A sophisticated supply chain attack has compromised critical industrial control systems through nine malicious NuGet packages designed to inject time-delayed destructive payloads into database operations and manufacturing environments.
Socket’s Threat Research Team identified these weapons of code, published under the alias shanhai666 between 2023 and 2024, which have collectively accumulated 9,488 downloads before being reported to NuGet on November 5, 2025.
The campaign demonstrates unprecedented attack sophistication, combining 99% legitimate functionality as cover code with hidden malicious payloads that trigger process termination with 20% probability on each database query after specific dates in 2027 and 2028.
The most dangerous package, Sharp7Extend, targets Siemens industrial programmable logic controllers (PLCs) through typosquatting, implementing dual sabotage mechanisms that wreak immediate chaos upon installation.
Sharp7Extend represents a particularly devastating threat to manufacturing environments. By appending “Extend” to the trusted Sharp7 library name, the threat actor exploited developers searching for PLC communication enhancements.
The package bundles the complete, unmodified legitimate Sharp7 library (version 1.1.79), making detection during code review virtually impossible.
However, Sharp7Extend implements inverted trigger logic compared to database-focused packages: instead of delayed activation, it terminates processes with 20% probability on every PLC operation immediately upon installation until June 6, 2028, then activates a second sabotage mechanism that silently corrupts write operations 80% of the time.
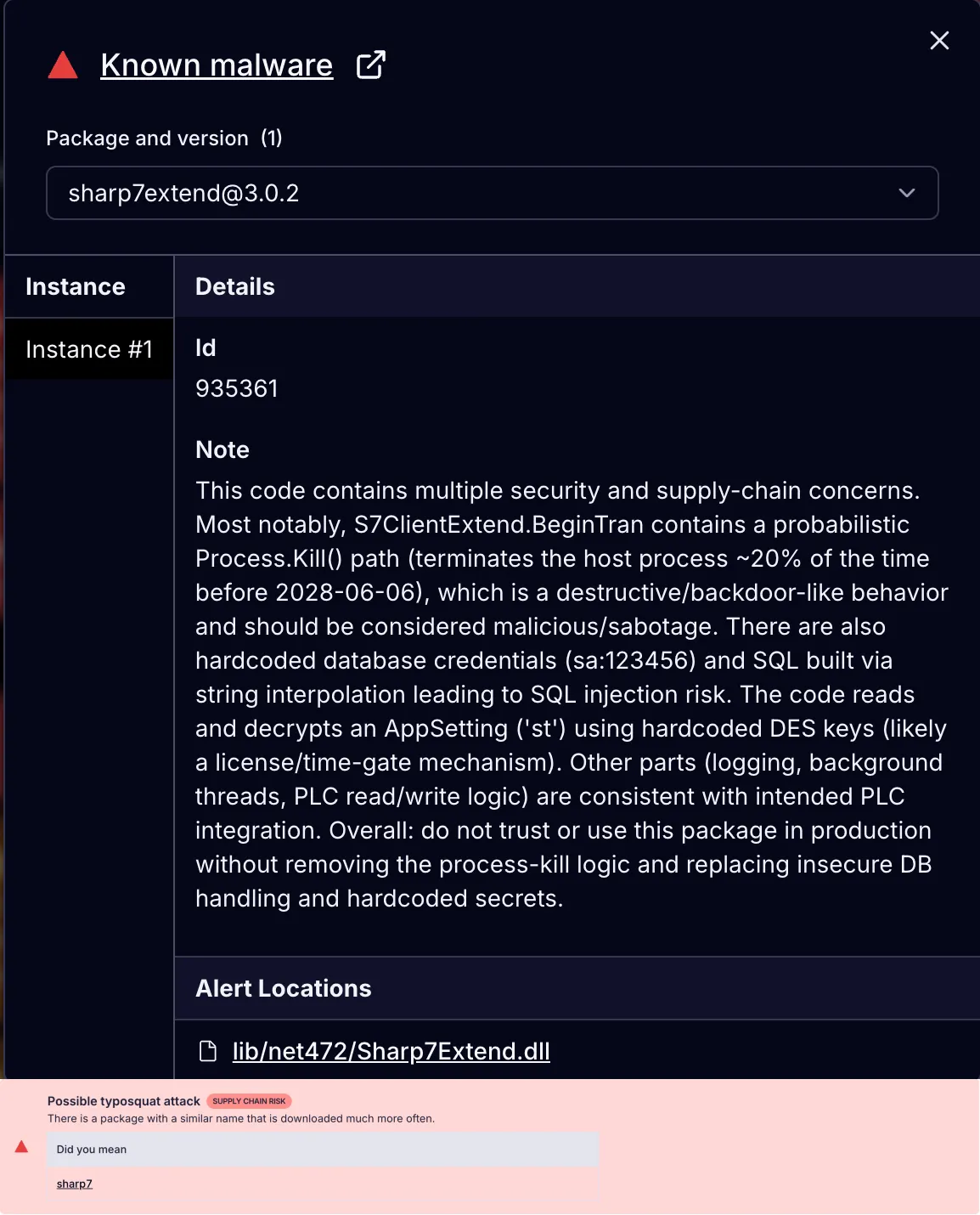
Sharp7Extend package.This dual-mechanism attack creates progressively worse failures. During the first 30-90 minutes, only process termination is active, causing random crashes attributable to network issues.
Affected sectors and geographic spread
After the grace period elapses, both mechanisms operate simultaneously, triggering cascading system failures and data corruption that mimic intermittent hardware failures rather than systematic attacks.
