JPCERT/CC has issued an urgent warning about ongoing attacks by the advanced persistent threat group APT-C-60, which continues to target recruitment professionals in Japan through sophisticated spear-phishing campaigns.
The attack campaign specifically impersonates job seekers contacting recruitment staff, exploiting the natural workflow of human resources professionals who regularly review candidate submissions.
Between June and August 2025, security researchers observed a significant evolution in the threat actors’ tactics, with attackers now directly attaching weaponized VHDX files to emails instead of hosting them on Google Drive as previously documented.
Unlike earlier attacks from August 2024 where victims were directed to download VHDX files from Google Drive links, the latest variant delivers the malicious virtual hard disk file directly as an email attachment, reducing the attack chain and increasing the likelihood of successful compromise.
When recipients mount the VHDX file and click the embedded LNK shortcut, the malware exploitation begins through an ingenious abuse of legitimate Git software.
The malicious LNK file executes gcmd.exe, a genuine Git component, which then processes the glog.txt script stored within the VHDX container.

This technique allows the attackers to bypass traditional security controls by leveraging trusted system processes.
The initial script performs three critical functions: displaying a decoy resume document to maintain the illusion of legitimacy, creating multiple persistent files on the victim’s system, and executing the first-stage payload called Downloader1.
The malware establishes persistence through COM hijacking by manipulating the Windows registry, specifically targeting the CLSID {566296fe-e0e8-475f-ba9c-a31ad31620b1} to ensure execution across system reboots.
Downloader1 communicates with legitimate statistics service StatCounter to identify compromised devices using a combination of the volume serial number and computer name.
The attackers monitor these communications and upload corresponding configuration files to GitHub repositories under their control.
This dual use of legitimate services makes network-based detection extremely challenging, as both StatCounter and GitHub are commonly whitelisted in enterprise environments.
Enhanced Malware Capabilities
The APT-C-60 group has significantly updated their SpyGlace malware framework, with JPCERT/CC observing three distinct versions: 3.1.12, 3.1.13, and 3.1.14.
The latest iterations demonstrate sophisticated anti-analysis capabilities and expanded functionality compared to version 3.1.6 documented in 2024.
Notably, the attackers modified the malware to disable previously implemented process termination commands while adding a new “uld” command capable of loading modules, executing specific functions, and cleanly unloading them after two seconds.
