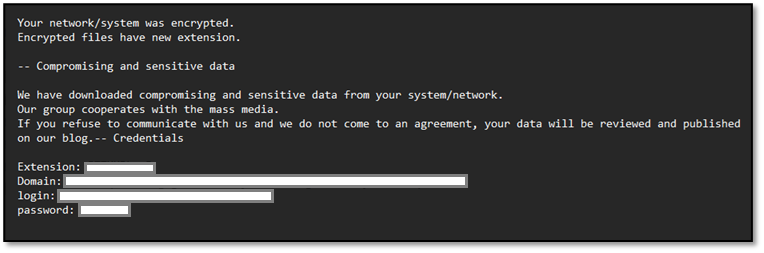
The Agenda ransomware group has evolved its attack methodology with a sophisticated technique that deploys Linux ransomware variants directly on Windows systems, challenging traditional endpoint security controls.
The attack represents a significant tactical evolution in ransomware deployment strategies. Threat actors utilized WinSCP for secure file transfer to move Linux ransomware binaries onto Windows machines, then leveraged Splashtop Remote management software to execute the cross-platform payload directly on Windows systems.
Trend Micro Research uncovered this advanced attack campaign that specifically targets VMware infrastructure and backup systems, combining legitimate remote management tools with bring-your-own-vulnerable-driver (BYOVD) techniques to evade detection and encrypt hybrid enterprise environments.
This unconventional approach bypasses most endpoint detection systems that are configured primarily to monitor native Windows executables rather than Linux binaries running through remote management channels.

The attack chain began with fake CAPTCHA pages hosted on Cloudflare R2 storage infrastructure that delivered information-stealing malware to harvest credentials and authentication tokens.
Once inside the network, attackers installed multiple remote management tools including AnyDesk through ATERA Networks’ RMM platform and ScreenConnect for command execution, creating redundant access channels that appeared legitimate to security monitoring systems. The strategic abuse of trusted IT tools allowed threat actors to blend malicious activity with normal administrative operations.
Systematic Targeting of Backup Infrastructure
A defining characteristic of this campaign was the deliberate targeting of Veeam backup systems to compromise disaster recovery capabilities before deploying ransomware.
However, testing confirmed successful loading when placed alongside compatible binaries, such as FoxitPDFReader.exe, which imports msimg32.dll as a dependency.

Attackers executed PowerShell scripts with base64-encoded payloads to systematically extract and decrypt stored credentials from multiple Veeam backup databases.
These databases contained authentication credentials for domain controllers, Exchange servers, SQL databases, and file servers across the enterprise infrastructure.
By harvesting credentials from backup systems, the Agenda group gained comprehensive access to remote systems while simultaneously compromising the organization’s ability to recover from the ransomware attack.
The threat actors queried specific database tables including Credentials, BackupRepositories, and WinServers to collect domain administrator accounts, service accounts, and local administrator credentials.
This approach demonstrated advanced operational planning focused on ensuring successful encryption while eliminating recovery options.
The attackers deployed multiple vulnerable drivers to disable security solutions and evade detection mechanisms.
Analysis revealed the use of eskle.sys, a driver digitally signed by a Beijing-based gaming technology company, commonly repurposed by threat actors from game cheat development tools.
The driver provided kernel-level access to terminate security processes, detect virtual machine environments, and implement anti-debugging countermeasures.
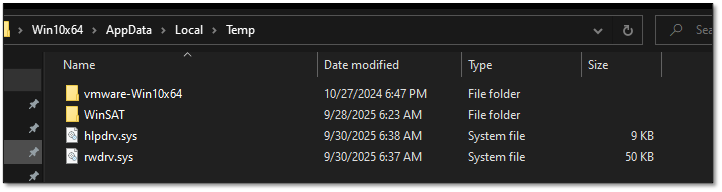
Additional BYOVD tools included msimg32.dll, which employed DLL sideloading techniques to drop rwdrv.sys and hlpdrv.sys drivers previously documented in Akira ransomware campaigns.
Analysis of the Linux ransomware binary revealed an advanced cross-platform payload with extensive configuration capabilities and platform-specific targeting.

