North Korean threat actors have escalated their Contagious Interview campaign, deploying 338 malicious npm packages with over 50,000 downloads to target cryptocurrency and blockchain developers through sophisticated social engineering tactics.
The state-sponsored operation represents a significant evolution in supply chain attacks, utilizing more than 180 fake personas and a dozen command and control endpoints to deliver advanced malware including BeaverTail and InvisibleFerret backdoors.
Security researchers have identified this as a factory-style operation designed to compromise developer endpoints and steal cryptocurrency assets.
The Contagious Interview campaign follows a systematic approach based on the Lockheed Martin Cyber Kill Chain framework.
Threat actors begin with reconnaissance on LinkedIn, approaching targets who appear to be cryptocurrency developers, Web3 engineers, and blockchain specialists. The attackers pose as recruiters or hiring managers, screening potential victims for technical expertise and financial potential.
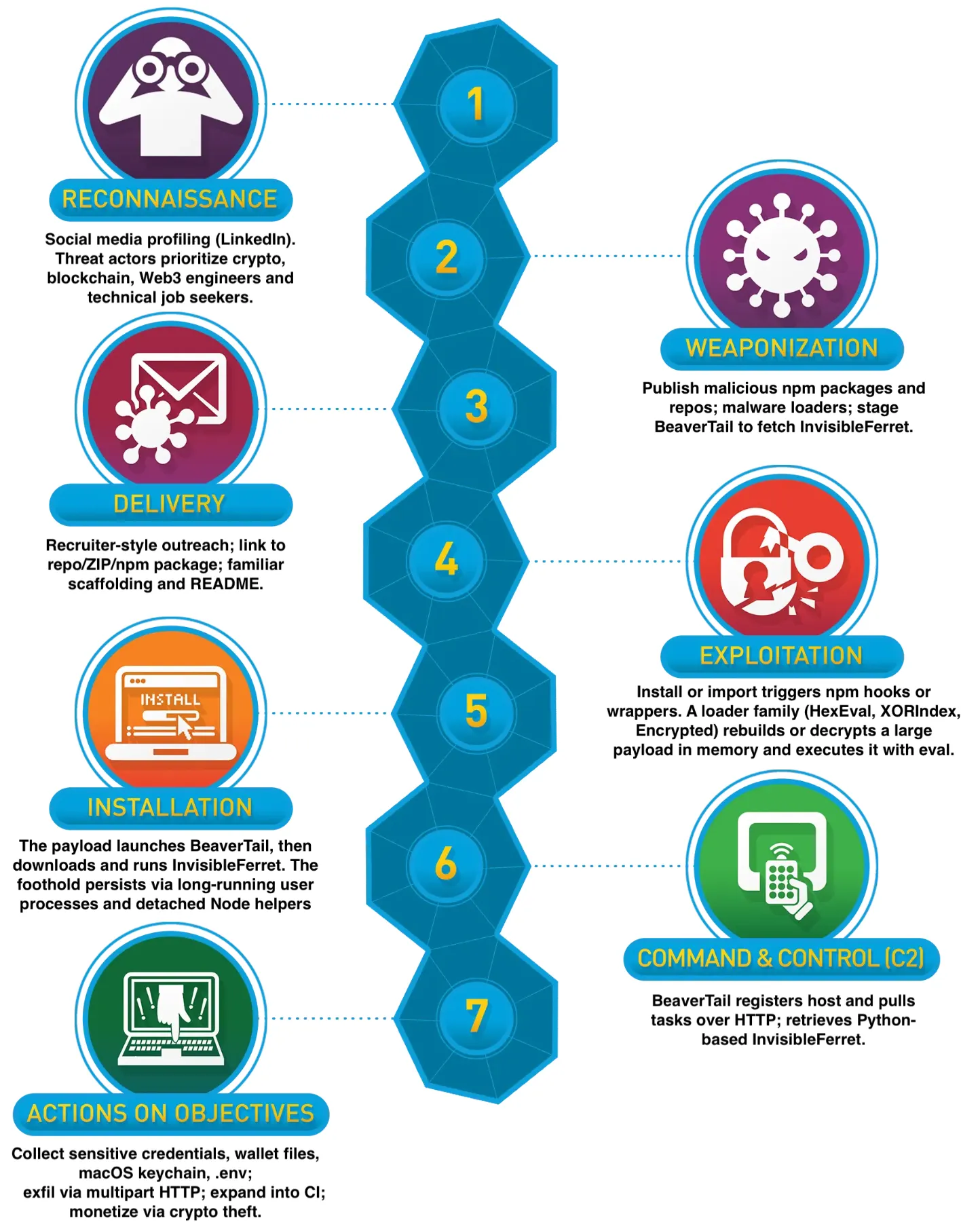
Victims typically receive job opportunity messages followed by coding assignments that require installing seemingly legitimate dependencies.
A recent case involved a software engineer who received a repository containing the malicious “eslint-detector” package, which appeared to be part of a routine recruitment test but contained encrypted payloads designed to steal credentials and wallet data.
The threat actors deliberately create time pressure around fake interview deadlines, encouraging victims to quickly run “npm install” commands without thorough security review.
Technical Evolution and Weaponization
The current wave demonstrates significant technical sophistication compared to earlier versions of the campaign.
Threat actors have moved beyond simple BeaverTail malware droppers to implement three distinct loader families: HexEval, XORIndex, and encrypted loaders.

The social engineering aspect proves particularly effective because it exploits the natural workflow of developers who regularly install dependencies during project setup.
Each variant executes during package installation or import, reconstructs obfuscated malware in memory, and typically fetches the InvisibleFerret backdoor for persistence.
