Proofpoint Threat Research has identified a previously unknown Iranian threat actor, dubbed UNK_SmudgedSerpent, that conducted sophisticated phishing campaigns against academics and foreign policy experts between June and August 2025.
The group employed credential harvesting techniques, sophisticated social engineering, and remote management tools to infiltrate targets, revealing a complex web of overlapping tactics reminiscent of established Iranian threat groups.
The campaign began in June 2025 when Proofpoint researchers discovered benign emails discussing economic uncertainty and political unrest in Iran sent to over 20 members of a United States-based think tank.
The threat actor impersonated Suzanne Maloney, vice president and director of the Foreign Policy program at the Brookings Institution, using a Gmail address with a deliberately misspelled name, “Suzzane Maloney.”
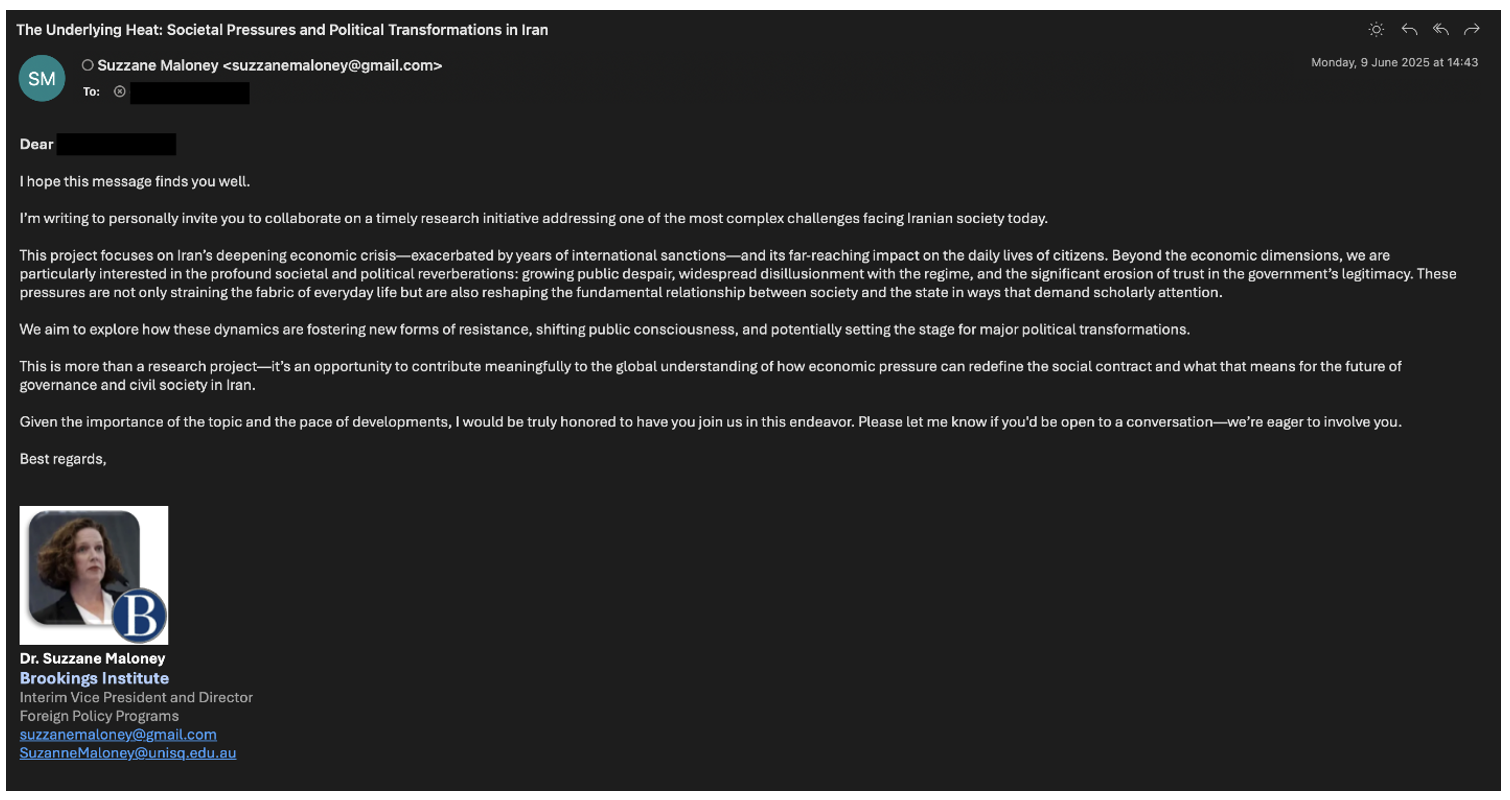
The attackers leveraged domestic political lures centered on societal change in Iran and an investigation into the militarization of the Islamic Revolutionary Guard Corps (IRGC).
