ClickFix attacks have surged dramatically over the past year, cementing their position as pivotal tools in the modern attacker’s arsenal.
These sophisticated social engineering campaigns coerce users into executing malicious code on their own devices, bypassing traditional awareness defenses that focus on preventing suspicious clicks, dodgy downloads, and phishing websites.
During a recent threat briefing in London and the latest webinar hosted by Push Security, researchers highlighted how ClickFix techniques have rapidly evolved not just in their web page design, but in how they are delivered and how payloads are executed.
A standout example included a highly sophisticated Cloudflare themed lure with a compelling interface.
This page featured an embedded instructional video, a ticking countdown, and a live counter of “users verified in the last hour,” all enhancing the lure’s credibility and pressing unsuspecting victims into following the process.
How Advanced ClickFix Pages Operate
One of the most alarming trends observed is the weaponization of instructional videos that show users step-by-step how to bypass supposed security checks.

The most advanced pages tailor content such as commands and instructions according to the visitor’s device, with Mac-specific directions becoming increasingly common.
Under the hood, dangerous automation is at play. A majority of these pages use JavaScript to automatically copy malicious commands to the user’s clipboard, setting the stage for what researchers describe as a “self-infection” process.
Victims are tricked into pasting and running this code, often under the guise of passing a security check.
Unlike classic phishing, these attacks rarely rely on email as the initial delivery vector. In fact, research found that four out of five ClickFix lures intercepted began with poisoned Google search results or malicious (malvertising) ads.
Attackers optimize fraudulent sites or leverage vulnerabilities in popular CMS platforms to distribute their payloads, thus evading email security gateways.
As ClickFix attack moves beyond email-based entry, traditional anti-phishing tools are sidestepped, exposing a monitoring gap. Even when email is used, evasion tactics such as domain camouflage, rapid domain rotation, bot protection, and heavy content obfuscation make detection by web crawlers and proxies increasingly challenging.


Critically, security solutions inside the browser sandbox often cannot flag clipboard-altering scripts as malicious, giving attackers a stealthy strike zone until malware execution occurs on the endpoint.
Device-level controls that block clipboard access offer little protection, as ClickFix lures require an explicit user action (like clicking a button) to trigger the malicious script. This interaction cannot be generically blocked at the OS level.
Payload Innovation and Beyond
The payloads themselves evolve, too. Attackers are no longer relying solely on PowerShell and mshta: they are leveraging a wide spectrum of living-off-the-land binaries (LOLBINs).
Sophisticated variants now employ cache smuggling, which tricks browsers into downloading disguised payloads such as a malicious file masked as a JPG executed locally with zero network signal for security tools to detect.
The future threat landscape may see complete compromise performed within the browser, bypassing EDR and endpoint security altogether.
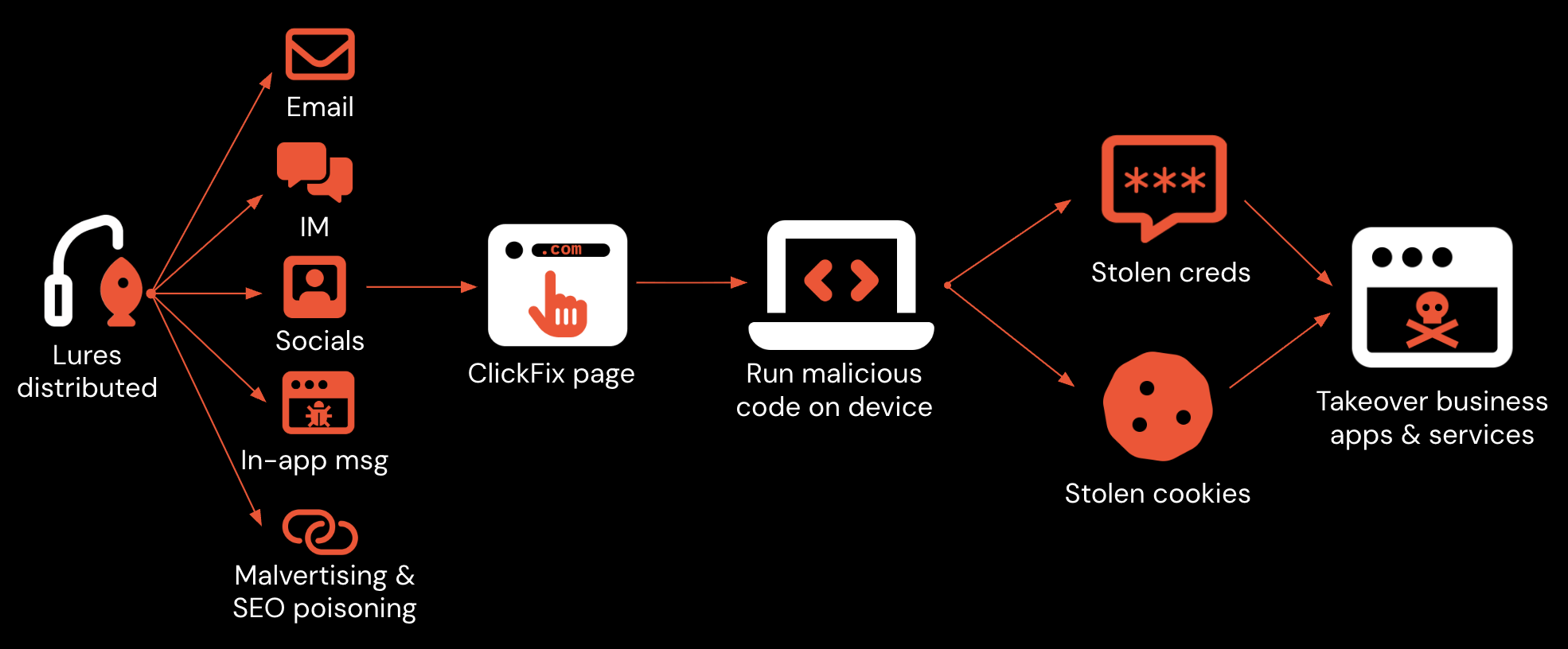

Already, the hybrid model delivering browser lures to trigger endpoint compromise for credential and cookie theft has proven alarmingly effective.
According to Microsoft’s 2025 Digital Defense Report, ClickFix was the leading initial access technique in 2025, constituting 47% of all observed attacks.
This reliance on EDR as the last and often only line of defense is dangerous, especially in organizations permitting unmanaged BYOD devices.
Because ClickFix is user-initiated, context may be lacking for automated tools to classify alerts, risking missed or misprioritized detections correctly.
Push Security’s new malicious copy-paste detection offers a proactive browser-side defense, blocking ClickFix at its inception regardless of delivery method or payload type.
Supplementing endpoint security with browser-based controls is now vital to intercepting these advanced social engineering attacks before they breach organizational defenses.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
