A newly discovered malware campaign is leveraging one of cybercriminals’ most effective lures cryptocurrency to distribute DarkComet RAT.
This notorious remote access trojan continues to plague users despite being discontinued by its creator years ago. Security researchers have identified a suspicious executable masquerading as a Bitcoin wallet application, which, when executed, silently deploys the full arsenal of DarkComet’s spying and control capabilities.
The cryptocurrency boom has created a fertile hunting ground for attackers. Bitcoin wallets, mining software, and trading tools represent prime targets for malicious repurposing because they appeal to a large, engaged audience of users who are often willing to download tools from unverified sources.
This particular campaign capitalizes on that weakness by packaging a DarkComet RAT variant inside a RAR archive labeled “94k BTC wallet.exe,” complete with deceptive cryptocurrency-related branding.
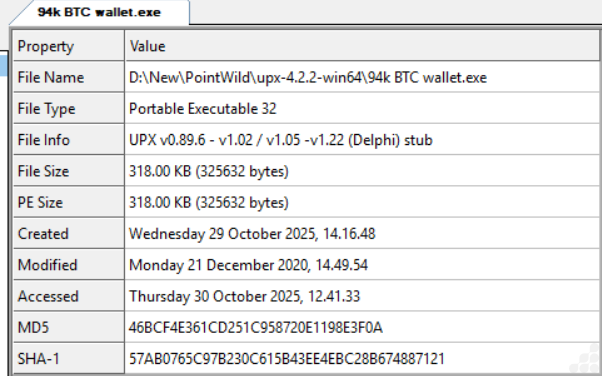
The attack chain begins with the compressed RAR file (MD5: dbedd5e7481b84fc5fa82d21aa20106f), which contains the malicious executable.
This layered delivery approach serves multiple purposes: it bypasses email filters that block direct executable attachments, reduces antivirus detection rates, and encourages victims to manually extract the payload playing into attackers’ social engineering tactics.
UPX Packing and Obfuscation
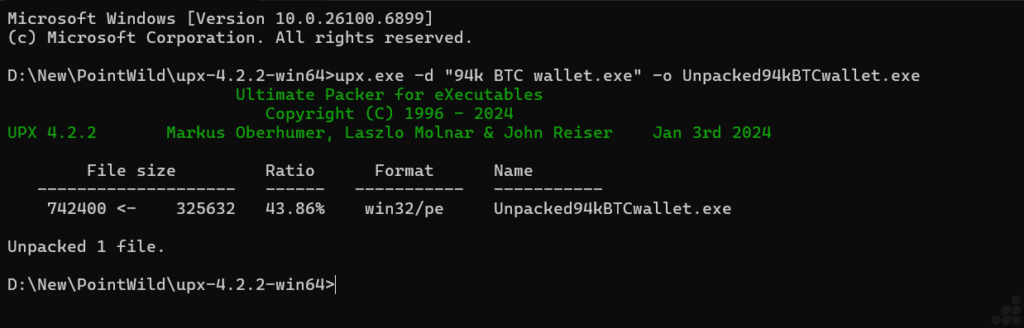
Upon decompression, the executable reveals itself as UPX-packed malware a compression technique that obscures the binary’s proper structure and capabilities.
The packed sample (318 KB) decompresses to 725 KB of unobfuscated code, representing a 43.86% compression ratio.
By applying UPX packing, malware authors achieve three critical objectives: they evade static signature-based detection, obscure API imports and code logic from reverse engineering tools, and reduce the payload size for efficient distribution.

Analysis using CFF Explorer revealed the telltale signs of UPX compression UPX0 and UPX1 sections replacing standard PE sections like .text and .data.
Cryptocurrency enthusiasts must exercise extreme caution when downloading wallet tools or trading utilities, relying exclusively on official sources and verifying cryptographic signatures before execution.
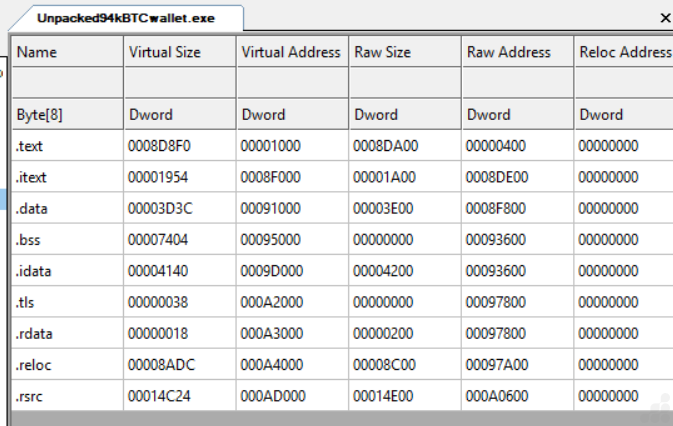

After successful unpacking using the UPX utility, the binary’s true nature emerged: a fully functional DarkComet RAT compiled with Borland Delphi (2006).
Capabilities and Malicious Behavior
Once executed, the malware establishes persistence by copying itself as “explorer.exe” to %AppData%RoamingMSDCSC and creating an autostart registry key at HKCUSoftwareMicrosoftWindowsCurrentVersionRun. This ensures the malware survives system reboots and maintains continuous access.
Configuration analysis revealed the hardcoded command-and-control infrastructure pointing to kvejo991.ddns.net on port 1604 the default C2 channel for DarkComet. The malware uses the mutex “DC_MUTEX-ARULYYD” to ensure only a single instance runs, preventing conflicts during execution.
The RAT’s feature set includes keystroke logging, where captured credentials and sensitive information are stored in a “dclogs” folder before exfiltration to the C2 server.
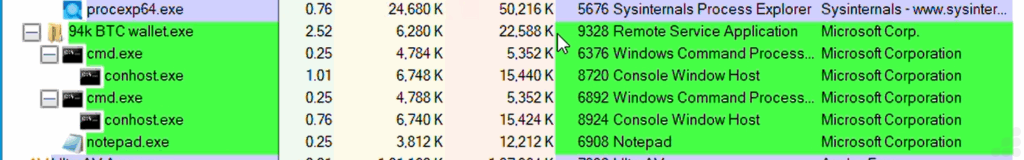

Process injection analysis showed the malware spawning decoy processes (cmd.exe, conhost.exe, and notepad.exe) to hide its malicious payload within legitimate Windows processes a common evasion tactic employed by DarkComet variants.
This discovery underscores a critical reality in cybersecurity: old malware never truly dies. Once publicly leaked, families like DarkComet are indefinitely repurposed by different threat actors.
Organizations should enforce application allowlisting policies and educate users on the dangers of downloading unverified software particularly tools claiming cryptocurrency functionality.
Indicators of Compromise (IOCs)
| Category | Indicator / Details |
|---|---|
| Archive File | 11bf1088d66bc3a63d16cc9334a05f214a25a47f39713400279e0823c97eb377 |
| Payload EXE | 5b5c276ea74e1086e4835221da50865f872fe20cfc5ea9aa6a909a0b0b9a0554 |
| Unpacked EXE | 58c284e7bbeacb5e1f91596660d33d0407d138ae0be545f59027f8787da75eda |
| Install Path | C:Users |
| Registry Key | HKCUSoftwareMicrosoftWindowsCurrentVersionRunexplorer → C:UsersadminAppDataRoamingMSDCSCexplorer.exe |
| Mutex | DC_MUTEX-ARULYYD |
| C2 Domain | kvejo991.ddns.net |
| C2 Port | 1604 (TCP) |
| Keystroke Capture Log file | 2025-10-29-4.dc |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
