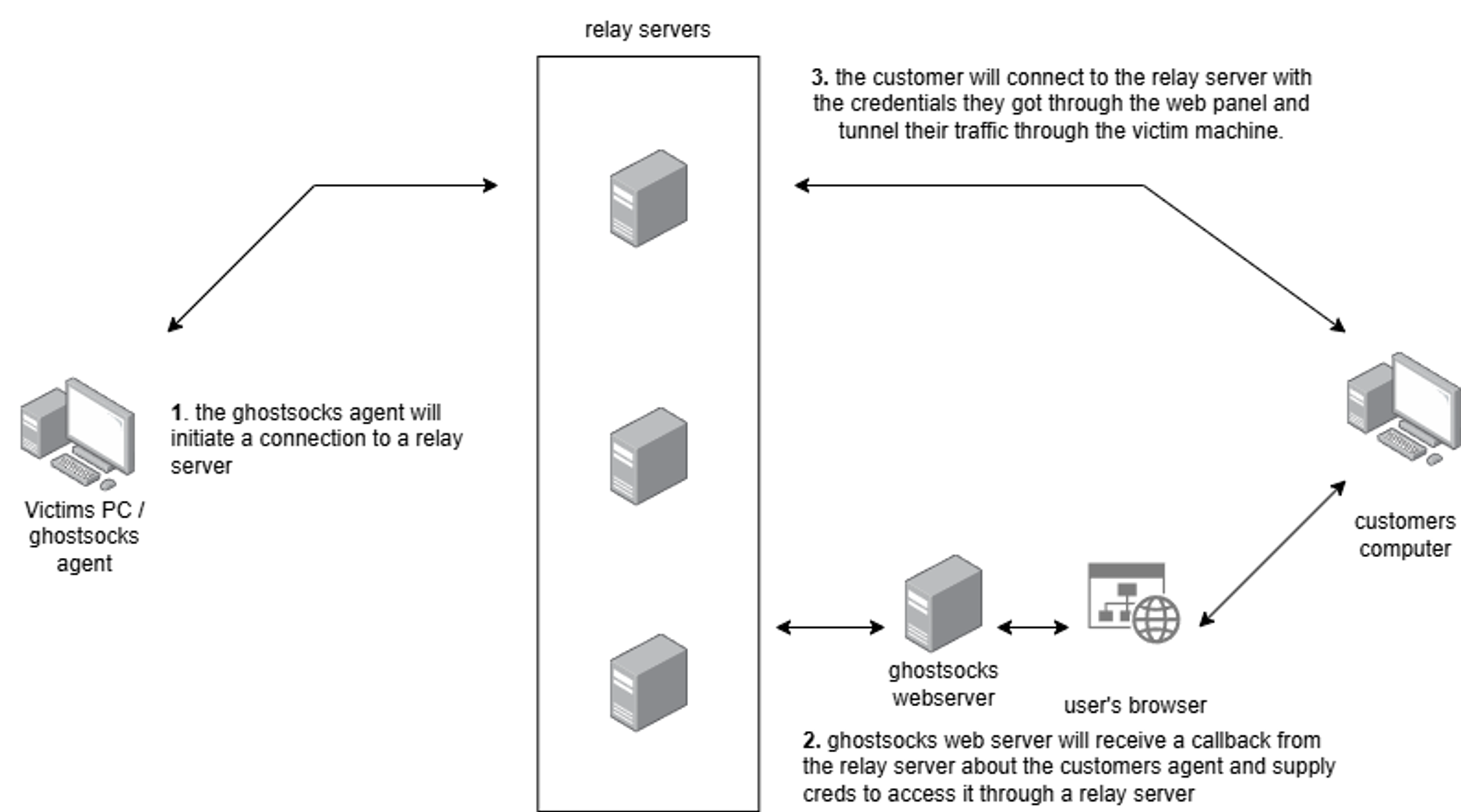
While GhostSocks does not introduce groundbreaking techniques, its popularity among diverse threat actors highlights the growing trend of double victimization: compromised systems become unwitting proxies, amplifying attacks against additional targets.
At rates as low as $0.50 per device per day, GhostSocks and similar proxy malware will likely remain an attractive commodity in underground markets. Vigilant network monitoring and proactive blocking of proxy protocols are essential to curb this emerging threat.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
