In September, a nascent pro-Russian hacktivist group known as TwoNet staged its first operational technology and industrial control systems (OT/ICS) intrusion against our water treatment utility honeypot.
By exploiting default credentials and SQL-based schema extraction, the adversary ultimately created backdoor accounts and defaced the human-machine interface (HMI), demonstrating a concerning pivot from pure DDoS to targeted utility attacks.
This incident underscores the growing imperative for critical infrastructure organizations—especially utilities—to deploy high-fidelity deception technologies and vigilant monitoring of hacktivist channels for accurate threat intelligence.
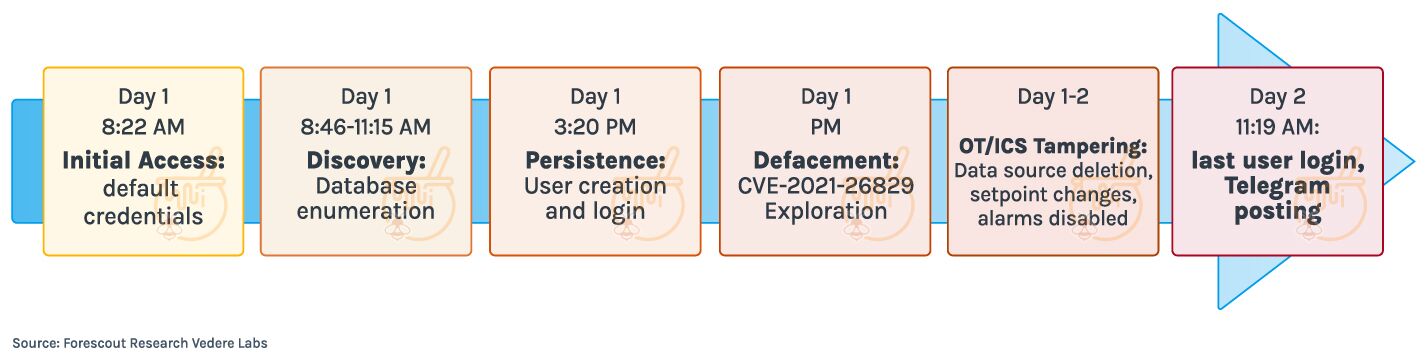
The attack commenced at 08:22 AM UTC on a September day, originating from IP 45.157.234[.]199 registered to AS58212 (dataforest GmbH).
Initial access was gained via default HMI credentials (admin/admin). Through the HMI’s sql.shtm interface, the attacker launched two rounds of SQL reconnaissance. The first queries, attempting to enumerate primary keys, failed; the second queries successfully extracted table and column metadata:
sqlSELECT t.TABLENAME, c.COLUMNNAME, c.COLUMNNUMBER, c.COLUMNDATATYPE, c.COLUMNDEFAULT, c.AUTOINCREMENTVALUE, c.AUTOINCREMENTSTART, c.AUTOINCREMENTINC
FROM sys.systables t
JOIN sys.syscolumns c ON t.TABLEID = c.REFERENCEID
WHERE t.tabletype="T"
ORDER BY t.TABLENAME, c.COLUMNNUMBER;
SELECT t.TABLENAME, con.CONSTRAINTNAME, con.TYPE
FROM sys.systables t
JOIN sys.sysconstraints con ON t.TABLEID = con.TABLEID
ORDER BY t.TABLENAME;
Evidence suggests these commands were entered manually, underscoring the attacker’s familiarity with HMI web interfaces and SQL schema structures.
The threat actor’s user-agent string, “Mozilla/5.0 (X11; Linux x86_64; rv:140.0) Gecko/20100101 Firefox/140.0”, indicates a Linux-based Firefox workflow, though spoofing remains possible.
Defacement, Disruption, and Credential Exfiltration
Approximately seven hours after initial compromise, the adversary created a new HMI user account—“BARLATI”—and executed four distinct actions before the intrusion concluded the next morning.

First, leveraging CVE-2021-26829, the attacker altered the HMI login page description to:
xml This defacement triggered a pop-up alert whenever the login page loaded. Next, the attacker deleted configured PLC data sources, halting real-time updates.
In a further manipulation, PLC setpoints were adjusted via the HMI, while system settings were modified to disable logs and alarms.
Notably, the attacker focused solely on the web application layer, making no attempts to escalate privileges or exploit underlying host components.
Broader Implications
TwoNet emerged in January 2025 and initially operated DDoS campaigns using the MegaMedusa Machine malware.
Its pivot to OT/ICS targeting coincides with the launch of a new Telegram channel on September 14, where it publicly claimed this water-utility intrusion and other attacks against solar-plant and biomass-boiler control panels across Europe.

TwoNet’s activity reflects a broader hacktivist trend: groups using alliances—such as OverFlame and CyberTroops—to exchange tooling, intelligence, and access, accelerating capability growth.
Despite flamboyant claims, honeypot deployments reveal frequent false starts and misdirection.
In this case, the water-treatment honeypot provided concrete IoCs, clarifying TTPs versus hacktivist exaggeration. Utilities remain attractive due to lagging security budgets and exposure of OT/ICS devices online.
Honeypot intelligence remains indispensable as hacktivists expand beyond DDoS to OT/ICS. By blending deception feeds into security operations, critical infrastructure entities can distinguish real threats from empty posturing, track evolving alliances, and mitigate risks to water, power, and other utility environments.
Vigilance, combined with deceptive counters, will be essential to safeguard industrial systems against the next wave of hacktivist-driven disruptions.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
