Security researchers have uncovered a sophisticated malware campaign that leverages the ClickFix social engineering technique to distribute information-stealing malware across Windows and macOS platforms.
The campaign demonstrates how threat actors are exploiting legitimate search queries for cracked software to deliver devastating payloads that compromise user credentials and sensitive data.paste.txt
The infection chain begins when users search for cracked or pirated software online, a well-established lure for cybercriminals.
Instead of receiving legitimate results, victims encounter malicious landing pages hosted on Google-hosted services, including Colab, Drive, Looker Studio, Sites, and Groups.
This multi-hop infrastructure is deliberately designed to evade traditional security measures, as administrators are less likely to block Google services outright.paste.txt
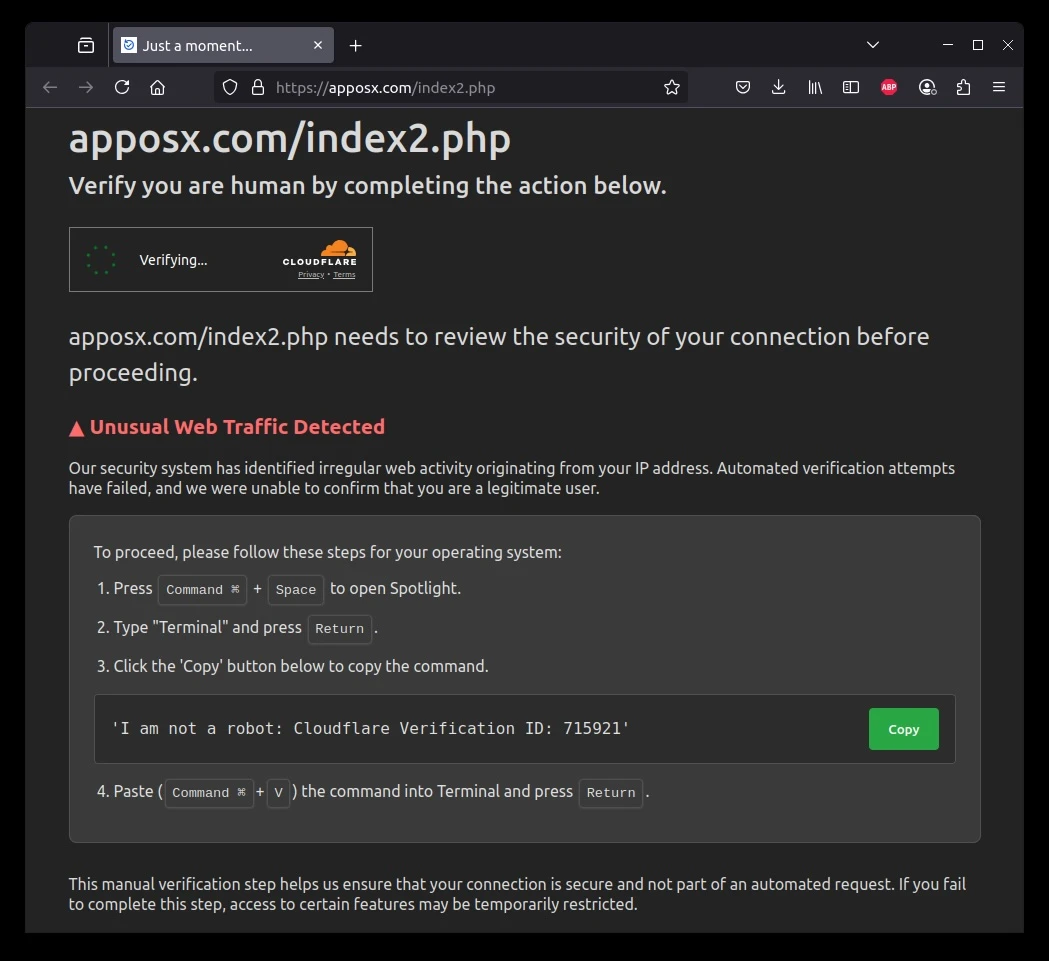
Once users click through these landing pages, they’re presented with fake security warnings that mimic legitimate Cloudflare verification pages.
