A significant uptick in Akira ransomware attacks has been observed exploiting unpatched SonicWall SSL VPN devices between July and August 2025.
Despite a patch release the same day, many organizations remained vulnerable, allowing threat actors to gain initial access and deploy Akira’s double-extortion scheme.
On August 20, 2025, Darktrace detected anomalous network scanning and reconnaissance activity on a U.S. customer’s network.
Initially attributed to a potential zero-day, SonicWall later confirmed that all incidents stemmed from exploitation of CVE-2024-40766, an improper access control flaw disclosed on August 23, 2024.
Reconnaissance included repeated Advanced IP Scanner lookups against an internal SonicWall SSL VPN server, followed by lateral movement and data exfiltration.
The SOC team traced the foothold to a virtual private network appliance running SonicOS 7.0.1.5035, confirming exploitation of CVE-2024-40766.
Akira is known to target organizations across multiple sectors, most notably those in manufacturing, education, and healthcare.
Using previously stolen credentials and misconfigurations in the Virtual Office Portal, attackers bypassed multi-factor protections and escalated privileges. Approximately 2 GiB of sensitive data was exfiltrated before Darktrace containment actions halted further damage.
Technical Analysis of Exploit and Malware
CVE-2024-40766 permits unauthorized access to administrative endpoints, enabling remote control of SSL VPN configurations. A minimal proof-of-concept exploit in Python leverages an HTTP POST to the vulnerable endpoint:
pythonimport requests
url = "https://victim-vpn.example.com/cgi-bin/sslvpn_cfg"
payload = {"func": "get_user_info", "user": "admin"}
response = requests.post(url, data=payload, verify=False)
print(response.text)
Following access, attackers dropped Akira Windows and Linux variants. The Windows build encrypts file systems, while the ESXi variant targets hypervisor file stores, enabling rapid encryption across cloud infrastructures.
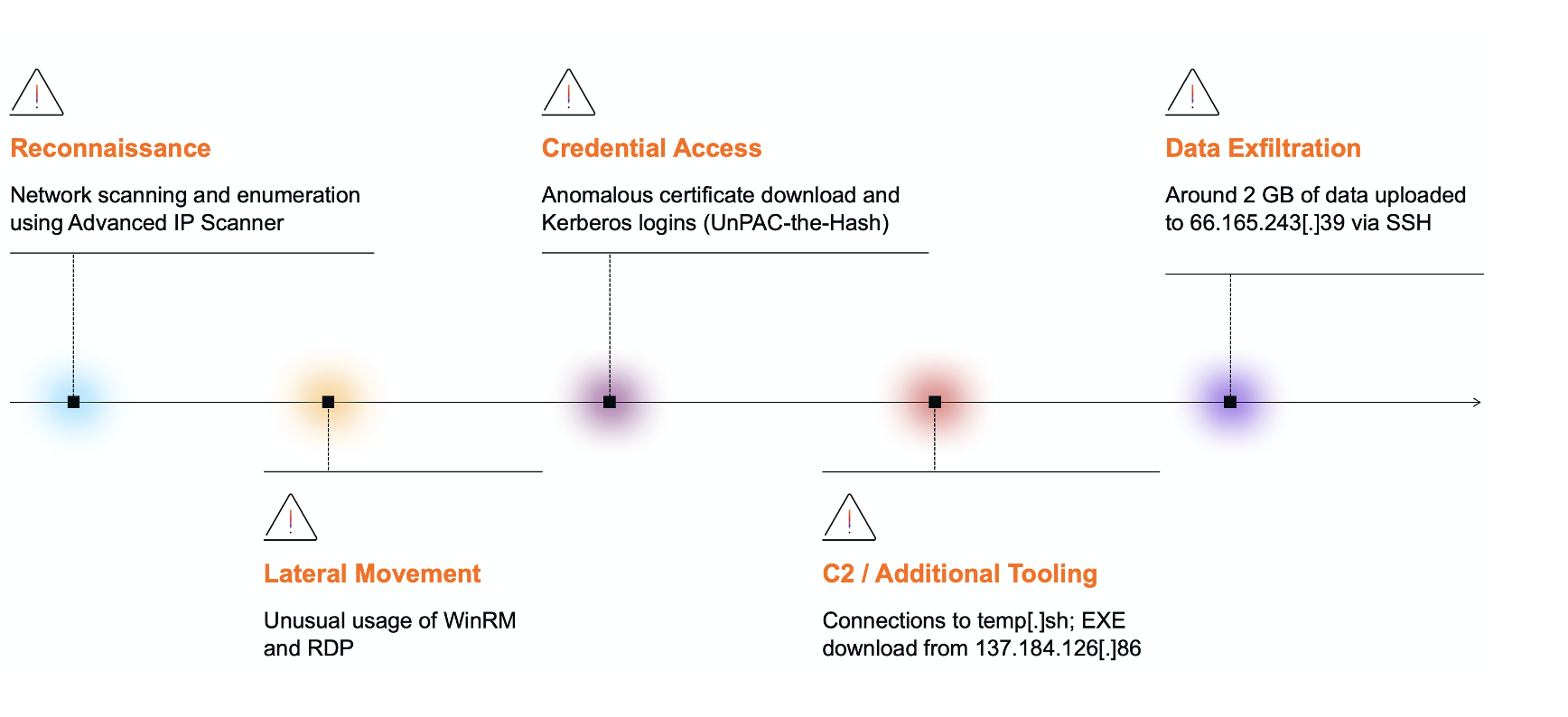

Once inside, adversaries moved laterally using WinRM and RDP, extracted NTLM hashes via Kerberos PKINIT and U2U authentication (“UnPAC the hash”), and deployed ransomware binaries using valid administrative tools.
