A novel phishing campaign has emerged targeting Colombian users by abusing judicial notifications and weaponizing Scalable Vector Graphics (SVG) files.
This sophisticated attack begins with a carefully crafted Spanish-language email impersonating the “17th Municipal Civil Court of the Bogotá Circuit,” complete with formal legal language and institutional details.
The .SVG attachment named “Fiscalia General De La Nacion Juzgado Civil 17.svg” lures recipients into initiating a multi-stage infection chain that ultimately delivers the AsyncRAT remote access Trojan (RAT) via in-memory injection into a trusted Windows process.
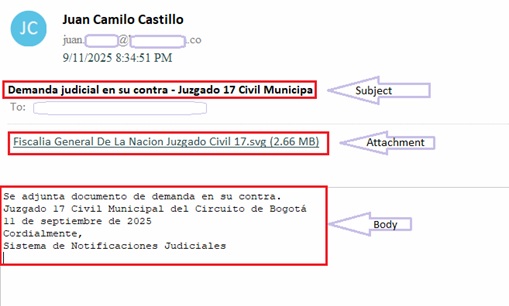
The phishing email replicates the style of an official court notice, referencing Bogotá’s municipal civil court and presenting a false notification of legal action.
Its body reads in Spanish: “Adjunta demanda presentada en su contra. Juzgado 17 Civil Municipal del Circuito de Bogotá. 11 de septiembre de 2025. Atentamente, Sistema de Notificaciones Judiciales.”


By invoking the capital’s judicial system, the attackers exploit geographic trust cues to bypass initial suspicion. The attached SVG file, unlike pixel-based formats, contains XML-based instructions that include an onclick handler:
When the user clicks the image, the embedded JavaScript decodes a Base64-encoded HTML blob, opens it as a fake “Attorney General’s Office” consultation portal, and prompts the victim to download an HTA file masquerading as an official document.
Multi-stage Dropper Chain
Upon clicking “DOWNLOAD DOCUMENTO_OFICIAL_JUZGADO.HTA,” the user unwittingly executes a client-side dropper. The HTA hides its malicious payload within junk code and decodes a large Base64 block into actualiza.vbs.
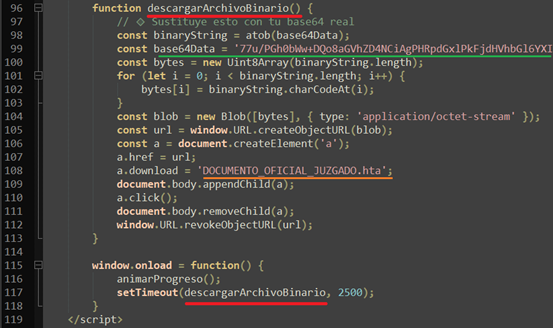

This Visual Basic script writes and runs a PowerShell downloader (veooZ.ps1), which fetches a text file (Ysemg.txt) from an attacker-controlled server.
The script cleans and decodes the file by replacing placeholder characters, producing classlibrary3.dll.
The .NET DLL functions as a module loader: it decodes and writes an injector component, retrieves the AsyncRAT payload, and uses .NET reflection to inject AsyncRAT into MSBuild.exe.
To avoid sandbox detection, the loader checks for VirtualBox and VMware processes and aborts if it detects analysis environments.
It also supports optional persistence methods—registry Run keys or startup shortcuts—though in this campaign the registry method was disabled.
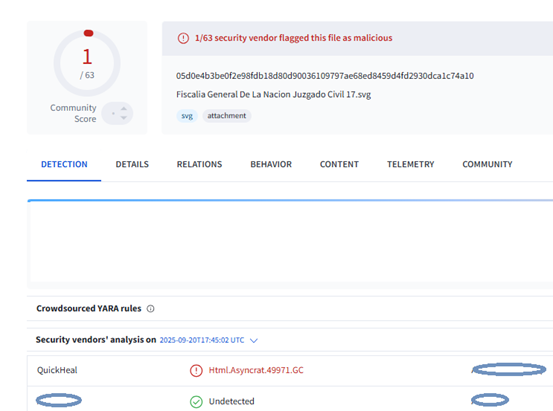

During the time of analysis of this campaign, the SVG file in attachment was detected by QuickHeal/Seqrite.
Security teams noted for unusual SVG behaviors and enforcing strict email attachment policies are essential to defend against such multifaceted threats.
AsyncRAT Payload Capabilities
AsyncRAT arrives as a .NET executable and executes entirely in memory within the context of MSBuild.exe. It begins by gathering system details—hardware identifiers, operating system version, user privileges, installed antivirus products, and webcam availability.
The file is heavily obfuscated and uses XOR’ing and shifting operations loop to decode these obfuscated values.

It checks for elevated privileges to determine persistence strategy: creating a scheduled task when running as administrator or writing to HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun otherwise.
The RAT employs anti-analysis and anti-VM checks, including AMSI bypass techniques, and searches for monitoring tools (Taskmgr.exe, ProcessHacker.exe) to terminate them.
It establishes a TLS-encrypted channel to its command-and-control server, dynamically loads plugins, and exfiltrates stolen data packaged with MessagePack. AsyncRAT also supports keylogging, file management, remote shell execution, and webcam surveillance.
By hiding malicious code in an SVG and chaining through HTA, VBS, and PowerShell, this campaign successfully bypasses many traditional defenses.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.