A critical authentication bypass in the Service Finder Bookings plugin has enabled unauthenticated attackers to assume administrator privileges on thousands of WordPress sites.
Exploitation began within 24 hours of public disclosure, and over 13,800 exploit attempts have been blocked by the Wordfence Firewall to date.
On June 8, 2025, a submission to the Wordfence Bug Bounty Program revealed an Authentication Bypass vulnerability in Service Finder Bookings, a plugin bundled with the Service Finder theme.
Approximately 6,000 sites purchased this theme, exposing a significant attack surface. The flaw resides in the plugin’s service_finder_switch_back() function, which switches user accounts based solely on a cookie value without authentication checks.
As a result, malicious actors can craft a request bearing an original_user_id cookie and gain access to any account, including administrators.
The vendor patched the issue in version 6.1 on July 17, 2025, and Wordfence publicly disclosed the vulnerability on July 31, 2025.
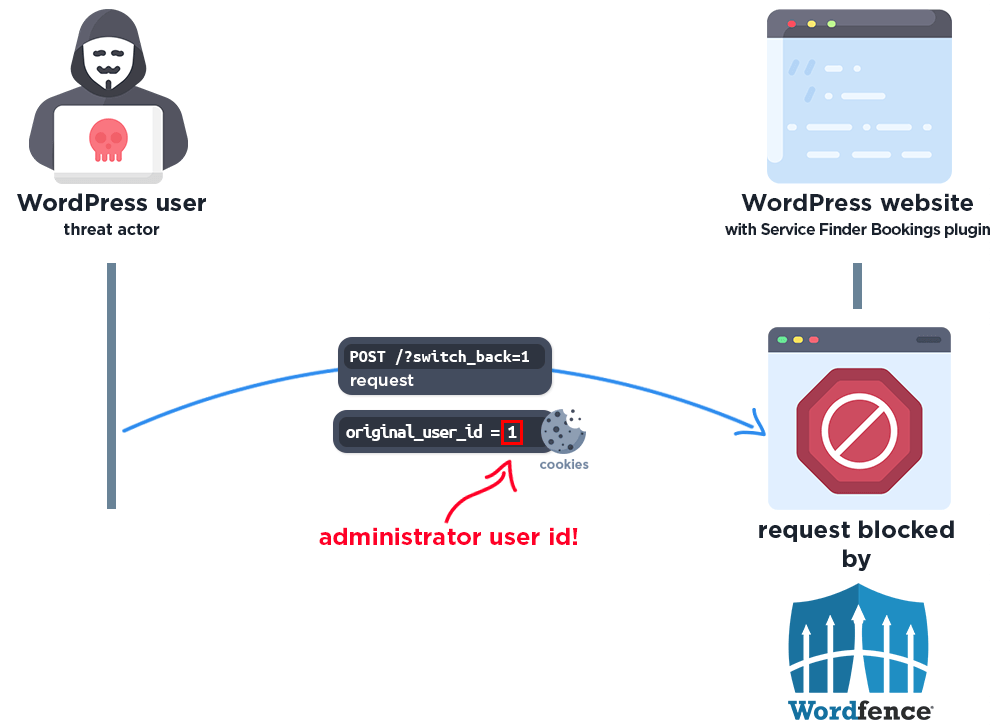
Within hours, threat actors began probing for vulnerable sites. Wordfence Premium, Care, and Response subscribers received a firewall rule on June 13, while free users received it after the standard 30-day delay on July 13, 2025. Despite firewall protections, the underlying vulnerability remains exploitable on unpatched sites.
Active Exploitation Data
Exploit attempts skyrocketed immediately after the disclosure. Wordfence Intelligence assigns a CVSS rating of 9.8 (Critical) to CVE-2025-5947.