Sophisticated Social Engineering
The infection chain demonstrated advanced operational tradecraft. After establishing initial contact with benign conversation starters about Iran policy collaboration, the attacker requested credential verification and scheduled meetings using Israeli time zones despite targeting U.S.-based analysts.
The actor then delivered URLs masquerading as OnlyOffice links but actually redirecting to health-themed attacker domains including thebesthomehealth.com and mosaichealthsolutions.com.
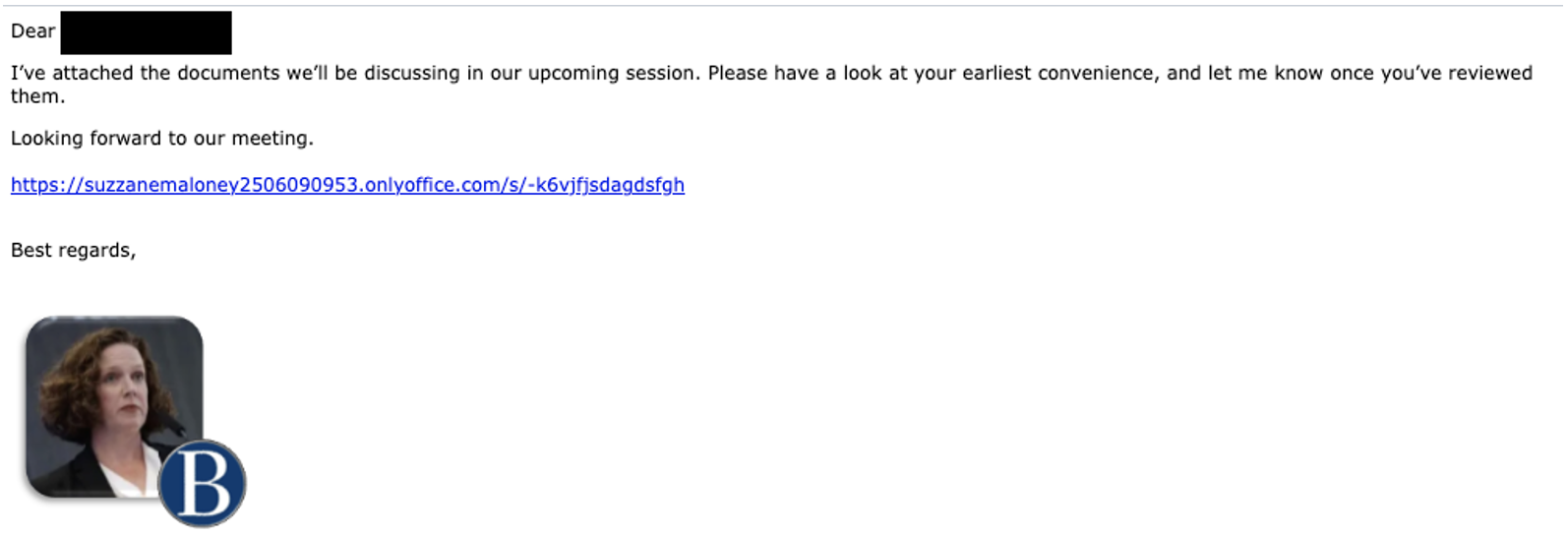

These domains hosted customized credential harvesting pages with pre-loaded user information, increasing the likelihood of successful compromise.
When targets grew suspicious of the credential harvesting pages, UNK_SmudgedSerpent quickly adapted by removing password requirements and transitioning to spoofed OnlyOffice login pages.
The attacker then hosted malicious archives containing Microsoft Installer (MSI) files that loaded PDQConnect, a legitimate Remote Monitoring and Monitoring (RMM) tool.
Subsequent hands-on-keyboard activity involved deploying ISL Online, a second RMM platform, suggesting either redundancy or contingency planning after initial compromise attempts failed.
The investigation revealed overlapping tactics with three established Iranian threat groups: TA453 (Charming Kitten), TA455 (C5 Agent), and TA450 (MuddyWater). These overlaps prevented definitive attribution but suggested potential operational connections.
The URL was only masquerading as an OnlyOffice link in the email but instead hyperlinked to a health-themed attacker domain thebesthomehealth[.]com, which redirected to a second health-themed attacker domain mosaichealthsolutions[.]com that displayed a Microsoft 365 login page.

UNK_SmudgedSerpent’s approach of targeting policy experts and using benign conversation starters matched TA453’s methodology, while the use of health-themed domains and OnlyOffice infrastructure resembled TA455 operations.
The deployment of RMM tools, however, aligned with TA450’s documented tactics—making RMM usage particularly significant since it remains rare among state-sponsored actors.
Continued Targeting of Iran Experts
Beyond the initial Brookings Institution campaign, UNK_SmudgedSerpent demonstrated persistent interest in Iran policy expertise.