The malicious packages target everyday dependencies that developers install automatically, particularly within the Node.js and Express ecosystem.
Attackers create typosquatted versions of popular packages including express, dotenv, body-parser, validator, cors, helmet, morgan, nodemailer, and nodemon. Examples include “epxreso” mimicking Express, “dotevn” imitating dotenv, and “boby_parser” targeting body-parser.
Beyond server utilities, the campaign specifically targets Web3 and cryptocurrency development tools.
Researchers have identified systematic typosquats of ethers.js (as “ethrs.js” and “ethres.js”), web3.js (as “we3.js” and “wb3.js”), and development frameworks like Truffle, Ganache, and Hardhat.
The attackers also create brand impersonation packages such as “metamask-api” to target cryptocurrency wallet developers.
Infrastructure and Persistence Mechanisms
The campaign’s command and control infrastructure combines raw IP addresses on commodity VPS providers with legitimate hosting platforms like Vercel to blend into normal developer traffic.
Communication occurs over HTTP/HTTPS and WebSocket protocols, with URI paths designed to appear work-related, such as “/api/ipcheck,” “/process-log,” and “/apikey.”
Installation creates long-running footholds rather than simple one-time compromises. The BeaverTail malware establishes persistent access and stages the InvisibleFerret backdoor, which operates across Windows, macOS, and Linux platforms.
This multi-stage approach allows threat actors to maintain access for extended periods while conducting reconnaissance and preparing for cryptocurrency theft.
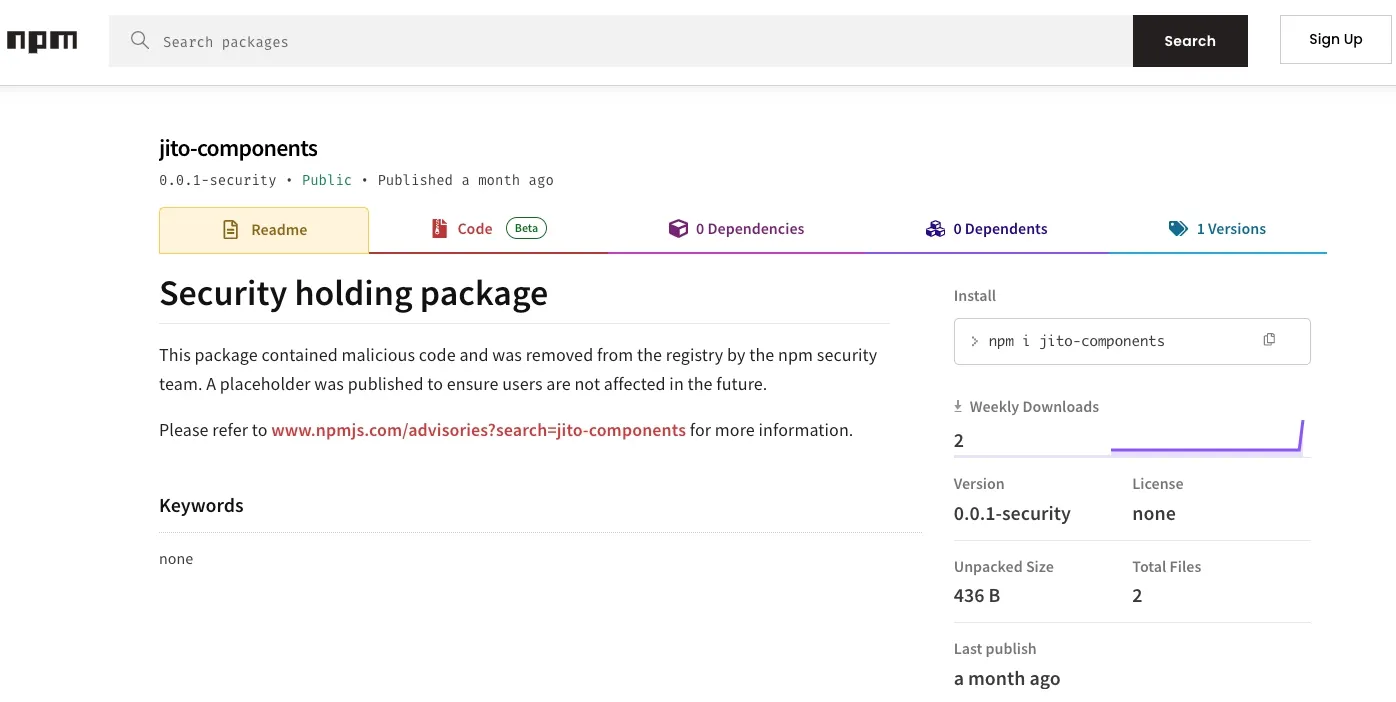
The campaign demonstrates remarkable persistence in the face of defensive measures. When security teams remove malicious packages, threat actors quickly upload new variants under different names.

The operation maintains weekly upload schedules, with researchers documenting consistent patterns of package submission, takedown, and re-upload cycles.
Independent reporting suggests North Korea-linked threat actors have already stolen over $2 billion in cryptocurrency during 2025, with the Contagious Interview campaign representing one vector in a broader strategy targeting the cryptocurrency ecosystem.
Stolen assets typically move through sophisticated laundering networks involving mixers, cross-chain swaps, and alternative blockchain networks including Bitcoin, Ethereum, BTTC, and Tron.
The scale and persistence of this campaign highlights the challenges facing the npm ecosystem and the broader software supply chain.
With 25 malicious packages remaining active at the time of analysis, the threat continues to evolve, requiring comprehensive defensive strategies that address both technical vulnerabilities and social engineering vectors targeting developer workflows.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
