A sophisticated threat actor known as Curly COMrades has demonstrated advanced evasion capabilities by leveraging legitimate Windows virtualization features to establish covert, long-term access to victim networks.
Operating to support Russian geopolitical interests, the group has deployed innovative tools and techniques that successfully bypass traditional endpoint detection and response (EDR) solutions.
This investigation, conducted in collaboration with the Georgian CERT under the Operative-Technical Agency of Georgia, reveals a multi-layered attack framework centered on Hyper-V abuse and custom malware implants.
The most notable discovery in this campaign involves the exploitation of Hyper-V, Windows’ native virtualization platform, to create an isolated attack infrastructure directly on compromised machines.
Rather than deploying malware directly on the host operating system, Curly COMrades enabled the Hyper-V role on selected Windows 10 systems and deployed a minimalistic Alpine Linux-based virtual machine containing their custom malware.
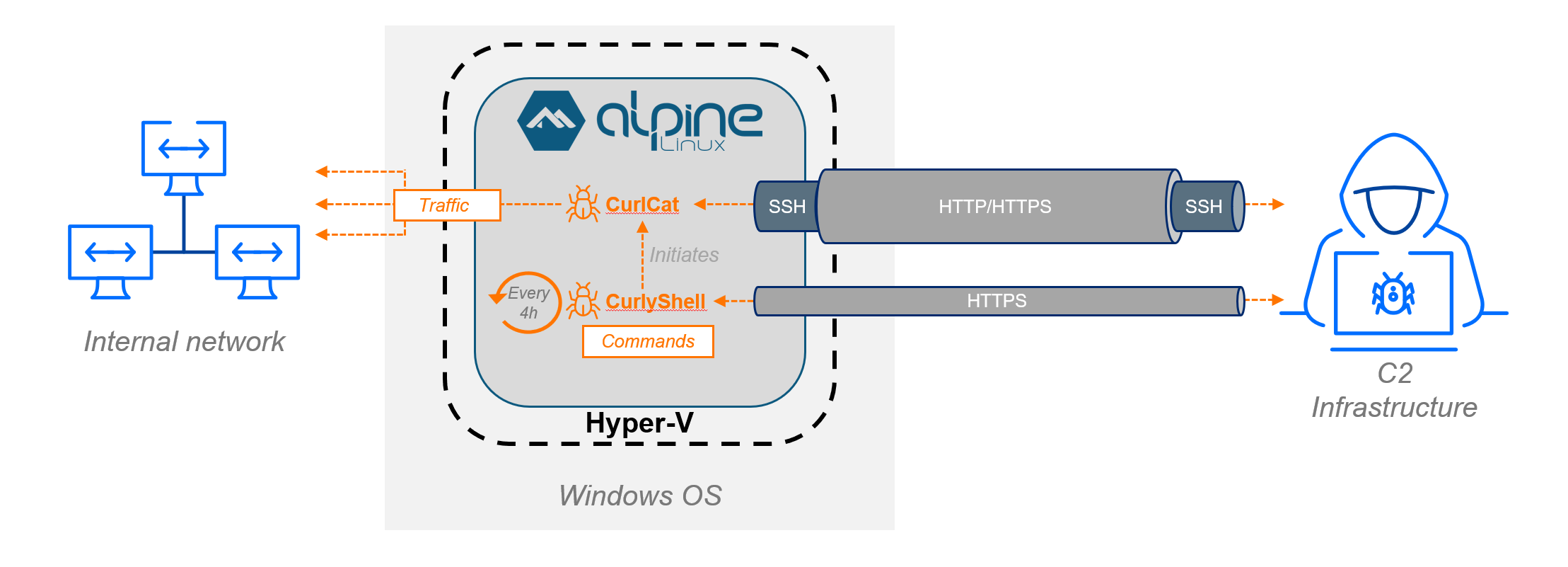
This environment occupied merely 120MB of disk space and consumed only 256MB of memory, creating a lightweight footprint that significantly reduces detection risk.
The attackers configured the virtual machine to use Hyper-V’s Default Switch network adapter, which routes all traffic through the host’s network stack using Network Address Translation (NAT).
This clever configuration made all malicious outbound communication appear to originate from the legitimate host machine’s IP address, effectively masking the true source of attacks.
The VM itself was customized with attacker-controlled domain-to-IP mappings and private DNS server configurations, enabling direct communication with command and control infrastructure while remaining isolated from traditional host-based monitoring.
Custom Malware Arsenal
Within the virtualized environment, Curly COMrades deployed two closely related custom malware families: CurlyShell and CurlCat.
