Axis Communications, a leading provider of network video and surveillance solutions, has confirmed a critical vulnerability in its Autodesk® Revit® plugin that exposed Azure Storage Account credentials within signed DLLs.
Discovered in July 2024 by Trend Micro’s Zero Day Initiative (ZDI), the vulnerability allowed attackers to access and manipulate cloud assets belonging to Axis and its customers.
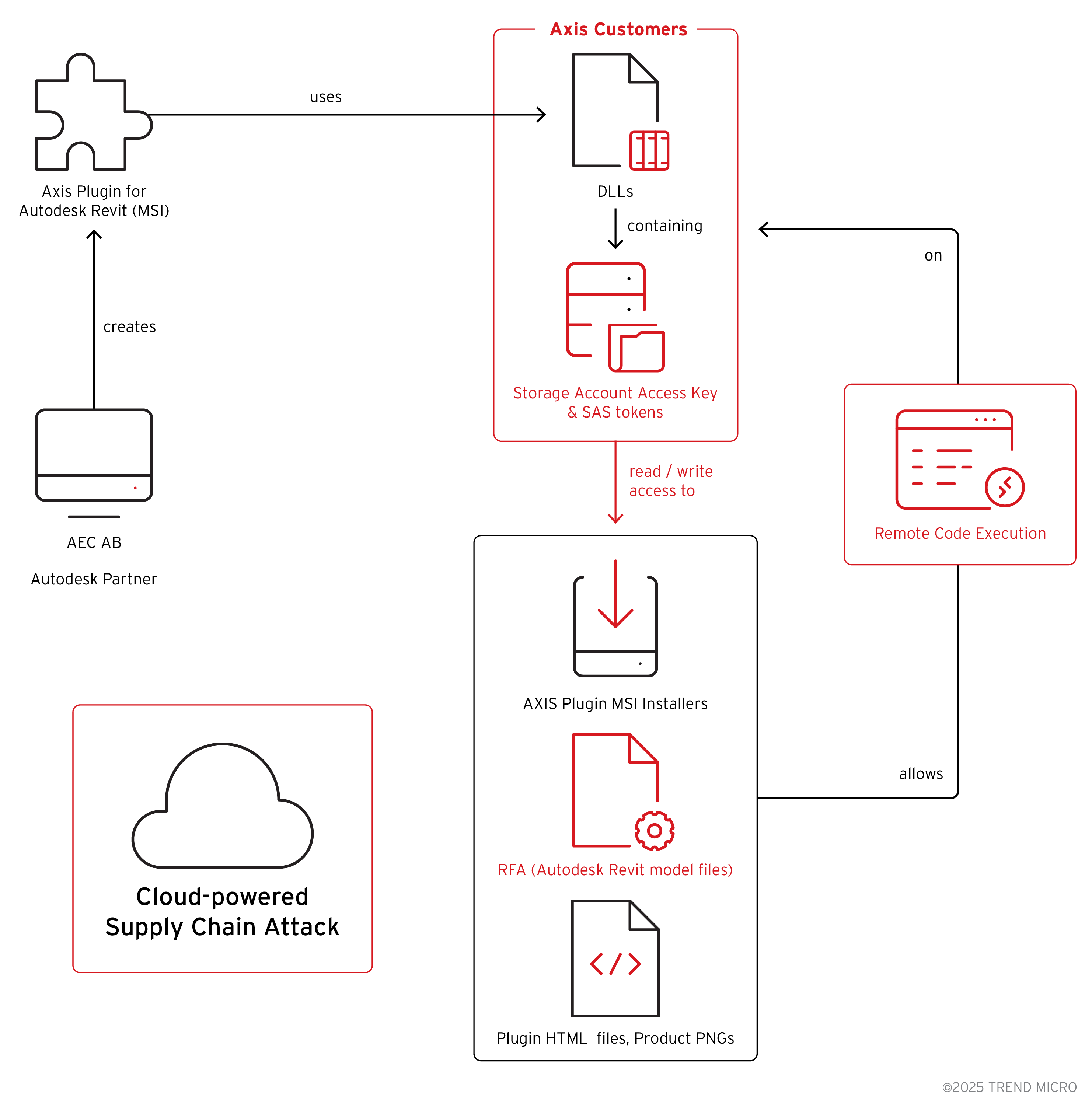
On July 8, 2024, ZDI researchers identified a digitally signed DLL, AzureBlobRestAPI.dll, bundled within the AXIS Plugin for Autodesk Revit.
This DLL, signed by AEC Advanced Engineering Computation AB—an Axis partner—contained cleartext Azure Shared Access Signature (SAS) tokens and access key pairs for two storage accounts named “axisfiles” and “axiscontentfiles.”
Embedding valid credentials in a private method of the DLL’s code allowed any user with the plugin installed to control those accounts, including reading, writing, and modifying stored resources.
Investigation revealed that both storage accounts hosted MSI installers for the Revit plugin and proprietary RFA model files for Axis products such as IP cameras and radars.

Because these installers and RFA files were distributed via the exposed storage accounts, any attacker could download the installers or tamper with model files used by architects and engineers in building information modelling workflows.
Vendor Response and Patch Evolution
Following disclosure under advisory ZDI-24-1181, Axis released version 25.3.710 of the plugin, which obscured credentials via .NET obfuscation.
However, tools like de4dot easily recovered the SAS tokens and access keys, leading to additional advisories ZDI-24-1328 and ZDI-24-1329.
In response, Axis issued version 25.3.711, removing storage account access keys entirely and embedding a read-only SAS token for a new account.
While this reduced privileges, the new token still permitted attackers to list and retrieve previous MSI installers—some of which contained the original, more permissive credentials.
The final advisory, ZDI-25-858, prompted Axis to revoke the original storage account keys and publish version 25.3.718 in March 2025.
This update eliminated embedded credentials and enforced least-privilege access, ensuring that only authorized customers could download plugin assets and model files.
Axis also removed all vulnerable plugin versions from its storage infrastructure and notified affected partners to upgrade immediately.
Supply Chain and RCE Risks
Beyond credential leaks, ZDI researchers examined potential repercussions of compromised RFA files. Revit family files serve as input for 3D modelling and have historically been prone to parser vulnerabilities.

Trend ZDI uncovered several vulnerabilities in Revit’s RFA handling that could enable remote code execution if an attacker replaced legitimate model files with malicious variants hosted on Axis’s storage accounts.
A successful exploitation chain could result in supply chain compromise, as malicious installers or altered RFA files distribute across engineering firms worldwide.

This incident echoes a 2023 case involving Microsoft’s PC Manager tool, where exposed SAS tokens allowed full control over WinGet packages, subdomains, and URL-shortening services.
Both examples underscore that signed binaries do not guarantee security and that credential exposure in customer-facing infrastructure can serve as a springboard for multi-stage attacks.
Axis Communications has fully patched the vulnerability with version 25.3.718. Nevertheless, the case highlights the need for continuous security review of third-party plugins, strict adherence to the principle of least privilege for cloud credentials, and rigorous file-format parsing safeguards.
Organizations leveraging cloud distribution mechanisms and third-party extensions must proactively validate trust, implement robust secret management, and monitor for anomalies to prevent supply chain exploits.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