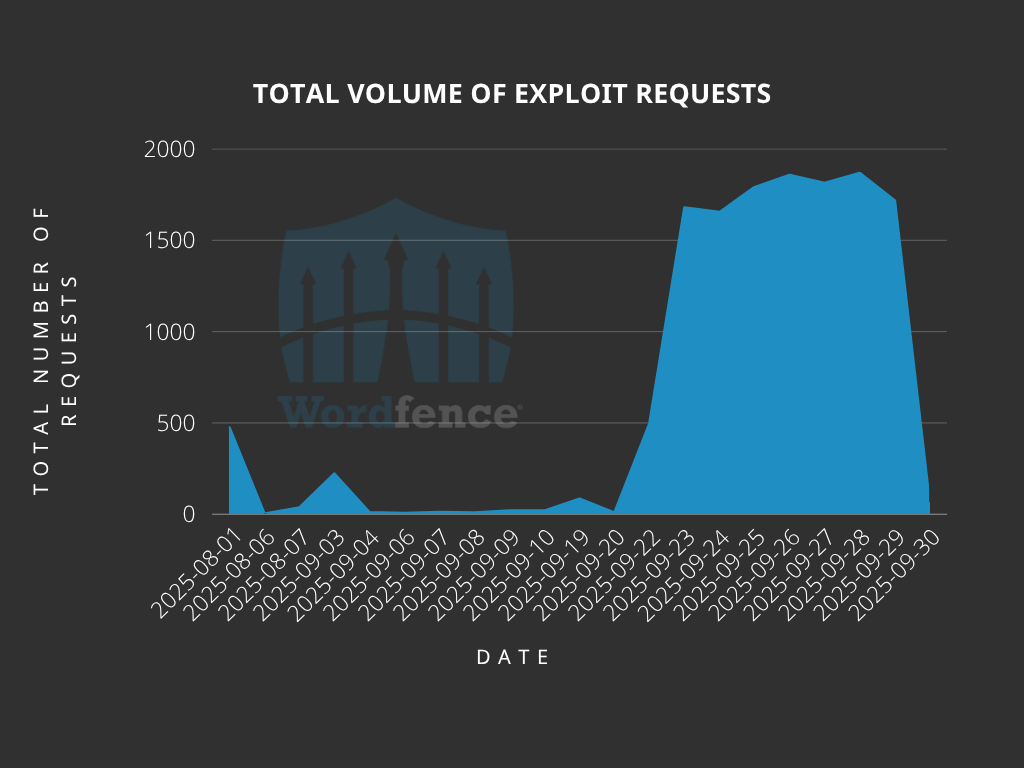

Between August 1 and September 29, over 13,800 malicious requests were blocked. A representative exploit request appears as follows:
textGET /?switch_back=1 HTTP/1.1
Cookie: original_user_id=1;
Host: victim-site.com
The plugin’s switch-back handler fails to verify whether the cookie bearer is authorized, as shown in these code lines:
phpfunction service_finder_switch_back() {
if (isset($_COOKIE['original_user_id'])) {
$original_user_id = intval($_COOKIE['original_user_id']);
if (get_userdata($original_user_id)) {
wp_set_current_user($original_user_id);
wp_set_auth_cookie($original_user_id);
}
}
}
Because there is no check on the requester’s credentials or nonce validation, attackers can leverage this path to fully compromise sites.
Analysis of blocked traffic reveals clusters of mass scanning and targeted exploitation from a handful of IP addresses. The most active threat sources and their blocked request counts are presented below.
| IP Address | Blocked Requests |
|---|---|
| 5.189.221.98 | 2,700 |
| 185.109.21.157 | 2,600 |
| 192.121.16.196 | 2,600 |
| 194.68.32.71 | 2,300 |
| 178.125.204.198 | 1,400 |
These IPs continue to generate high volumes of exploit attempts, peaking between September 22 and 29.
Mitigations
Site owners must update Service Finder Bookings to version 6.1 immediately. Firewall rules alone cannot guarantee protection if the plugin remains outdated.
Administrators should review logs for any requests containing the switch_back parameter, especially those originating from the IP addresses listed above.
Because attackers can erase evidence after gaining admin privileges, the absence of suspicious log entries does not imply safety.
For ongoing defense, users of Wordfence Premium, Care, and Response already have active firewall rules. Free users can manually implement custom WAF rules or deploy the patch without delay.
If a site is suspected of compromise, Wordfence Care provides incident response and cleanup services, while Wordfence Response offers 24/7 remediation with a one-hour response commitment.
Thousands of sites remain at risk until patched. It is imperative to apply the Service Finder Bookings update, monitor logs for abnormal activity, and share this advisory with colleagues still running vulnerable versions. Remaining vigilant against authentication bypass exploits is critical to safeguarding WordPress environments against full site takeover.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