Both implants share an identical underlying code base written in C++ and built around the libcurl library, yet serve distinctly different operational purposes.
The program’s custom session management begins with the construction of the SesCustom object.

CurlyShell functions as a persistent reverse shell, establishing and maintaining primary connections to command and control infrastructure using HTTPS.
The malware employs a non-standard Base64 encoding alphabet to evade security tools expecting standard encoding patterns.
For persistence, it leverages a simple but effective cron job executed at 20-minute intervals every four hours, ensuring continuous access even after system reboots.
CurlCat operates as a reverse proxy tunnel manager, designed specifically to wrap outgoing SSH traffic into standard HTTP request payloads.
This technique allows attackers to blend malicious communications with legitimate network traffic, bypassing network-based detection systems.
The malware integrates directly into SSH client configurations, using a ProxyCommand mechanism to covertly tunnel all subsequent connections through a SOCKS proxy on the attacker’s infrastructure.
PowerShell-Based Lateral Movement
Beyond the virtualized environment, investigators discovered sophisticated PowerShell scripts enabling lateral movement across compromised networks.
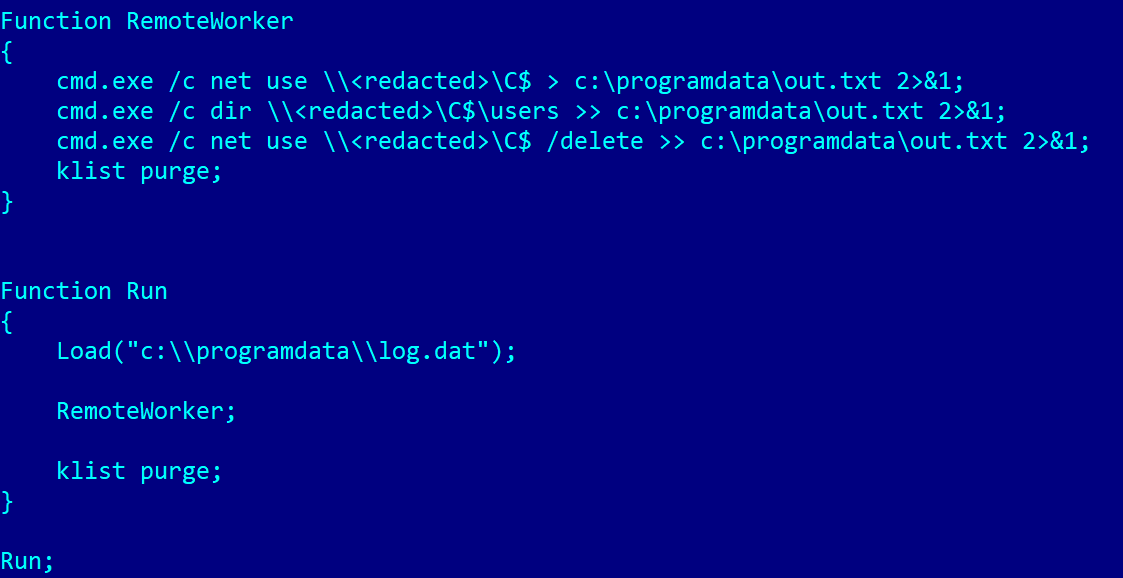
One script, found at c:programdatakb_upd.ps1, performs Kerberos ticket injection into the LSASS process, allowing attackers to authenticate to remote systems without requiring passwords. The script encrypts embedded payloads using a hardcoded key, demonstrating careful operational security considerations.
The RemoteWorker() function is designed as a template for executing post-exploitation tasks, using the newly injected Kerberos tickets to authenticate against remote systems via SMB.

A second PowerShell variant discovered through Group Policy deployment creates persistent local accounts on domain-joined machines.
Found at c:Windowsps1screensaver.ps1 and later variants, these scripts repeatedly reset account passwords to maintain persistent access across remediation attempts.
Critical analysis of the attackers’ command and control infrastructure became possible through swift collaboration between security researchers and Georgian CERT officials.
When Georgian authorities seized a compromised website used as a relay point, forensic analysis revealed iptables rules redirecting victim traffic to attacker infrastructure at 88.198.91[.]116, alongside custom sshd services and application-level proxy configurations designed to minimize forensic traces.
The investigation demonstrates how modern threat actors increasingly abuse legitimate system features to evade detection, requiring organizations to implement defense-in-depth security strategies beyond traditional EDR solutions.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