The deceptive interface instructs users to copy and paste what appears to be a verification string into their terminal.
However, what victims actually execute is a malicious Base64-encoded shell command that fetches and runs infostealer malware directly in memory a fileless attack method that bypasses traditional antivirus protection.paste.txt
Overview of the ClickFix Attack Campaign
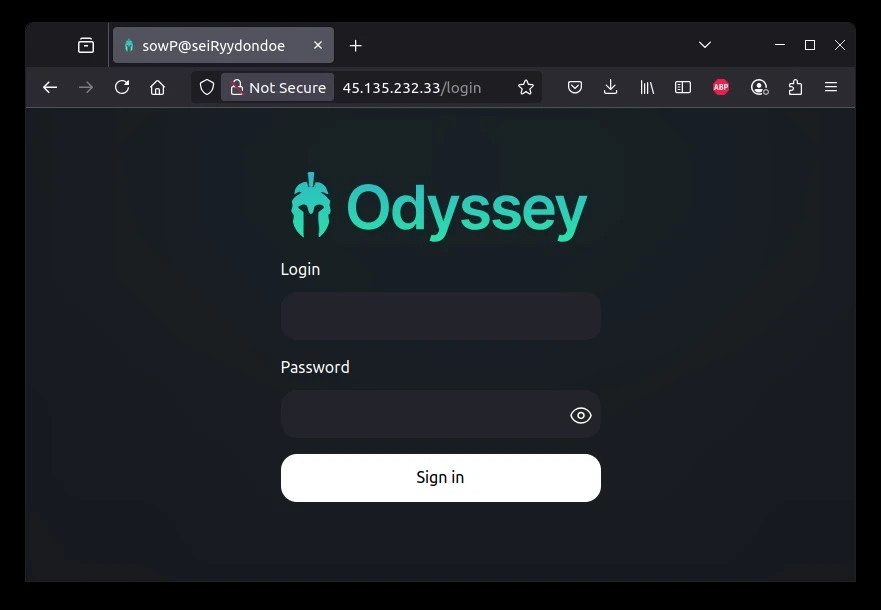
The campaign’s sophistication lies in its operating system-specific payload delivery. Windows users are directed toward ACR stealer, while macOS users receive Odyssey stealer, a macOS variant.
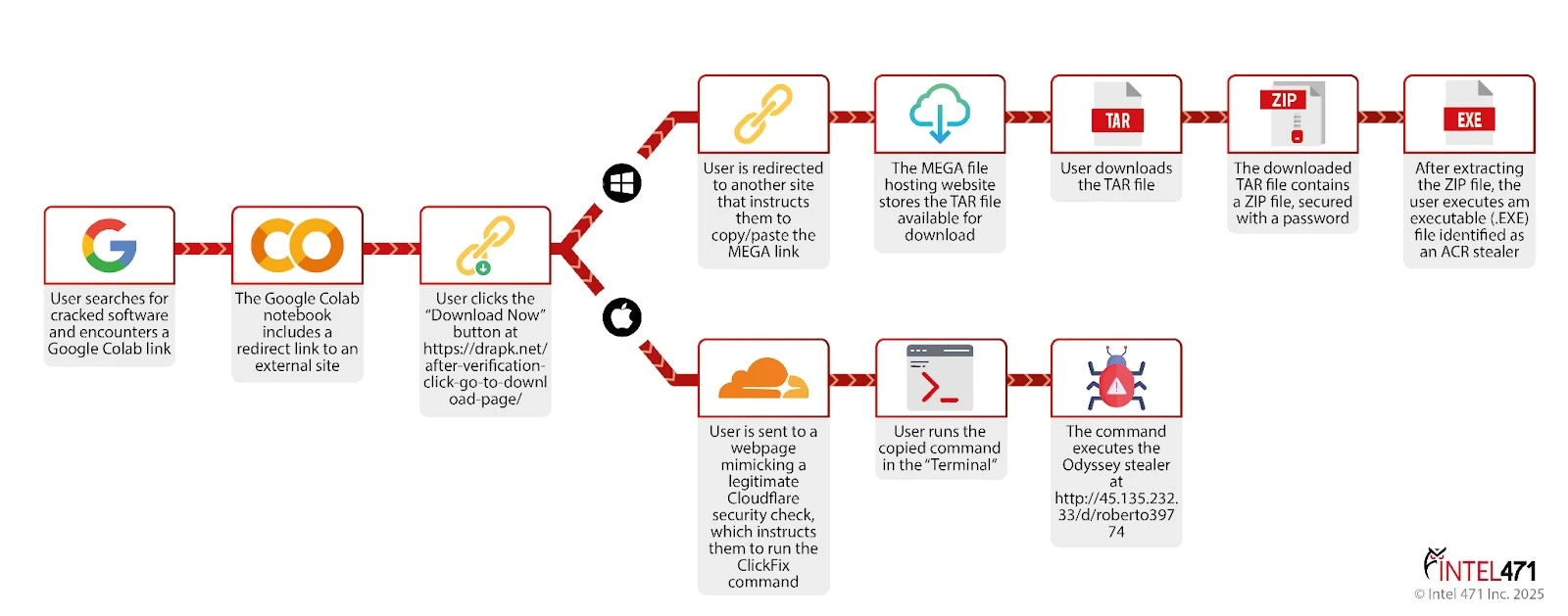
The initial payloads arrive as password-protected ZIP archives containing executable files that deploy the full infostealer functionality.
Security researchers discovered that ACR operates not only as an information stealer but also functions as a loader for additional malware, including SharkClipper, a cryptocurrency clipboard hijacker that replaces copied wallet addresses with attacker-controlled ones.paste.txt. Selecting this button redirects to a webpage where a “Download Now” button appears.

