In a very recent and well-targeted phishing attempt, scammers tried to get hold of the 1Password credentials belonging to a Malwarebytes’ employee.
Stealing someone’s 1Password login would be like hitting the jackpot for cybercriminals, because they potentially export all the saved logins the target stored in the password manager.
The phishing email looked like this:
“Your 1Password account has been compromised
Unfortunately, Watchtower has detected that your 1Password account password has been found in a data breach. This password protects access to your entire vault.
Take action immediately
To keep your account secure, please take the following actions:
– Change your 1Password account password
– Enable two-factor authentication
– Review your account activity
Secure my account now
If you need help securing your account, or have any questions, contact us. Our team is on hand to provide expert, one-on-one support.”
While the email looks convincing enough, you can spot a few red flags.
- The sender’s address
watchtower@eightninety[.]comdoes not belong to 1Password, which typically use the domain@1password.com. - If you hover over the “Secure my account now” button you’ll notice that it points to:
https://mandrillapp[.]com/track/click/30140187/onepass-word[.]com?p={long-identifier}
Although 1Password’s Watchtower feature can send alerts about compromised passwords, it does so by checking its database of known data breaches and then notifying you directly within the 1Password app or through very specific emails about the breach—not by sending a generic message like this.
Obviously, the onepass-word[.]com is a feeble attempt to make it look legitimate. I guess all the good typosquats were already taken or protected. What’s interesting is that the “Contact us” link goes to the legitimate support.1password.com, although it also flows through a redirect through mandrillapp.
Mandrillapp is a transactional email API and delivery service provided by Mailchimp. It enables organizations to send automated, event-driven emails like order confirmations, password resets, and shipping notifications. Mandrill also provides delivery tracking and statistics to their customers.
What the scammers may not have realized is that Mandrillapp doesn’t forward people to known phishing websites.

Shortly after the emails went out on October 2, the domain was already classified as a phishing site by several vendors. By October 3, anyone that clicked the button would end up viewing an error message on mandrillapp[.]com saying bad url - reference number: {23 character string}.
But early birds would have seen this form:
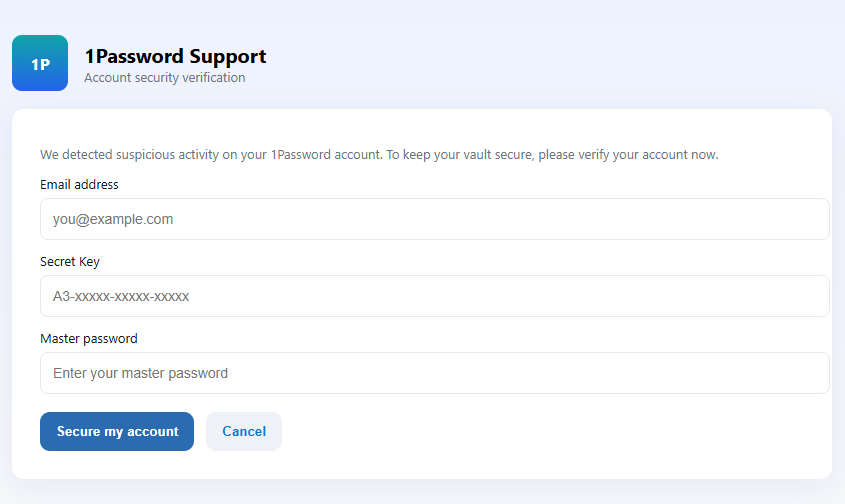
Anyone who fell for this scam would have sent their 1Password credentials straight to the phishing crew.
On September 25, 2025, Hoax-Slayer reported about a very similar phishing expedition. This might indicate that this was the first—and probably is not the last—attempt, so be warned.
With the key to your password vault, cybercriminals could take over all your important accounts and potentially steal your identity, so be very careful about where and when you use these credentials.
Our advice:
- Do not click any links or buttons in an unsolicited email
- Do not provide any of your 1Password credentials or personal information.
- If you are concerned about your 1Password account, go directly to the official 1Password website or app and check your account status there.
- Use up-to-date real-time protection which includes a web protection module.
Indicators of compromise (IOCs)
Email address:
watchtower@eightninety[.]com
Domain Phishing website:
onepass-word[.]com
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