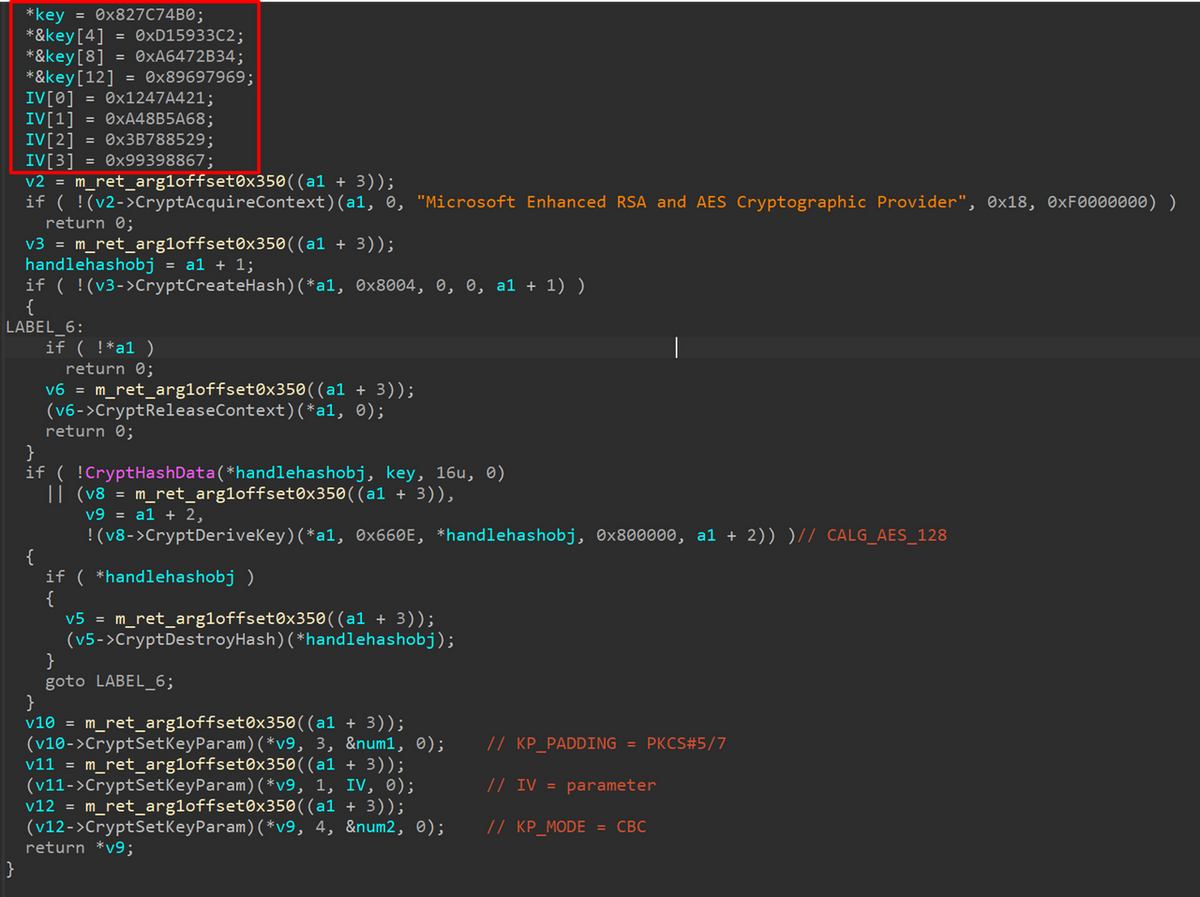
The malware employs custom cryptographic implementations including a modified RC4 algorithm with increased Key Scheduling Algorithm cycles and additional XOR operations.
SpyGlace’s encoding scheme combines single-byte XOR with SUB instructions for string obfuscation and dynamic API resolution, making static analysis significantly more difficult.
Communication with command-and-control infrastructure uses BASE64 encoding layered over the custom RC4 variant, with all payloads encrypted using AES-128-CBC encryption.

Analysis of the malware’s communication headers reveals the consistent userid value “GOLDBAR” in initial check-in requests, which security researchers believe indicates campaigns specifically targeting Japanese organizations.
This identifier matches patterns reported by Positive Technologies and JPCERT/CC observations from 2024, suggesting operational continuity and regional focus by the threat actors.
Infrastructure Analysis and Attribution
The attackers’ infrastructure transition from Bitbucket to GitHub for payload distribution provides unique visibility into their operations.
Because GitHub retains historical commit data unless repositories are deleted, researchers successfully reconstructed the timeline of malware deployments. Version 3.1.12 was uploaded on June 27, 2025, followed by version 3.1.13 on July 3, and version 3.1.14 on July 16, demonstrating rapid iteration cycles and active development.
Examination of GitHub commit logs revealed email addresses associated with the attacker-controlled repositories, along with volume serial numbers and computer names of successfully compromised devices.
Organizations are strongly advised to implement enhanced scrutiny of VHDX file attachments, monitor unusual GitHub and StatCounter traffic patterns, and deploy behavioral detection capabilities focused on COM hijacking techniques.
The decoy documents used in the campaign contained fabricated academic resumes listing multiple research papers, though investigation revealed the purported authors did not include the sender’s name, indicating the attackers created persona-based email accounts specifically for this operation.
JPCERT/CC emphasizes that APT-C-60 continues primarily targeting Japan and East Asian regions with consistent methodologies despite tactical evolution.
The threat group’s persistent abuse of legitimate services including StatCounter, GitHub, and Git software demonstrates their sophisticated understanding of enterprise security architectures and detection blind spots.
The threat remains active and continues evolving, requiring sustained vigilance from security teams across the region.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
