The construction industry has emerged as a primary target for sophisticated cyber adversaries in 2025, with threat actors including state-sponsored APT groups, ransomware operators, and organized cybercriminal networks actively targeting organizations across the building and construction sector.
Nation-state actors from China, Russia, Iran, and North Korea are leveraging the industry’s rapid digital transformation and security gaps to establish persistent network access and exfiltrate valuable data.
The escalating threat landscape stems from the construction sector’s increasing dependence on vulnerable IoT-enabled machinery, Building Information Modeling (BIM) systems, and cloud-based project management platforms.
These technologies, while enhancing operational efficiency, have created new attack surfaces that threat actors exploit with precision.
Ransomware campaigns designed to disrupt critical project timelines, supply chain attacks targeting third-party software and equipment vendors, and social engineering schemes directed at on-site personnel represent substantial operational and financial risks for construction enterprises.
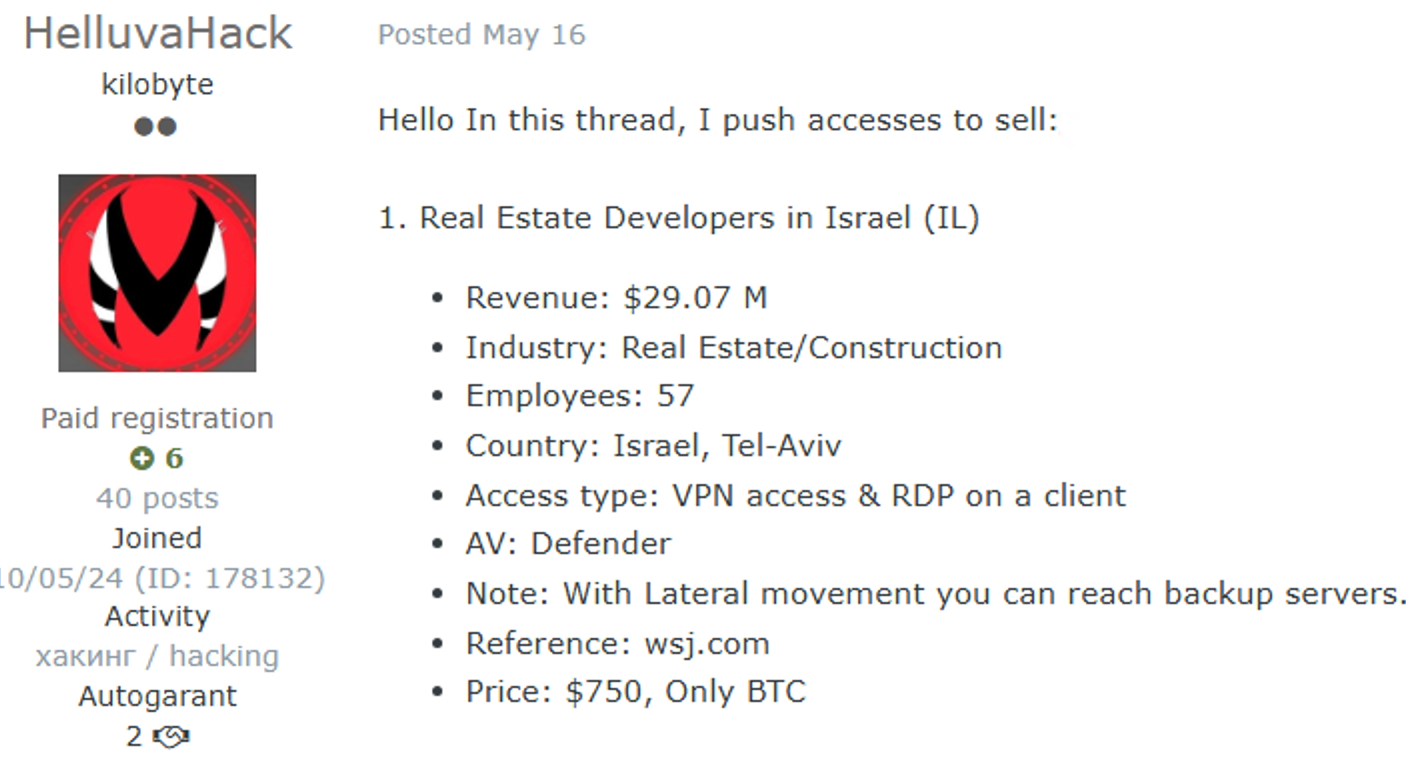
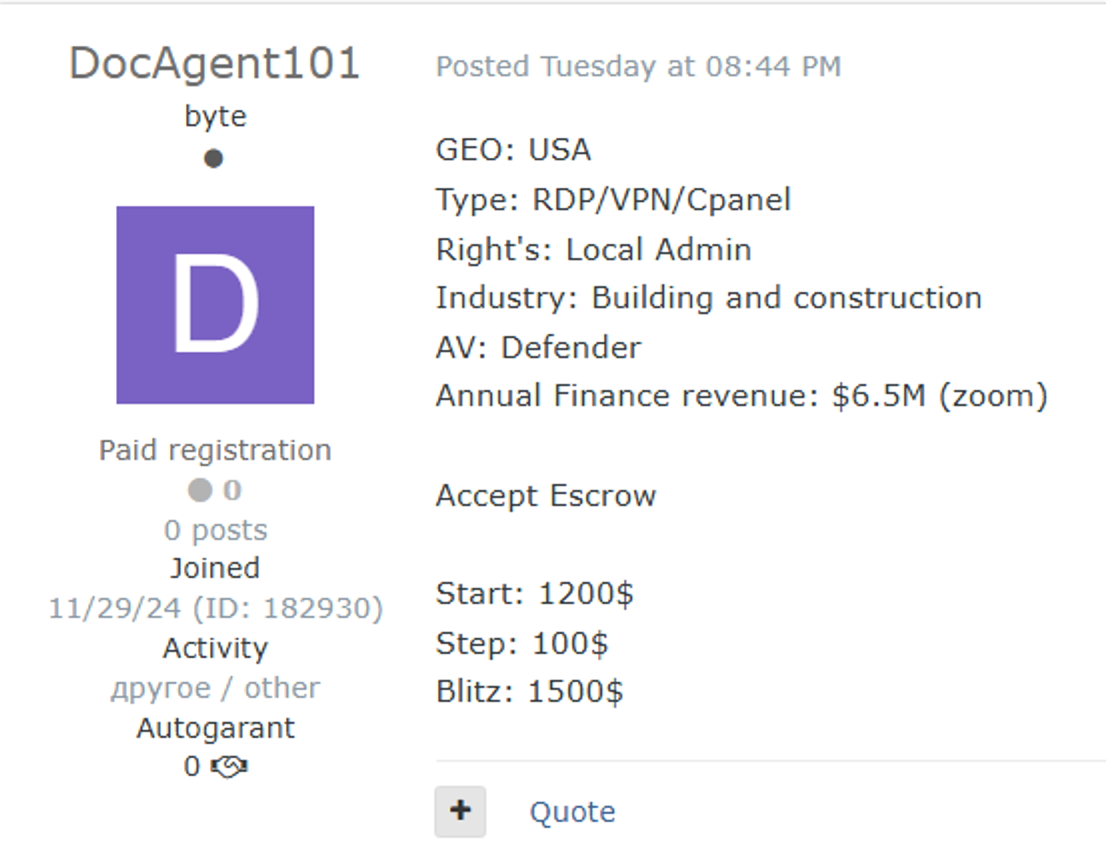
Cybercriminals have identified initial network access as a critical entry point for infiltrating the construction industry. These digital brokers facilitate the sale of network access types including VPN, RDP, SSH, Citrix, SMTP, and FTP credentials sourced from previously breached networks.
Rather than conducting resource-intensive reconnaissance, threat actors increasingly purchase pre-compromised credentials from underground forums and dark web marketplaces.
⠀
Pricing correlates directly with the target organization’s size and network complexity, making enterprise construction firms particularly attractive commodities.
This credential-based attack methodology bypasses traditional perimeter defenses, allowing attackers to establish legitimate-appearing network sessions and move laterally throughout interconnected systems.
Once inside, threat actors systematically exfiltrate high-value data including architectural blueprints, project contracts, financial records, and personally identifiable information belonging to employees and subcontractors.
Social Engineering Exploitation
