A sophisticated cybercrime campaign leveraging Near Field Communication technology has exploded across multiple continents, with researchers at zLabs identifying over 760 malicious Android applications designed to steal banking credentials and facilitate fraudulent transactions.
What initially appeared as isolated incidents in April 2024 has evolved into a large-scale threat operation targeting financial institutions across Russia, Poland, the Czech Republic, Slovakia, Brazil, and beyond.
The malware ecosystem operates through an extensive infrastructure comprising more than 70 command-and-control servers, dozens of private Telegram channels for data exfiltration, and applications impersonating approximately 20 legitimate banking institutions and government services.
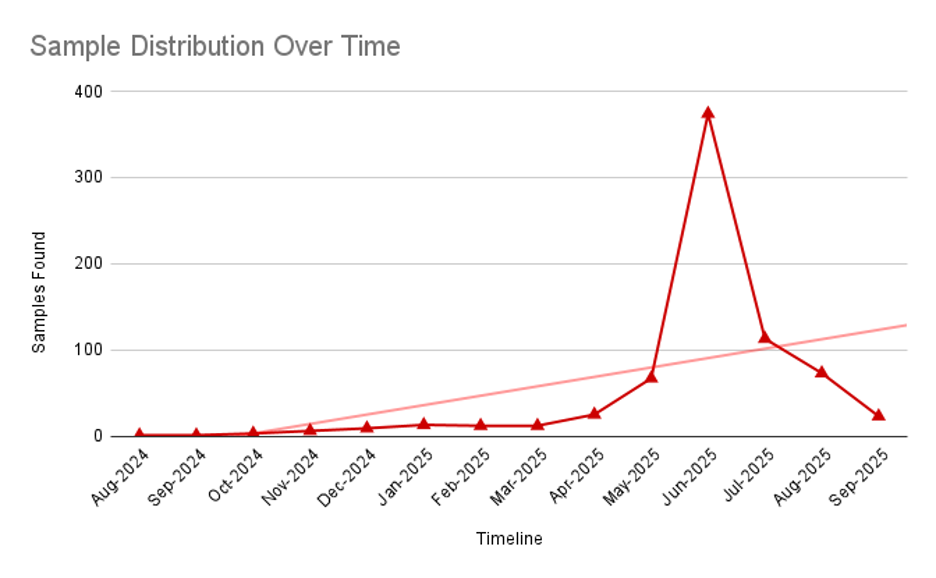
Security researchers monitoring these campaigns have documented a steady increase in malicious samples throughout 2024, indicating that threat actors are continuously refining their techniques and expanding their geographic reach.
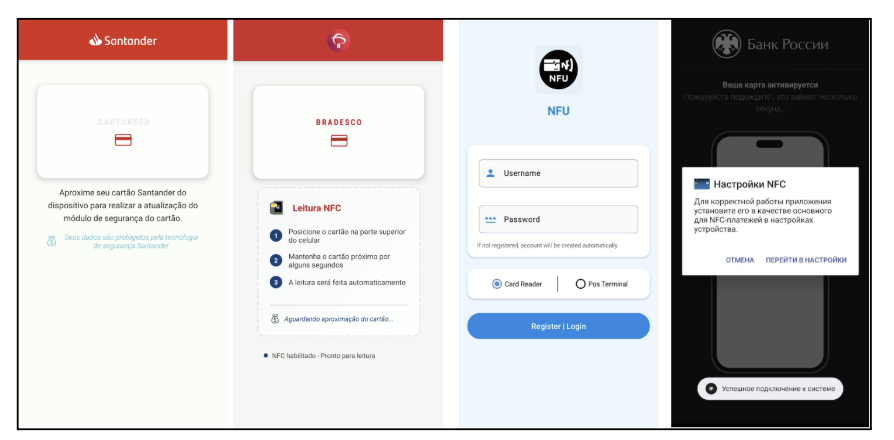
These malicious applications employ social engineering by masquerading as legitimate services from major financial institutions and government agencies.
Threat actors have impersonated prominent organizations including VTB Bank, Tinkoff Bank, Santander, PKO Bank Polski, Bradesco, Itaú, and even government services like Russia’s Gosuslugi portal and regulatory bodies such as the Central Bank of Russia and National Bank of Slovakia.