These drivers enabled the termination of endpoint detection and response solutions at the kernel level.
The attackers also deployed multiple SOCKS proxy instances disguised within directories of legitimate enterprise software from Veeam, VMware, and Adobe, creating distributed command-and-control channels that obfuscated malicious traffic within normal application communications.
Global Impact and Victimology Patterns
Agenda emerged as one of the most active ransomware-as-a-service operations in 2025, demonstrating unprecedented operational tempo with victims documented across the United States, Western Europe, and Japan.
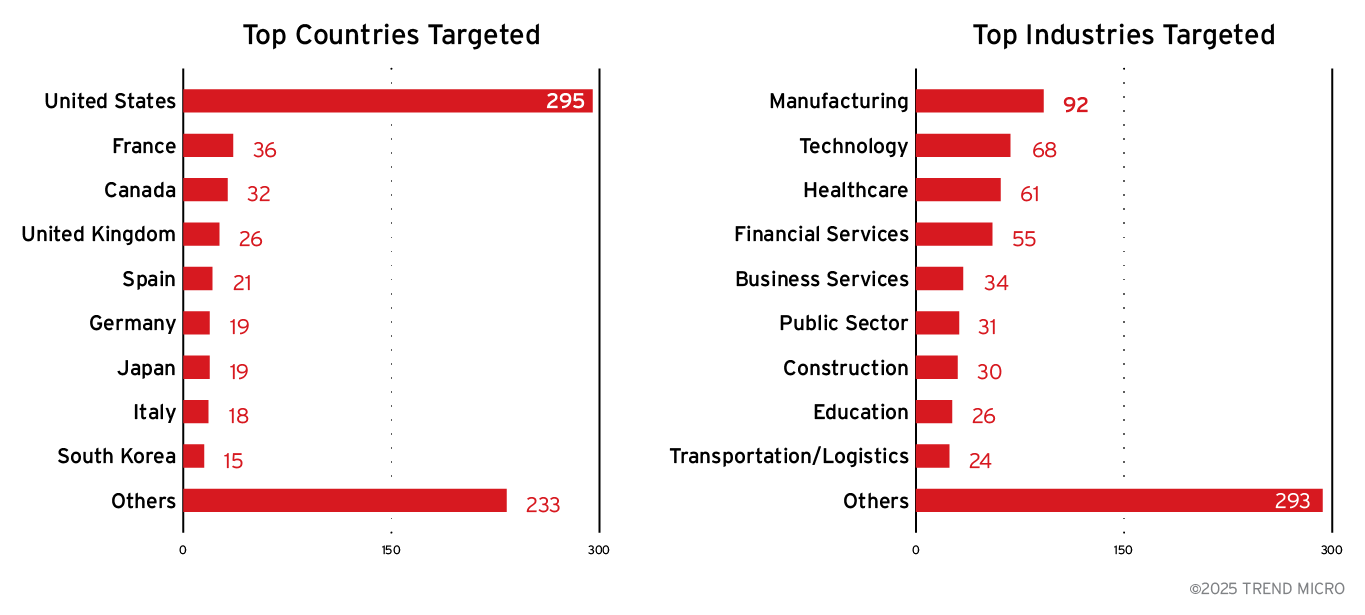

Analysis of the group’s data leak site revealed opportunistic targeting of high-value sectors including manufacturing, technology, financial services, and healthcare.
The victimology pattern indicates threat actors prioritize industries with operational sensitivity, data criticality, and higher likelihood of ransom payment.
The group’s willingness to target critical infrastructure and healthcare facilities emphasizes their prioritization of financial gain over societal impact.
The geographic and sectoral distribution shows a sophisticated understanding of which organizations are most vulnerable to operational disruption and most likely to pay ransom demands to restore business operations quickly.
This attack methodology challenges conventional security architectures built primarily around Windows-focused controls.
The execution of Linux binaries through legitimate remote management tools on Windows platforms represents a significant blind spot in most enterprise security programs.
Organizations must urgently reassess their security posture to account for hybrid environment threats and cross-platform ransomware deployment techniques.
Security teams should implement enhanced monitoring of remote management tools, restrict RMM platforms to authorized hosts, and enforce multifactor authentication on all administrative access.
Critical backup infrastructure must be segmented from production networks with the principle of least privilege strictly enforced on credential access.
Detection rules should be expanded to identify unsigned driver loads, DLL sideloading attempts, and Linux binary execution on Windows systems through remote administration tools.
The Agenda ransomware campaign demonstrates that threat actors are adapting faster than many organizations’ security controls.
The combination of BYOVD techniques, legitimate tool abuse, backup infrastructure targeting, and cross-platform execution methods creates a formidable attack vector that requires comprehensive visibility across hybrid Windows and Linux environments to detect and prevent successfully.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