The construction sector’s operational characteristics create ideal conditions for social engineering attacks.

A dispersed workforce operating across multiple job sites, tight project deadlines, and complex vendor networks provide attackers with numerous manipulation vectors.
Threat actors impersonate project managers, suppliers, and executives through phishing emails, SMS messages, and voice communications requesting immediate payment, credential disclosure, or sensitive document access.
Vendor impersonation tactics prove particularly effective, with attackers requesting payment detail modifications or delivering fraudulent invoices that exploit the industry’s reliance on extensive subcontractor networks.
Executive impersonation campaigns leverage urgency to pressure employees into fund transfers or confidential information disclosure before verification procedures can be implemented.
Construction projects typically involve dozens or hundreds of distinct partners, each introducing their own security posture and potential vulnerabilities.
Unlike centralized industries, construction companies rarely maintain complete visibility over or control of third-party cybersecurity standards.
This fragmented environment creates significant blind spots where compromised software updates or equipment suppliers can rapidly propagate breaches across entire projects.
The industry’s prioritization of speed and cost-efficiency over comprehensive security vetting compounds these risks.
Mitigations
Construction organizations must elevate cybersecurity from operational afterthought to business-critical priority.
This includes securing legacy systems, protecting IoT devices through network segmentation and firmware updates, implementing mandatory employee security awareness training, and deploying robust encryption for sensitive data at rest and in transit.
As the industry continues its digital evolution, proactive threat mitigation is imperative for ensuring project continuity and organizational resilience.
Effective mitigation requires establishing precise contractual cybersecurity requirements, conducting ongoing third-party risk assessments, and implementing real-time monitoring systems that identify vulnerabilities before operational impact.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
