LockBit has remained one of the most dominant ransomware-as-a-service (RaaS) groups in the world since its emergence as ABCD ransomware in 2019 and official launch as LockBit in 2020.
Despite high-profile setbacks including international law enforcement takedowns in early 2024 and a damaging affiliate panel leak in May 2025 the group continues to update its codebase, expand affiliate operations, and launch large-scale attacks targeting organizations across industries.
Flashpoint has tracked LockBit through numerous evolutions, from the early .abcd encryptors to the faster and stealthier LockBit 3.0 and the Conti-inspired LockBit Green.
Now, with version 5.0, the group has introduced a refined two-stage ransomware deployment model that aims to maximize evasion, modularity, and destructive impact.
This analysis outlines how LockBit 5.0 works, what’s changed, and why defenders should treat this latest evolution as a clear signal that even after takedowns and leaks, ransomware groups are innovating faster, not backing off.
Trend Micro first flagged the emergence of LockBit 5.0 in late September 2025. Flashpoint’s analysis confirms that the group is building on the existing v4.0 codebase rather than starting from scratch.
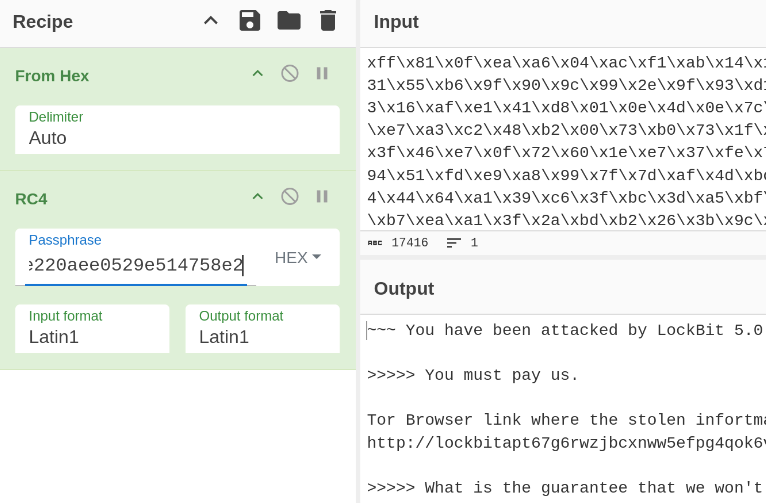
Many core functions remain, including familiar file encryption methods, geographic execution limits, and even a recycled ransom note that still misspells “information”.
However, LockBit 5.0 introduces several new or upgraded capabilities. A modular two-stage architecture separates the loader from the primary payload, and expanded anti-analysis features include control-flow obfuscation and API hashing.
The malware employs aggressive EDR bypass using process hollowing, unhooked libraries, and ETW patching. It also supports stealth execution modes that omit file extensions and ransom notes.
These updates demonstrate that LockBit’s developers are focused on staying operational under pressure, iterating on technical defenses while retaining the group’s familiar tooling and affiliate model.
The Two-Stage Execution Model
At the heart of LockBit 5.0 is its new two-stage execution model. Stage one acts as a loader built for stealth and survivability, while stage two executes the core ransomware payload, designed for flexible deployment, targeted destruction, and layered evasion.
Stage One: The Stealthy Loader and EDR Evasion
Key features of the loader at stage one include control flow obfuscation, where the code calculates jump destinations dynamically, making traditional disassembly and reverse engineering more difficult.
Dynamic API resolution means the malware avoids hardcoded API names and instead resolves function calls at runtime using a custom hashing algorithm.
Library unhooking is employed to reload clean copies of NTDLL and Kernel32 from disk, overwriting any hooks placed by security tools in memory.
The loader constructs custom shellcode trampolines that redirect execution to resolved API calls, bypassing standard detection methods.
The loader then creates a suspended instance of defrag.exe and injects the decrypted payload using process hollowing.
Flashpoint analysts confirmed that the stage two payload is written into memory using ZwWriteProcessMemory, the instruction pointer is updated, and the process resumes execution all without triggering default security alerts.
Stage Two: The Destructive Ransomware Payload
Stage two is the main ransomware payload. Flashpoint observed this binary labeled “ChuongDoung Locker v1.01,” a likely nod to researcher Chuong Dong. It contains both familiar LockBit features and new destructive options.
The payload supports various command-line switches and can run with or without a visible impact. In “destruction-only” mode, it encrypts files silently without changing extensions or displaying a ransom note, a tactic that may be used for retaliatory or purely disruptive campaigns.
Additional behaviors include encryption of local drives, specific directories, and network shares, as well as multi-threaded encryption using Curve25519 keys and XChaCha20 cipher.
Repeated library unhooking occurs for every DLL loaded, while system services such as VSS, WSearch, and Edgeupdate are disabled.
File and directory exclusions preserve OS functionality and evade detection. The ransom note text is decrypted using RC4 and written as ReadMeForDecrypt.txt.
Before executing, the payload checks the victim machine to ensure it is not in Russia or Russia-allied locations, and curiously, avoids execution on systems located in the Philippines a behavior Flashpoint continues to investigate.
Implications for Defenders
LockBit 5.0 reflects a broader shift in ransomware development: professionalization under pressure. Despite sanctions, leaks, and arrests, the group continues to operate at scale.
Security teams should monitor illicit forums and breach sites for early warning signals, correlate vulnerability intelligence with ransomware group preferences to prioritize patching, use behavioral detection to flag evasive actions like ETW patching or library unhooking, and prepare tailored response playbooks with negotiation protocols, offline backups, and legal guidance pre-staged before an attack occurs.
The release follows the May 2025 leak of internal LockBit data, which exposed affiliate accounts, ransomware builds, and ransom negotiations between victims and affiliates.
For defenders, this reinforces the importance of tracking ransomware groups not only by indicators of compromise but also by their tooling, tactics, techniques, and procedures.
LockBit 5.0 is the latest proof that ransomware isn’t going away it’s adapting. The best way to stay ahead is by fusing primary source intelligence, behavioral analysis, and coordinated readiness.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