For manufacturing environments executing ten PLC operations per minute, production crashes become inevitable within 30 seconds, while 80% write operation failures compromise safety-critical systems.
The attack’s genius lies in its mathematical inevitability masked by probabilistic execution. Applications executing hundreds of database queries per hour will crash within seconds to minutes.
An e-commerce platform processing 100 queries per minute crashes mid-checkout in approximately three seconds. Healthcare systems operating at 50 queries per minute experience complete outages within six seconds.
Financial platforms trading at 500 queries per minute face total platform failure in under one second.
All nine malicious packages provide fully functional legitimate code implementing database repository patterns, LINQ support, pagination, async operations, and entity mapping.
This extensive legitimate functionality serves multiple purposes: building developer trust, passing code reviews where reviewers encounter familiar patterns, encouraging adoption through actual value delivery, and burying approximately 20 lines of malicious payload within thousands of lines of legitimate code.
Extension method injection weaponizes C# language features, transparently injecting malicious logic into every database and PLC operation.
The malware adds.Exec() extension methods to database command types and .BeginTran() methods to S7Client objects, enabling automatic execution with each operation.
The threat actor demonstrated operational security sophistication by maintaining metadata inconsistencies across packages displaying different author names despite publishing under the same shanhai666 alias designed to evade detection systems flagging packages from identical authors.
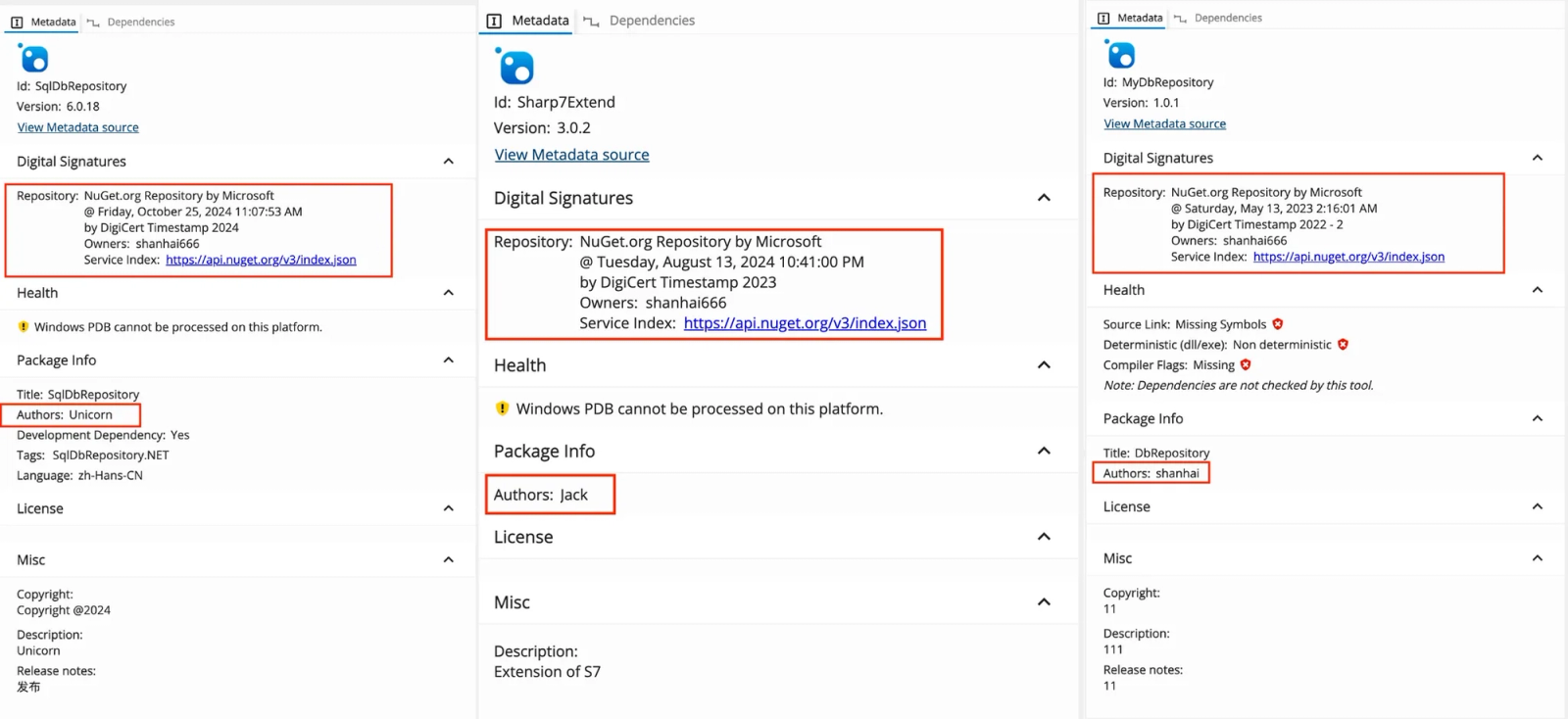

Signature file analysis revealed malformed structures, embedded strings, and multiple indicators suggesting Chinese origin, including Chinese-language error messages and internet slang throughout the code.
As of publication, the malicious packages remain live on the NuGet registry despite Socket’s November 5 report. NuGet confirmed investigation and removal efforts, but the time-delayed activation mechanisms have already compromised countless production systems.
Organizations must immediately audit dependencies for all nine packages and assume complete compromise of affected systems.
Industrial control systems running Sharp7Extend may already experience intermittent failures misattributed to PLC communication issues while silent write failures corrupt critical manufacturing operations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
