Threat actors are actively exploiting a critical vulnerability in the Service Finder WordPress theme that allows them to bypass authentication and log in as administrators.
Administrator privileges in WordPress grant full control over content and settings, permission to create accounts, upload PHP files, and export databases.
WordPress plugin security firm Wordfence recorded more than 13,800 exploitation atempts since August 1st.
Service Finder is a premium WordPress theme designed for service directory and job board websites. It supports customer booking, feedback, time slot management, staff management, invoice generation, and a payment system.
The theme has more 6,000 sales on Envato Market, and like most premium plugins, it is typically used by active sites.
The vulnerability exploited in the latest attacks is tracked as CVE-2025-5947 and has a critical severity score of 9.8. It affects Service Finder versions 6.0 and older, stemming from an improper validation of the original_user_id cookie in the service_finder_switch_back() function.
An attacker exploiting CVE-2025-5947 can log in as any user, including administrators, without authentication.
The issue was discovered by security researcher ‘Foxyyy,’ who reported it through Wordfence’s bug bounty program on June 8.
Aonetheme, the theme’s vendor, addressed the security issue in version 6.1, released on July 17. At the end of the month, the issue was publicly disclosed and exploitation began the next day.
For about a week since September 23, Wordfence observed a surge of more than 1,500 attack attempts every day. Overall, the researchers saw more than 13,800 exploit attempts.
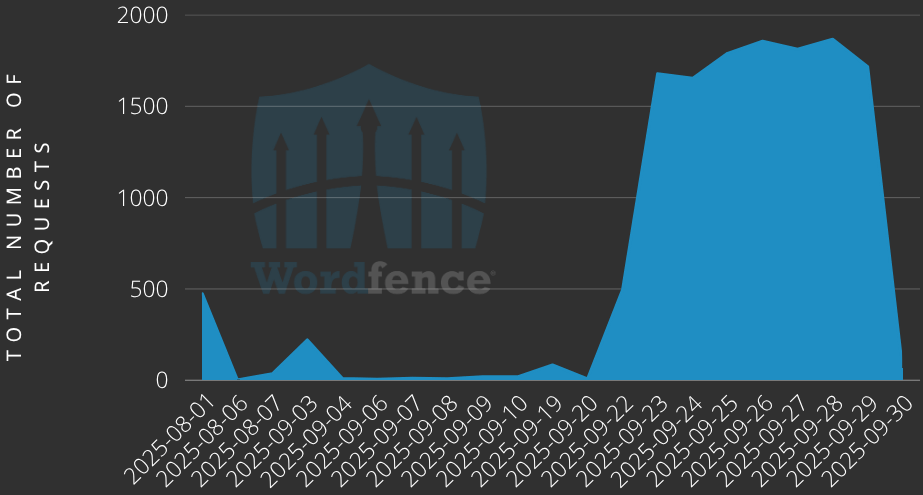
Source: Wordfence
Based on Wordfence’s observations, a typical attack includes an HTTP GET request to the root path with a query parameter (switch_back=1) to impersonate an existing user.
The researchers say that there are several IP addresses used for launching the attacks. However, thousands of attack requests orginated from just five of them:
- 5.189.221.98
- 185.109.21.157
- 192.121.16.196
- 194.68.32.71
- 178.125.204.198
As part of defense measures against these attacks is blocklisting the above IP addresses. However, it should be noted that attackers can switch to new ones.
The researchers say that there are no clear indicators of compromise to stop these attacks apart from requests that contain the ‘switch_back’ parameter.
Website administrators should review all logs for suspicious activity or accounts that threat actors may create for persistence.
Wordfence warns that “the absence of any such log entries does not guarantee that your website has not been compromised,” as administrator access gives attackers the capability to cover their tracks by deleting logs or other evidence.
Given the active exploitation status of CVE-2025-5947, users of the Service Finder theme are recommended to apply the security update as soon as possible or stop using the plugin.

Join the Breach and Attack Simulation Summit and experience the future of security validation. Hear from top experts and see how AI-powered BAS is transforming breach and attack simulation.
Don’t miss the event that will shape the future of your security strategy