The effectiveness of this campaign is staggering. Researchers documented nearly 700 percent increase in ACR stealer logs uploaded to underground markets in May 2025 compared to the previous month, with 133,980 new compromised user logs captured in that month alone.
This dramatic surge underscores how successful the ClickFix attack vector has become, even among advanced threat actors.paste.txt
Future Threat Predictions
ClickFix’s success stems from several critical factors. Unlike traditional phishing campaigns delivered through email, these attacks arrive through organic search results and social media, completely bypassing email security solutions.
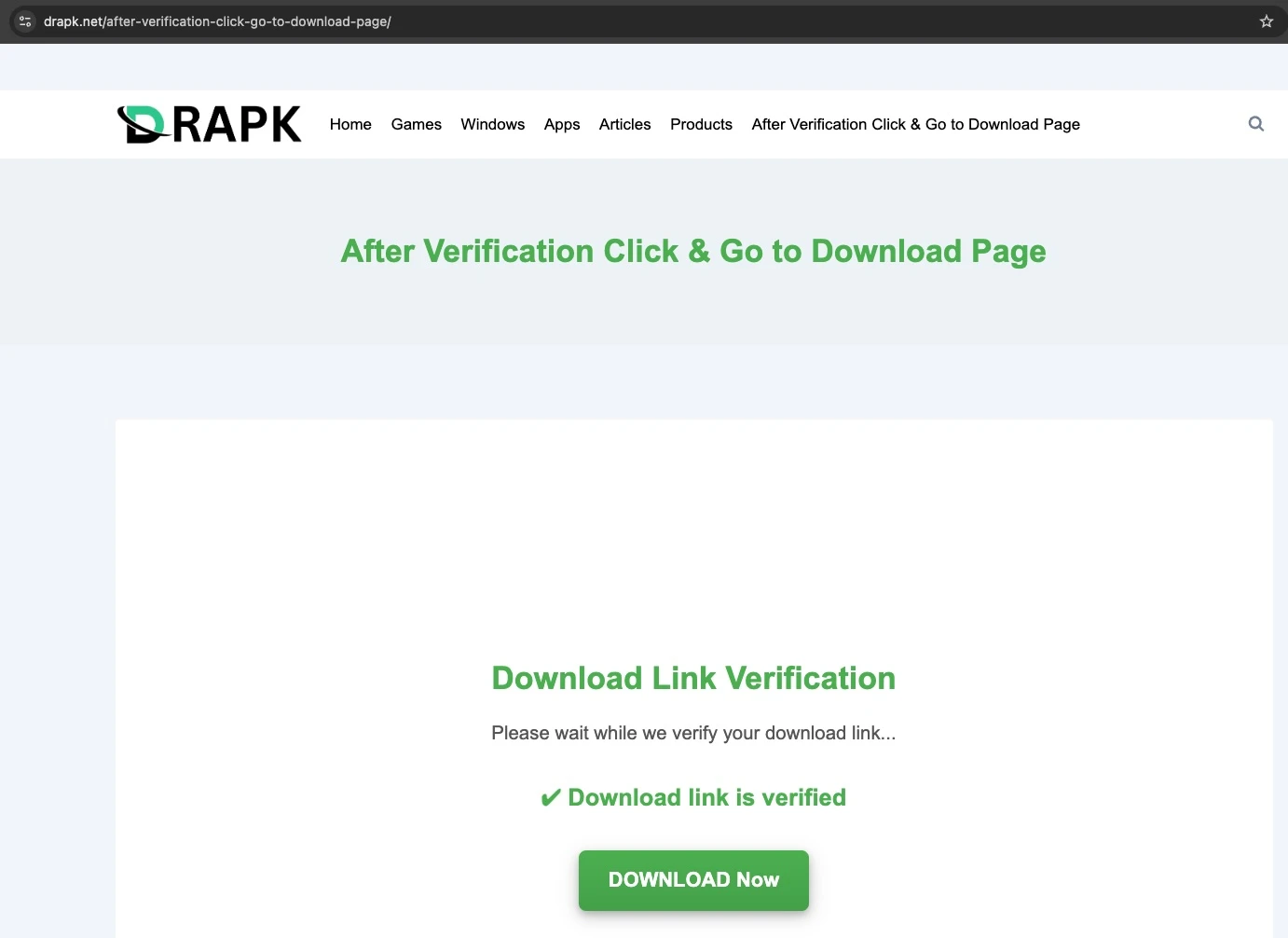
NordVPN crack link on macOS, the initial redirect from Google Colab still led to https://drapk.net/after-verification-click-go-to-download-page/, but clicking the “Download Now” button no longer triggered a second redirect.

The malicious scripts execute within browser sandboxes, making them invisible to most security monitoring tools. Additionally, the commands execute directly in memory, creating a clean, fileless process that evades traditional endpoint security measures.paste.txt
Odyssey collects user data, including passwords, cookies, cryptocurrency wallets, documents that match a particular extension, Apple Notes, Keychain entries and system metadata.

According to Microsoft’s 2025 Digital Defense Report, ClickFix has become the most common initial access method, accounting for 47 percent of all initial access schemes.
This alarming statistic reflects a broader shift in attack methodologies, as cybercriminals prioritize social engineering over technical exploits.paste.txt
The implications for Windows and macOS users are severe. Once compromised, affected systems become vectors for credential theft, financial data exfiltration, and further malware installation.
Security experts emphasize that users should never copy and execute unverified commands from unknown sources, regardless of how legitimate the prompting page appears.
Organizations must also strengthen endpoint detection and response (EDR) capabilities, as this remains the last line of defense against fileless ClickFix attacks that slip past traditional security tools.paste.txt
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