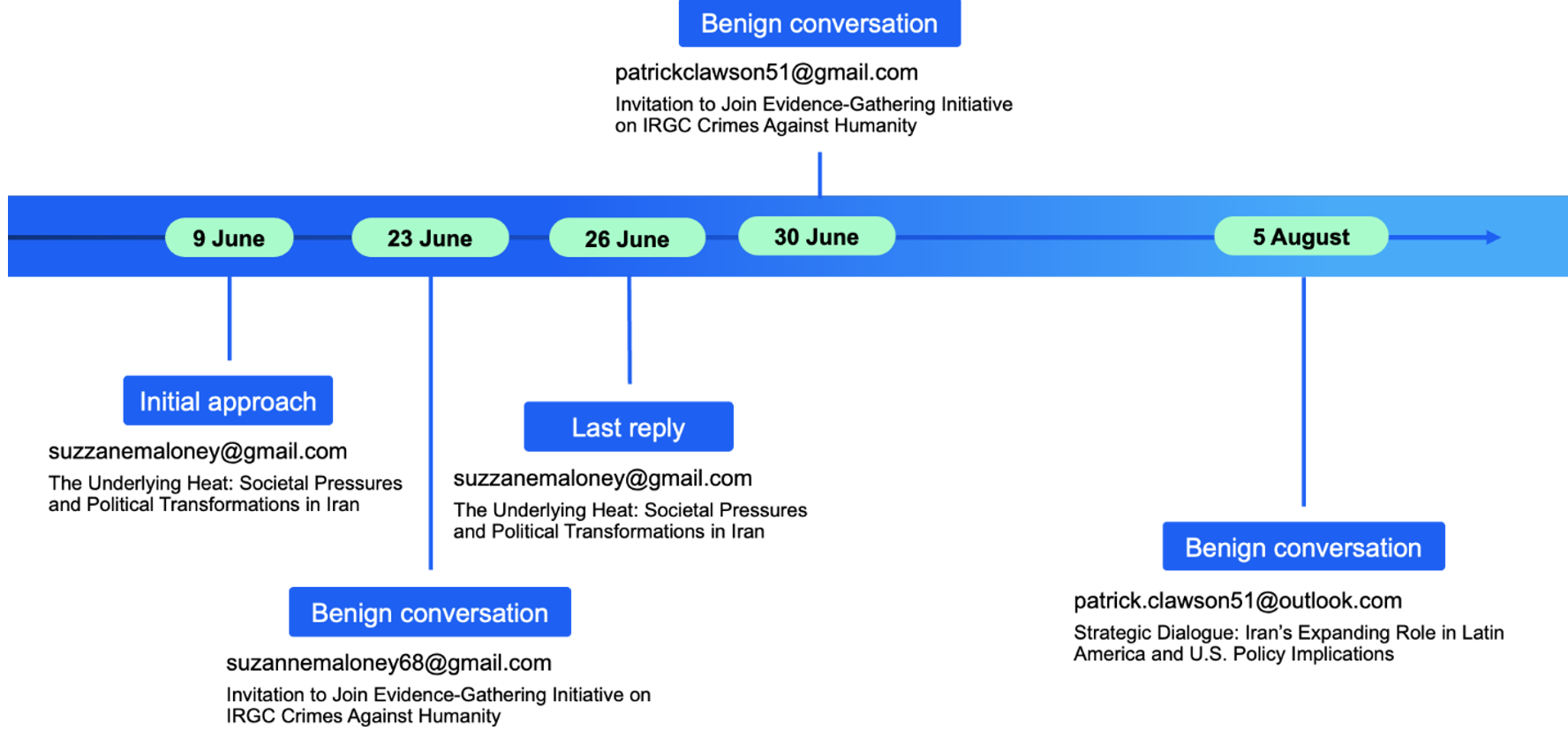

The group spoofed additional personas, including Dr. Suzanne Maloney (spelled correctly) and Patrick Clawson, director at the Washington Institute, targeting U.S.-based academics with Israeli connections.
In August 2025, the actor pivoted to soliciting collaboration on Iran’s Latin American operations, again using spoofed Patrick Clawson accounts across Gmail and Outlook.
The campaign’s sporadic but deliberate targeting pattern suggests institutional interest in understanding foreign perspectives on Iranian government activities, military operations, and regional influence.
Since August 2025, no further UNK_SmudgedSerpent activity has been detected, though researchers believe related operations likely continue.
Proofpoint’s findings highlight the evolving sophistication of Iranian cyber operations and the persistent targeting of policy experts who analyze Iranian government intentions and capabilities.
The complexity of attribution in this ecosystem reflects the Iranian government’s broader intelligence collection priorities and the potential reorganization or contractor exchanges among threat groups operating under state sponsorship.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
