The online cybercrime marketplace, Russian Market, has evolved from selling Remote Desktop Protocol (RDP) access to becoming one of the most active underground hubs for information-stealing malware logs.
Stolen user credentials are traded daily, and each compromised login represents a potential gateway into corporate systems.
Threat actors routinely purchase credentials to launch credential-based attacks that put businesses, governments, and individuals at risk of account compromise and follow-on cyberattacks.
Several high-profile breaches have been traced back to credentials bought on marketplaces like Russian Market, demonstrated how a single exposed password can lead to significant data loss, financial damage, and reputational harm.
At its inception in early 2020, Russian Market specialized in selling RDP access and login credentials to compromised computers. Threat actors exploited this access for ransomware deployment, cyberespionage, and to pivot within target networks.
From 2020 until January 2024, when RDP sales were discontinued, the marketplace commoditized access to thousands of servers and workstations.
In 2021, operators shifted focus to stolen credit card data before launching the “Bots” product line later that year.
These “bots” are data logs exfiltrated from compromised machines—typically via information-stealing malware—and include harvested cookies, credentials, autofill data, and session tokens.
By the first half of 2025, over 180,000 infostealer logs were offered for sale. Three key vendors—Nu####ez, bl####ow, and Mo####yf—dominated the marketplace, accounting for nearly 70% of all bot listings.
Sellers employ a multi-stealer approach, leveraging malware variants such as Raccoon, Vidar, Lumma, RedLine, and Stealc. More recently, Rhadamanthys and Acreed have gained traction following law enforcement disruptions of Lumma Stealer infrastructure.
Anatomy of a Bot Sale
Within the “Logs” section, buyers can filter listings by geography, operating system, infostealer, and vendor.
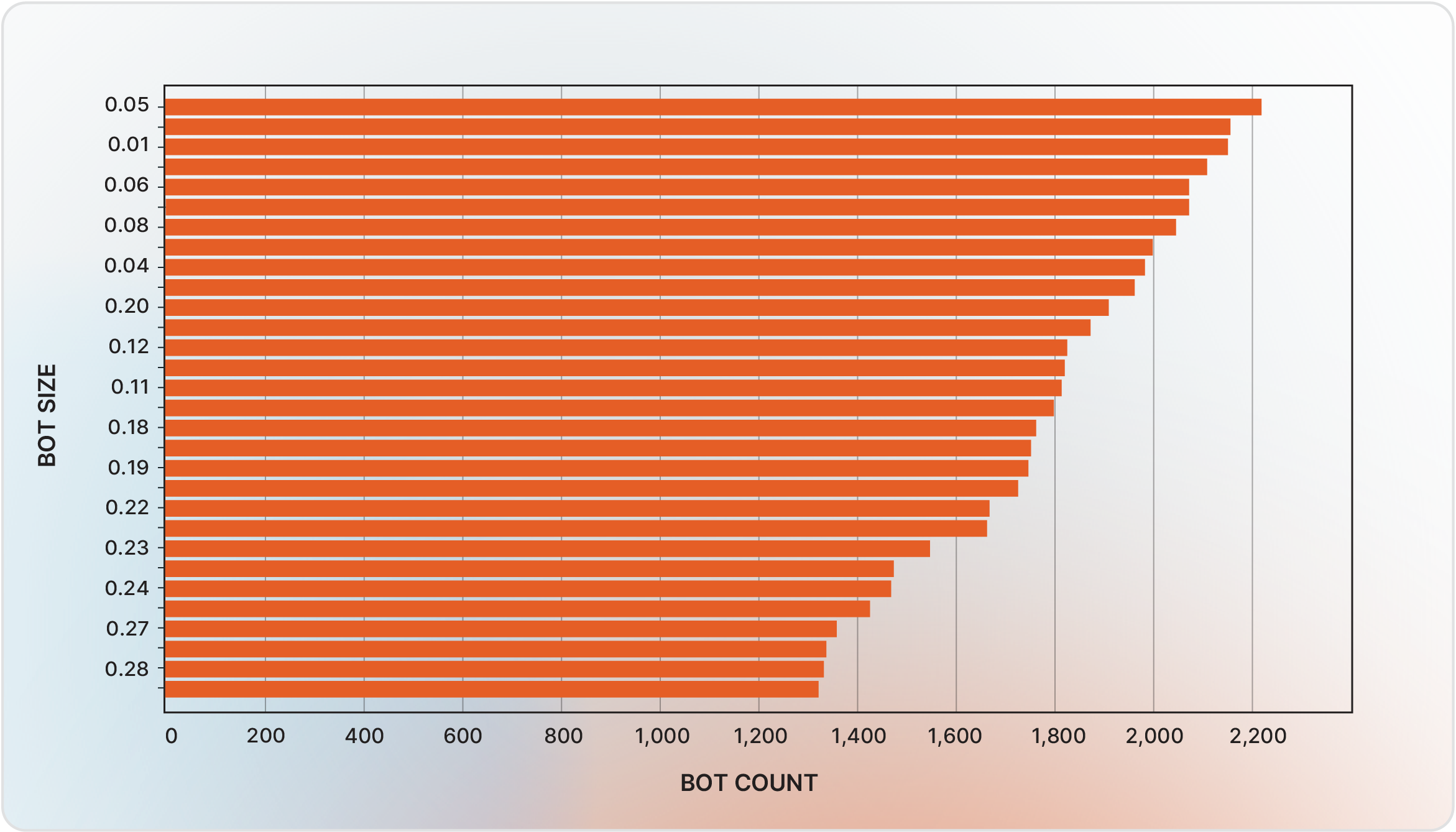
A typical bot contains credentials for multiple domains; its size—ranging from 0.05 to 0.3 megabytes—correlates with the number of harvested logins.
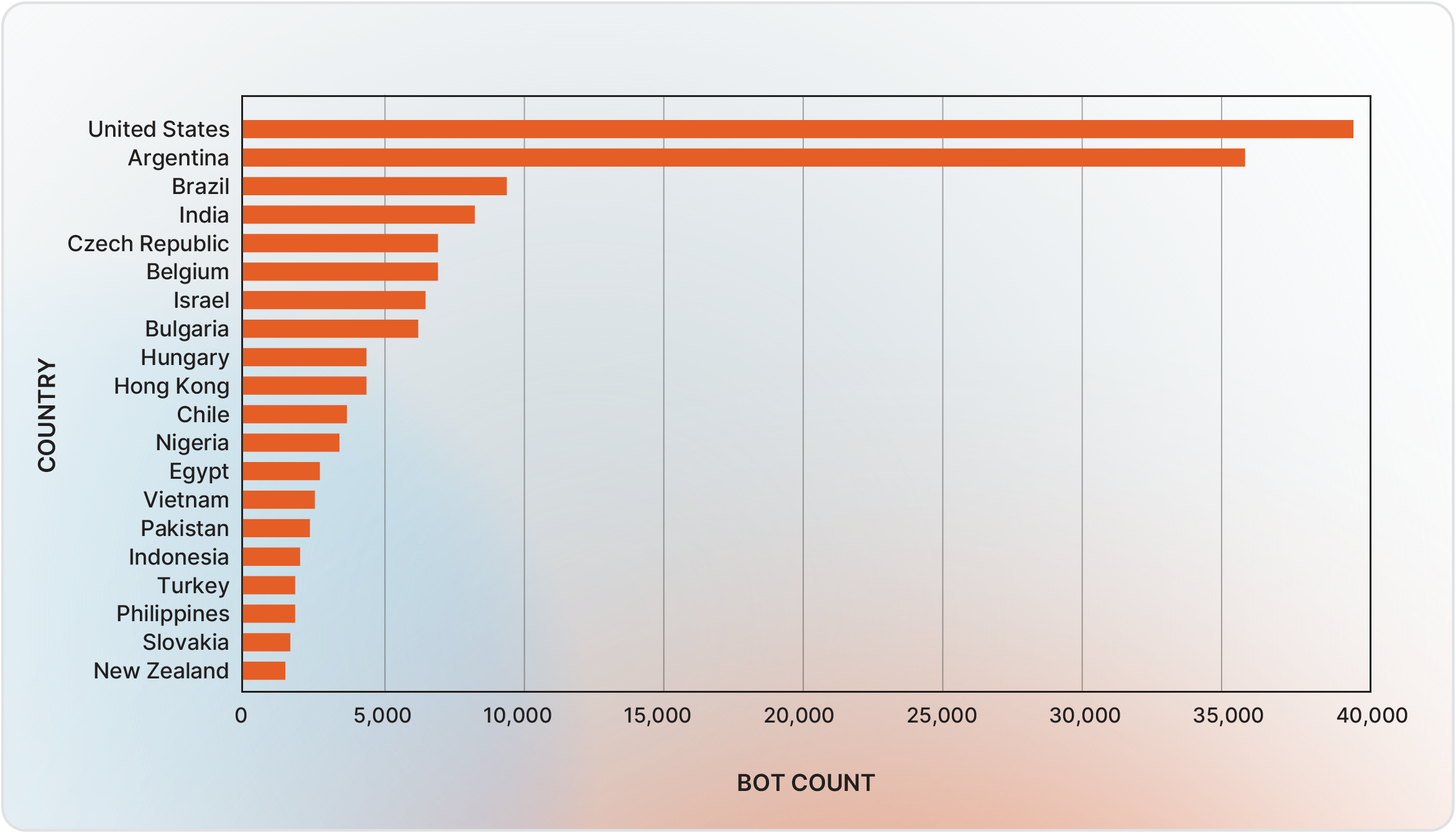

