Cybersecurity researchers have identified a growing trend in Windows-targeted attacks that exploit fundamental operating system features to force machines into surrendering valuable credentials without requiring user interaction or system vulnerabilities.
Known as authentication coercion, this attack method manipulates legitimate Remote Procedure Call (RPC) protocols to trick computers into authenticating to attacker-controlled systems, potentially compromising entire network domains.
Authentication coercion attacks exploit the auto-authentication behavior built into Windows. When a machine attempts to connect to a network resource like a shared directory or printer, it automatically initiates authentication.
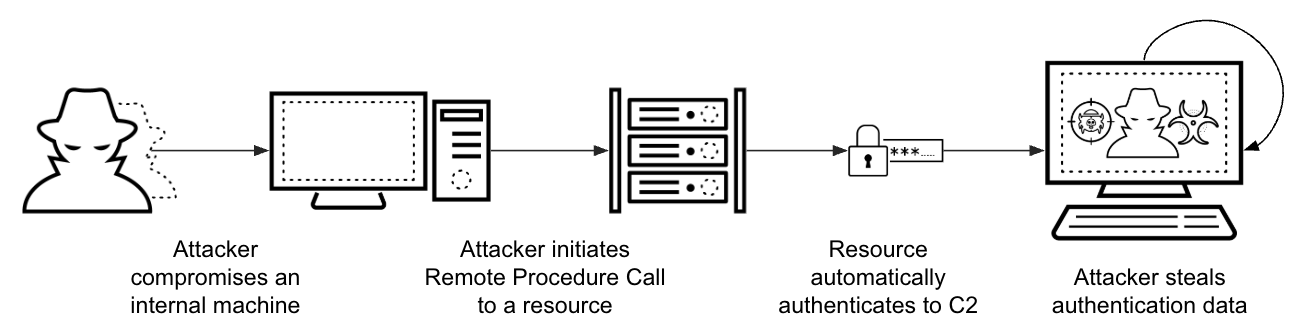
Attackers exploit this fundamental feature by setting up malicious listeners that impersonate legitimate resources. When a targeted machine connects, it inadvertently transmits its hashed credentials to the attacker’s server, providing the initial foothold for further compromise.
While authentication coercion techniques such as PrintNightmare became widely recognized in recent years, security researchers are now observing a significant shift in attacker tactics.
Rather than relying on well-known exploits that have become targets for defensive measures, threat actors increasingly exploit rarely monitored RPC interfaces and functions.
The legitimate usage of MS-EVEN when connecting to a remote server in the “Event Viewer” console.
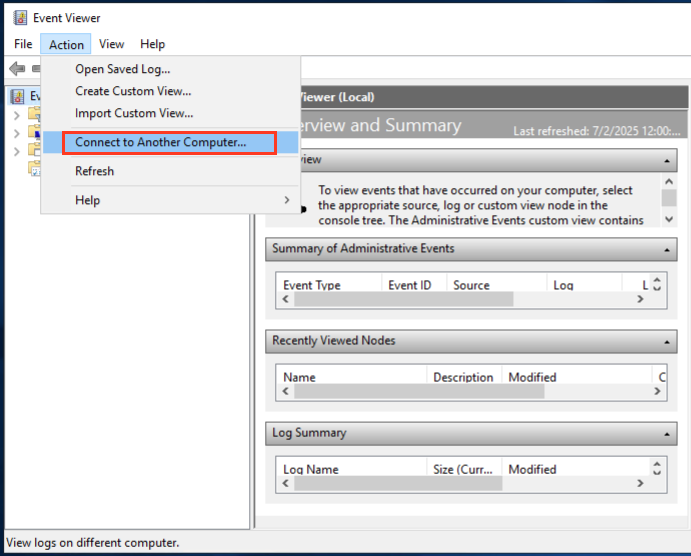

This evolution allows malicious actors to circumvent security tools specifically designed to detect traditional coercion attacks.
The Expanding Attack Surface
The scope of potential exploitation is considerably broader than initially recognized. A publicly available repository of Windows coerced authentication methods documents 16 working functions across five protocols that attackers can leverage, with researchers noting that over 240 additional functions remain untested and potentially exploitable.
This means attackers have numerous pathways to conduct these attacks, allowing them to rotate between techniques as defenses evolve.
Recent telemetry reveals that organizations across multiple sectors face increasingly sophisticated authentication coercion campaigns.
Threat actors have demonstrated particular interest in targeting critical assets such as Domain Controllers and Read-Only Domain Controllers, which, if compromised, can lead to complete domain compromise and lateral movement throughout enterprise networks.
In a March 2025 incident affecting a healthcare organization, attackers exploited the rarely used MS-EVEN (EventLog Remoting Protocol) interface to conduct authentication coercion. The threat actors employed the ElfrOpenBELW function a relatively obscure RPC method seldom monitored in typical network environments.
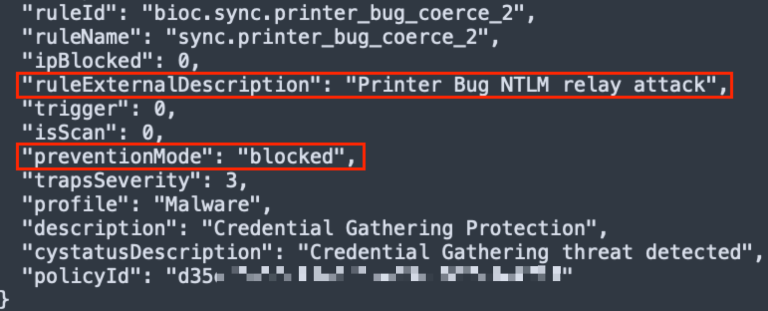

After successfully coercing authentication from multiple critical servers, including Domain Controllers and Citrix systems, the attackers harvested NTLM hashes and subsequently conducted an NTLM relay attack against certificate authority servers, potentially enabling domain-wide privilege escalation.
The attack’s success hinged on exploiting the rarity of this RPC interface within the target environment. By using lesser-known functions, threat actors effectively evaded traditional detection mechanisms focused on popular coercion techniques like PrintNightmare and PetitPotam.
Mitigating the Threat
Organizations must move beyond reactive defenses targeting specific known exploits. Effective protection requires implementing generic RPC monitoring that identifies behavioral anomalies, including unusual UNC path parameters, suspicious source-destination combinations, and calls targeting critical infrastructure.
Security teams should monitor for both well-known vulnerable interfaces and rare RPC functions that deviate from established baselines.

Technical mitigations include turning off unused RPC services, enforcing SMB signing across domains, enabling Extended Protection for Authentication, and implementing RPC filters using Windows built-in utilities.
Additionally, disabling unnecessary services like Print Spooler on Domain Controllers significantly reduces the attack surface.
As defenders strengthen defenses against known vectors, attackers will inevitably discover and weaponize new RPC functions.
Success requires organizations to adopt proactive, context-aware monitoring strategies that identify anomalies in RPC traffic patterns, establish behavioral baselines, and continuously assess emerging attack methodologies.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
