A publicly available proof-of-concept (PoC) exploit has been released for CVE-2025-32463, a local privilege escalation (LPE) flaw in the Sudo utility that can grant root access under specific configurations.
Security researcher Rich Mirch is credited with identifying the weakness, while a functional PoC and usage guide have been published in an open GitHub repository, accelerating the urgency for patching across Linux environments that rely on Sudo’s chroot functionality.
According to the project documentation, versions 1.9.14 through 1.9.17 are vulnerable, with fixes available in 1.9.17p1 and later. Systems running legacy builds prior to 1.9.14 are not impacted because the chroot feature did not exist in those releases.
Local Privilege Escalation Flaw (CVE-2025-32463)
The vulnerability resides in how Sudo handles chroot-related invocation paths and environment when executing commands with elevated privileges.
Under certain conditions, a low-privileged user can exploit the chroot feature to pivot out of the constrained environment and execute commands as root.
This turns a standard LPE scenario into full system compromise when Sudo policies permit chroot usage.
The PoC demonstrates a straightforward exploitation flow: verify the target Sudo version, run the exploit script, and observe the effective UID/GID change to root.
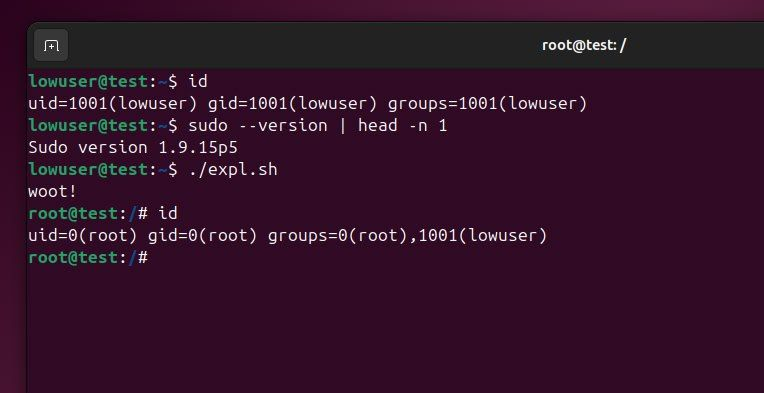
In testing screenshots, the user transitions from uid=1001 to uid=0 after executing the script, confirming successful escalation.
The project explicitly categorizes the issue as “Local Privilege Escalation to Root via Sudo chroot in Linux,” emphasizing that weaponization hinges on local account access and specific Sudo configurations that enable chroot execution.
| Risk Factors | Details |
| Affected Products | Sudo versions 1.9.14 through 1.9.17 |
| Impact | Local privilege escalation |
| Exploit Prerequisites | Local user access with ability to invoke sudo under misconfigured chroot settings |
| CVSS 3.1 Score | Not yet assigned |
Mitigations
Immediate remediation is to upgrade Sudo to 1.9.17p1 or newer across affected hosts. Where upgrades must be staged, administrators should harden Sudoers policies to deny or tightly restrict use of chroot, and enforce least privilege.
Mandatory access control frameworks such as AppArmor or SELinux can further constrain Sudo behavior and contain abuse paths during change windows.
From a detection perspective, defenders should monitor for anomalous Sudo invocations referencing chroot or unusual working directories, correlate privilege transitions (uid changes to 0) from non-standard shells or paths, and alert on rapid “id → exploit → id” sequences commonly seen during exploitation tests.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
