In March 2025, security researchers at Kaspersky detected a sophisticated campaign exploiting a previously unknown Chrome vulnerability to deliver advanced spyware to high-profile targets.
The attack, dubbed Operation ForumTroll, leveraged personalized phishing links to compromise organizations across Russia, including media outlets, universities, research centers, government agencies, and financial institutions.
A single click on a malicious link was sufficient to trigger infection through Google Chrome or any Chromium-based web browser.
The attackers demonstrated remarkable operational security by crafting extremely short-lived personalized links designed to evade detection systems.
However, Kaspersky’s threat intelligence team identified a complex zero-day sandbox escape exploit embedded within the infection chain.
The vulnerability, tracked as CVE-2025-2783, was subsequently reported to Google and patched in Chrome 134.0.6998.177/.178.
The discovery highlights a previously unknown attack surface in modern browser architecture that threat actors had been actively weaponizing against critical infrastructure and government organizations.
The Attack Infrastructure
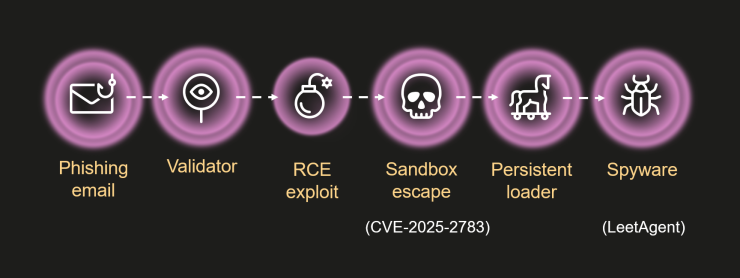
Operation ForumTroll used a multi-stage infection chain that began with convincing spear-phishing emails masquerading as invitations to the prestigious Primakov Readings forum.
These lures contained personalized links directing victims to malicious websites that verified targets before executing the exploit.
The attackers demonstrated sophistication by employing advanced obfuscation techniques and leveraging legitimate infrastructure providers to host command and control servers.
The infection process required no additional user interaction beyond clicking the malicious link. Once a victim visited the compromised website, the attack chain initiated automatically, silently escaping Chrome’s sandbox protections and establishing persistent access to the infected system.
Kaspersky researchers were unable to fully recover the exploit code from compromised infrastructure, as the attackers had sanitized their deployment servers by the time the investigation began.
However, telemetry from the initial infection waves provided sufficient artifacts to reconstruct the attack methodology.
Unmasking the Sandbox Escape
CVE-2025-2783 represents one of the most intriguing sandbox escape vulnerabilities discovered in recent years.
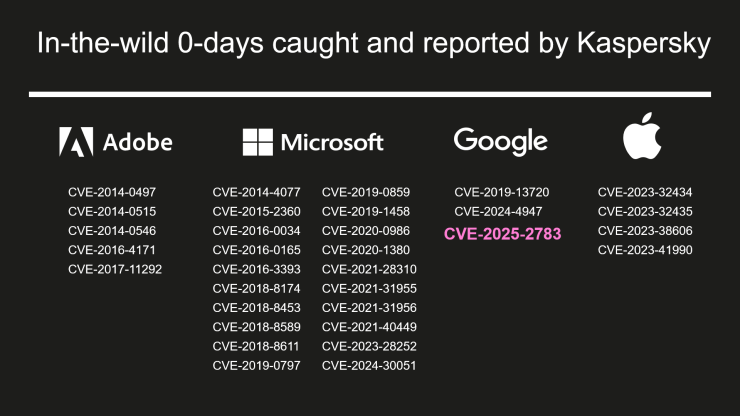

The exploit leveraged an obscure Windows operating system quirk that Chrome security architecture had failed to address.
The vulnerability stemmed from mishandling of pseudo handles—special constants returned by Windows API functions like GetCurrentThread and GetCurrentProcess that are interpreted differently by the kernel than standard process handles.
In addition to VMProtect’s anti-debugging techniques, Dante uses some common methods to detect debuggers.
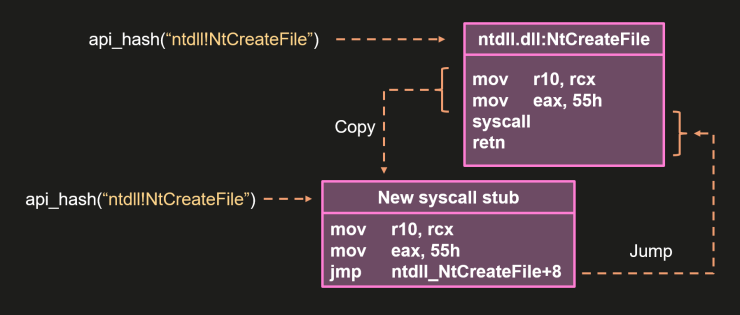

Chrome’s IPC code had previously checked for pseudo handles valued at -1 (INVALID_HANDLE_VALUE), but developers overlooked the -2 constant representing the current thread.
This oversight enabled attackers to relay pseudo handles through Chrome’s message relay system, where the broker would convert the -2 constant into an actual thread handle belonging to the browser process itself.
The renderer process then received a legitimate handle to the browser’s main thread, bypassing all sandbox restrictions.
The exploit demonstrated exceptional technical sophistication by utilizing statically compiled Mojo and ipcz libraries to communicate with the IPC broker, eliminating the need for manual message crafting.
Attackers could then execute arbitrary shellcode within the privileged browser process by suspending the hijacked thread, modifying register values, and resuming execution.
Kaspersky’s investigation traced the ForumTroll campaign back to 2022, uncovering a toolset developed by Memento Labs—the Italian company formerly known as Hacking Team.
The researchers identified previously unknown commercial spyware called Dante, which had remained undetected for years following Hacking Team’s rebrand.

Similarities in code patterns strongly suggest that Operation ForumTroll employed the complete Dante toolset alongside custom exploitation capabilities.
The discovery emphasizes the persistent threat posed by commercial spyware vendors to governmental and organizational security.
Firefox developers subsequently identified similar vulnerability patterns in their IPC code, releasing patch CVE-2025-2857 to address comparable issues.
Organizations should immediately update all Chromium-based browsers and review network logs for suspicious activity originating from March 2025 or earlier.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