C2 communications utilized temporary cloud-hosting services (e.g., temp[.]sh) and direct downloads from rare IPs.
Mitigations
This campaign underscores the critical importance of timely patching and robust configuration management.
CVE-2024-40766 was exploitable over a year after disclosure, demonstrating that adversaries will continually scan for unpatched systems.
Misconfigurations in Virtual Office Portals further enabled initial access even on patched devices, highlighting the need for credential hygiene and periodic configuration audits.
Ransomware operators now favor legitimate administrative protocols—WinRM, RDP, Kerberos—to blend malicious activity into normal traffic.
The “UnPAC the hash” technique, abused here, showcases how certificate-based Kerberos authentication can be subverted to extract NTLM hashes for lateral movement.
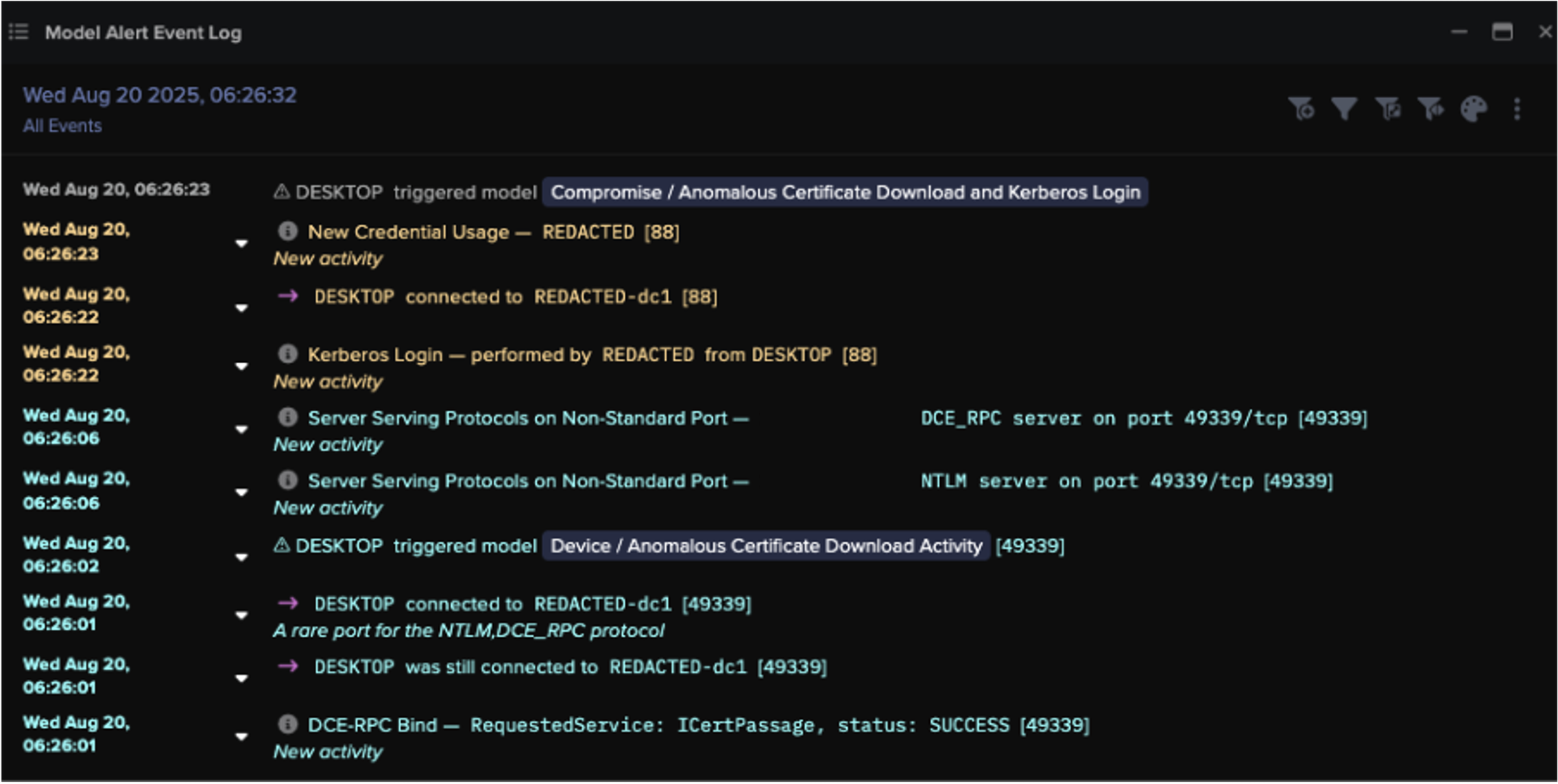

Monitoring for unusual Kerberos PKINIT requests, DCE-RPC calls, and abnormal external data transfers is essential.
Defenders should adopt a defense-in-depth approach:
- Enforce least-privilege access and multi-factor authentication on all VPN portals.
- Deploy network segmentation to limit lateral movement.
- Monitor and block rare external endpoints and anomalous administrative tool usage.
- Leverage AI-driven detection for correlating reconnaissance, credential abuse, and data exfiltration into cohesive incidents.
As Darktrace’s Autonomous Response demonstrated, rapid triage and containment can drastically reduce impact.
Organizations subscribing to managed detection and response services benefit from high-fidelity alerting, expedited investigation, and immediate mitigation, curbing the scope of Akira’s double-extortion tactics. Continuous vigilance—even post-patch—is paramount to thwart evolving ransomware threats exploiting legacy vulnerabilities.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
