NCSC has issued an urgent warning regarding a critical zero-day flaw in Oracle E-Business Suite (EBS) that is currently being exploited in the wild.
Tracked as CVE-2025-61882, the vulnerability resides in the BI Publisher Integration component of Oracle Concurrent Processing and allows unauthenticated remote code execution.
Organisations running EBS versions 12.2.3 through 12.2.14—especially those exposed to the internet are at the highest risk.
Oracle BI Publisher Flaw (CVE-2025-61882)
Oracle’s security alert confirms that an attacker can send specially crafted HTTP requests to the BI Publisher Integration servlet without any prior authentication, achieving full system compromise.
No user interaction is required. A proof-of-concept HTTP request pattern resembles the following:
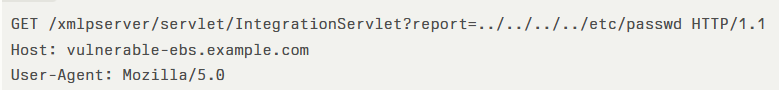
Successful exploitation could allow arbitrary command execution under the Oracle EBS application account, potentially leading to data exfiltration, system takeover, or lateral movement across the corporate network.
Indicators of compromise (IoCs) published in Oracle’s advisory include anomalous servlet URIs, unexpected child processes spawned by $XBPSRV, and suspicious outbound connections on non-standard ports.
The NCSC is closely monitoring incident reports and has observed multiple exploitation attempts against UK organisations.
Exposed EBS instances on the public internet are the primary target, although internal networks lacking proper segmentation may also be vulnerable to threat actors who gain an initial foothold.
| Risk Factors | Details |
| Affected Products | Oracle E-Business Suite (EBS) 12.2.3 – 12.2.14; BI Publisher Integration component of Oracle Concurrent Processing |
| Impact | Remote code execution (RCE) |
| Exploit Prerequisites | Network access to exposed BI Publisher Integration endpoint; no authentication or user interaction required |
| CVSS 3.1 Score | 9.8 (Critical) |
Mitigation
To address CVE-2025-61882, the NCSC urges UK organisations to adopt a defense-in-depth approach.
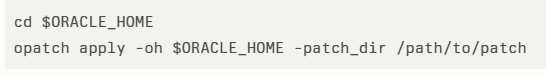
Apply Oracle’s October 2023 Critical Patch Update followed by the dedicated EBS patch for CVE-2025-61882. Oracle’s advisory provides detailed installation instructions.
Leverage the published IoCs to scan logs, web access records, and process listings for signs of exploitation. Tools such as grep and SIEM rules can help identify:

Limit public exposure of Oracle EBS components. Where internet access is unavoidable, implement web application firewalls (WAFs), strict access control lists (ACLs), and network perimeter guidelines as outlined by the NCSC.
Deploy EDR agents on application servers and conduct behavioral analysis to detect anomalous child processes or unusual outbound traffic.
If compromise is suspected, contact Oracle PSIRT and report to the NCSC via its online portal. Early notification can help coordinate response and threat intelligence sharing.
Additional free NCSC resources include guidance on vulnerability management, preventing lateral movement, and the Early Warning service for real-time alerts.
By taking these precautions, Oracle E-Business Suite resilience would be strengthened against present and upcoming vulnerabilities.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