Bots predominantly target users in the United States (26%), Argentina (23%), and Brazil. In the first half of 2025, average bot size was 0.14 megabytes, and prices averaged $10 per bot, with historical ranges from $1 to $100 based on geolocation, session quality, and credential validity.

Example SQL-style query used by buyers to locate enterprise credentials:
sqlSELECT * FROM bots
WHERE domain LIKE '%examplecorp.com'
AND infostealer="Lumma"
AND country = 'US';
Each compromised login may represent access to webmail portals, cloud services, or VPN connections.
These stolen credentials enable threat actors to bypass perimeter defenses and launch email-based phishing or direct ransomware deployments under the guise of legitimate user activity.
Profiling Key Vendors
The infostealer ecosystem on Russian Market is anchored by a small number of prolific vendors. Nu####ez, active since January 2024, holds a “Diamond” status with a 4.41 rating and uses Lumma, Rhadamanthys, and Acreed in 2025.
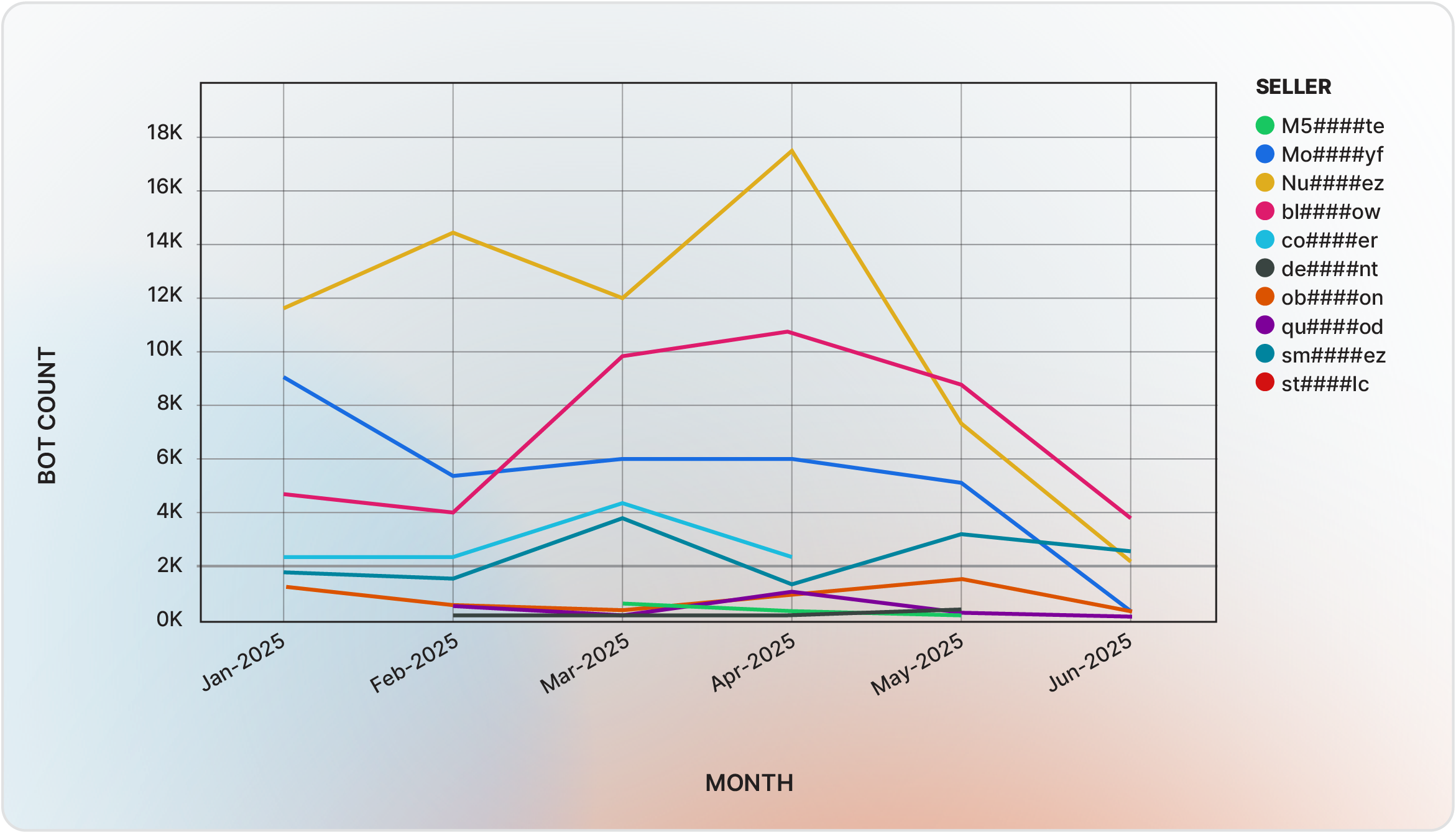

Bl####ow relies exclusively on Lumma, maintaining a 4.78 rating through October 2024. Mo####yf, initially a credit card seller, shifted to bots and achieved a 4.50 rating, leveraging Lumma after using Stealc and Vidar in 2024.
Newer entrants such as sm####ez and co####er have rapidly gained prominence with similar multi-stealer strategies.
Table 1 – Top Vendors by Market Share in H1 2025
| Vendor | Market Share | Primary Malware Variants |
|---|---|---|
| Nu####ez | 38% | Lumma, Rhadamanthys, Acreed |
| bl####ow | 24% | Lumma |
| Mo####yf | 19% | Lumma |
| sm####ez | 7% | Lumma, Vidar, Stealc |
| co####er | 4% | Lumma, Stealc |
Information-stealing malware fuels a thriving underground economy by providing the raw material for credential-based intrusions.
Unlike forums such as BreachForums and XSS that have been disrupted, Russian Market has maintained continuous operations, demonstrating its resilience and adaptability.
Organizations must strengthen defenses by enforcing multi-factor authentication, implementing continuous credential monitoring, and integrating threat intelligence feeds to detect anomalous login activity.
Profiling key vendors and infostealer variants provides a rare inside look at Russian Market’s operations, underscoring the urgency for businesses to act now to prevent exposure of employee credentials and mitigate the risk of devastating follow-on attacks.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
