The North Korean-linked threat group BlueNoroff, also known by aliases including Sapphire Sleet, APT38, and Alluring Pisces, continues to evolve its attack tactics while maintaining its primary focus on financial gain.
The group has shifted its strategy to employ sophisticated new infiltration methods targeting high-value victims including C-level executives, managers, and blockchain developers within the Web3 and venture capital sectors.
Security researchers have identified two distinct campaigns, dubbed GhostCall and GhostHire, which showcase the actor’s increasing sophistication and use of social engineering techniques combined with advanced malware delivery mechanisms.paste.txt
The GhostCall campaign represents one of BlueNoroff’s most deceptive operations, leveraging carefully crafted phishing tactics to compromise macOS systems used by executives at technology companies and venture capital firms.
The attack begins on Telegram, where threat actors impersonate venture capitalists or use compromised accounts of legitimate entrepreneurs to establish contact with targets.
They pitch lucrative investment or partnership opportunities, then use Calendly to schedule fake meetings with links pointing to domains that mimic legitimate Zoom interfaces.paste.txt
Upon visiting these malicious domains, victims encounter a meticulously designed interface that mirrors Zoom’s appearance.
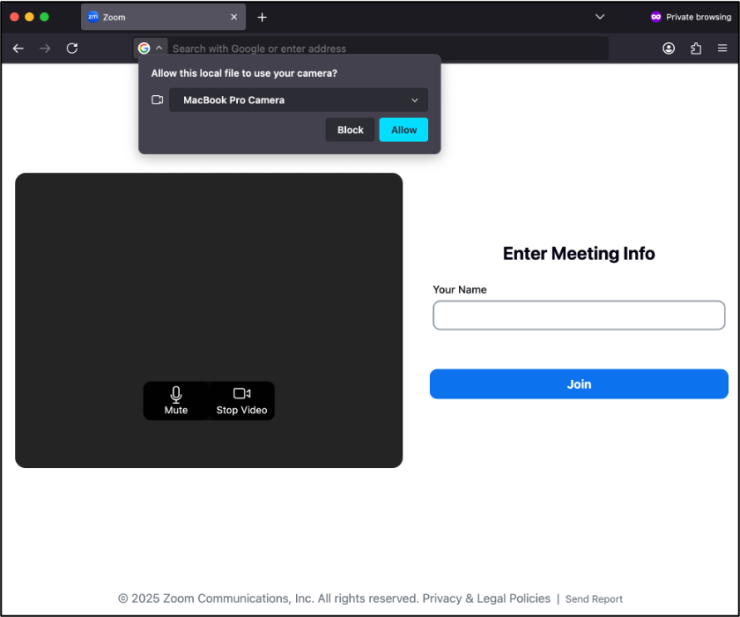
The page prompts users to enable their cameras and enter their names, but instead of joining a genuine video call, victims are presented with what appears to be a live meeting with three participants.
The critical deception lies in the videos displayed—rather than deepfakes or AI-generated content as many victims initially believed, these are actual recordings secretly captured from previous victims.
The actor also occasionally uses Telegram’s hyperlink feature to hide phishing URLs and disguise them as legitimate URLs.
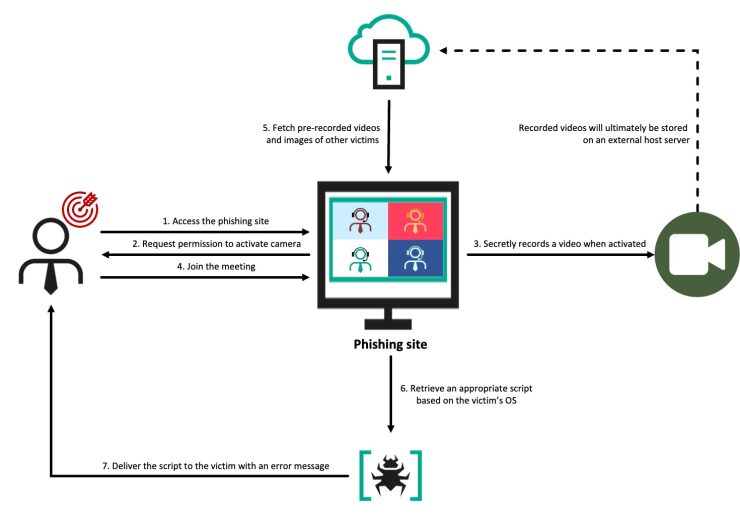

The attacker-controlled infrastructure stores these webcam recordings and replays them to new targets, creating a convincing illusion of a real meeting.paste.txt
From Video Calls to Malware Infection
After the fake call concludes, victims are directed through a series of social engineering steps designed to achieve malware installation.
ZoomClutch steals macOS passwords by displaying a fake Zoom dialog, then sends the captured credentials to the C2 server.
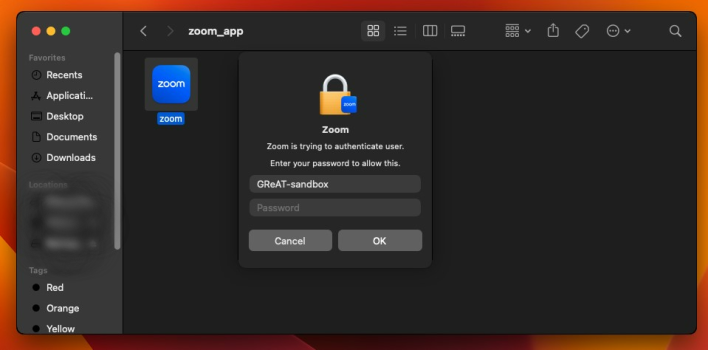

The threat actors shift blame from technical issues to audio problems, convincing targets to download and execute malicious AppleScript code disguised as Zoom client updates.
This marks the transition from initial compromise to full system infection, with the scripts downloading ZIP files containing multi-component malware chains tailored to the victim’s operating system.paste.txt
Complementing the GhostCall campaign is GhostHire, which targets Web3 developers through fraudulent recruitment processes.
BlueNoroff actors pose as legitimate recruiters, conducting initial screening calls before adding potential victims to Telegram bots.
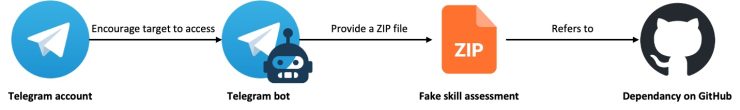

These bots then distribute either ZIP files or GitHub repository links containing malicious code, framed as technical assessments.
Victims face artificial time pressure—30-minute deadlines to complete tasks—encouraging quick execution of the malicious payloads. The malware automatically selects appropriate infection chains based on the user agent identifying the victim’s operating system.paste.txt
Advanced Capabilities and Intelligence Gathering
Researchers have identified seven distinct multi-component infection chains deployed across both campaigns, accompanied by sophisticated stealer suites and keyloggers.
These malware components extract extensive sensitive information including cryptocurrency wallet credentials, Keychain data, API keys for cloud services like OpenAI, DevOps infrastructure credentials, browser-stored passwords, and authentication tokens from messaging applications including Telegram.paste.txt
BlueNoroff’s integration of artificial intelligence throughout these campaigns demonstrates the group’s investment in scaling operations while maintaining precision in targeting and attack execution.
The organization has been tracked conducting these operations since at least April 2025, with continuous victim sightings reported across social media platforms.
Security researchers emphasize that understanding these sophisticated tactics is critical for protecting organizational leadership and developers working within the blockchain ecosystem from these highly persistent financial-motivated threats.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