By replicating the branding and interfaces of these trusted entities, attackers successfully trick victims into granting the applications dangerous NFC permissions.
The malware leverages Android’s Host Card Emulation functionality to intercept payment data when users attempt contactless transactions.
Once installed, these applications request to become the default NFC payment method while displaying convincing full-screen banking interfaces—often rendered within WebViews to enhance authenticity.
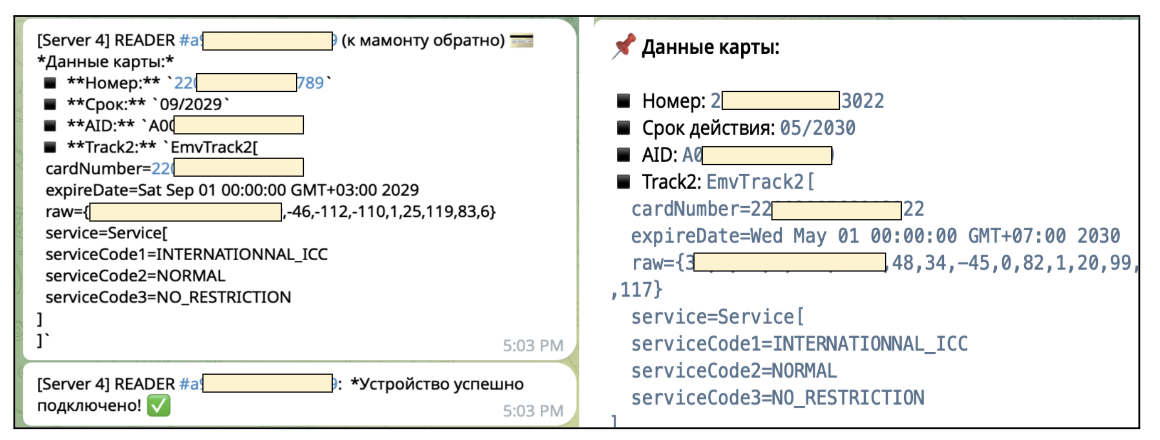

Behind this facade, background services silently capture card numbers, expiration dates, and critical EMV data fields transmitted during payment attempts.
From Data Theft to Automated Fraud Operations
Operational methods vary across different threat actor groups. Some campaigns deploy paired applications where one tool extracts card data while another interfaces with point-of-sale systems to complete fraudulent purchases.
Other variants focus exclusively on data exfiltration, automatically transmitting stolen credentials to private Telegram channels where cybercriminals receive structured messages containing device identifiers, complete card details, and transaction metadata.
The malware maintains persistent communication with command-and-control infrastructure through an extensive protocol of commands including device registration, APDU relay for terminal communication, PIN harvesting, and status monitoring.
Commands like “apdu_command” and “apdu_response” enable real-time relay attacks where the malicious app forwards payment terminal requests to remote servers controlled by attackers, effectively allowing criminals to conduct transactions using victims’ payment credentials from anywhere in the world.
Cybercriminal forums have adopted the Russian slang term “Mamont”—meaning mammoth—to refer to victims of these schemes, underscoring the organized nature of these operations and their roots in Eastern European cybercrime networks.
Growing Threat Demands Heightened Vigilance
The rapid proliferation of NFC-based payment malware reflects cybercriminals adaptation to the increasing adoption of contactless payment technologies.

As “Tap-to-Pay” transactions become ubiquitous globally, the attack surface for NFC exploitation continues to expand.
The scale of this threat—evidenced by hundreds of malicious applications, extensive server infrastructure, and coordinated Telegram-based command channels—demonstrates that this is no longer experimental activity but rather an established and profitable criminal enterprise.
Financial institutions must enhance fraud detection systems to identify anomalous NFC transaction patterns, while mobile device manufacturers should implement stricter controls around NFC permissions.
Users should exercise extreme caution before granting any application access to NFC payment functionality, particularly when installing apps from unofficial sources or unfamiliar developers requesting payment-related privileges.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
