Security researchers have uncovered a sophisticated supply chain attack disguised as a legitimate cryptocurrency wallet.
Socket’s Threat Research Team discovered a malicious Chrome extension called “Safery: Ethereum Wallet,” published on the Chrome Web Store on November 12, 2024, that employs an ingenious technique to steal user seed phrases through hidden blockchain transactions.
The extension, identified by its ID fibemlnkopkeenmmgcfohhcdbkhgbolo, markets itself as a secure and straightforward Ethereum wallet offering quick two-click transfers and easy balance management.
However, beneath this benign exterior lies a sophisticated backdoor that exfiltrates seed phrases by encoding them into Sui blockchain addresses and broadcasting microtransactions from a threat actor-controlled wallet.
When users create or import a wallet, the malicious extension encodes their BIP-39 mnemonic into one or two synthetic Sui-style addresses.
The extension then sends 0.000001 SUI to these encoded addresses using a hardcoded threat actor mnemonic. By decoding the transaction recipients, the attacker reconstructs the original seed phrase without requiring traditional command-and-control infrastructure.
This approach hides exfiltration within legitimate-looking blockchain transactions that are nearly impossible to detect through conventional monitoring.
The extension’s technical implementation is sophisticated. It loads the standard BIP-39 wordlist, maps each word to its numeric index, and packs these indices into a hexadecimal string prefixed with “0x” to resemble a valid Sui address.
The malware never displays Sui balances or prompts for Sui actions these functions exist solely to transform seed phrases into blockchain-compatible data appearing innocuous to external observers.
Deceptive Distribution
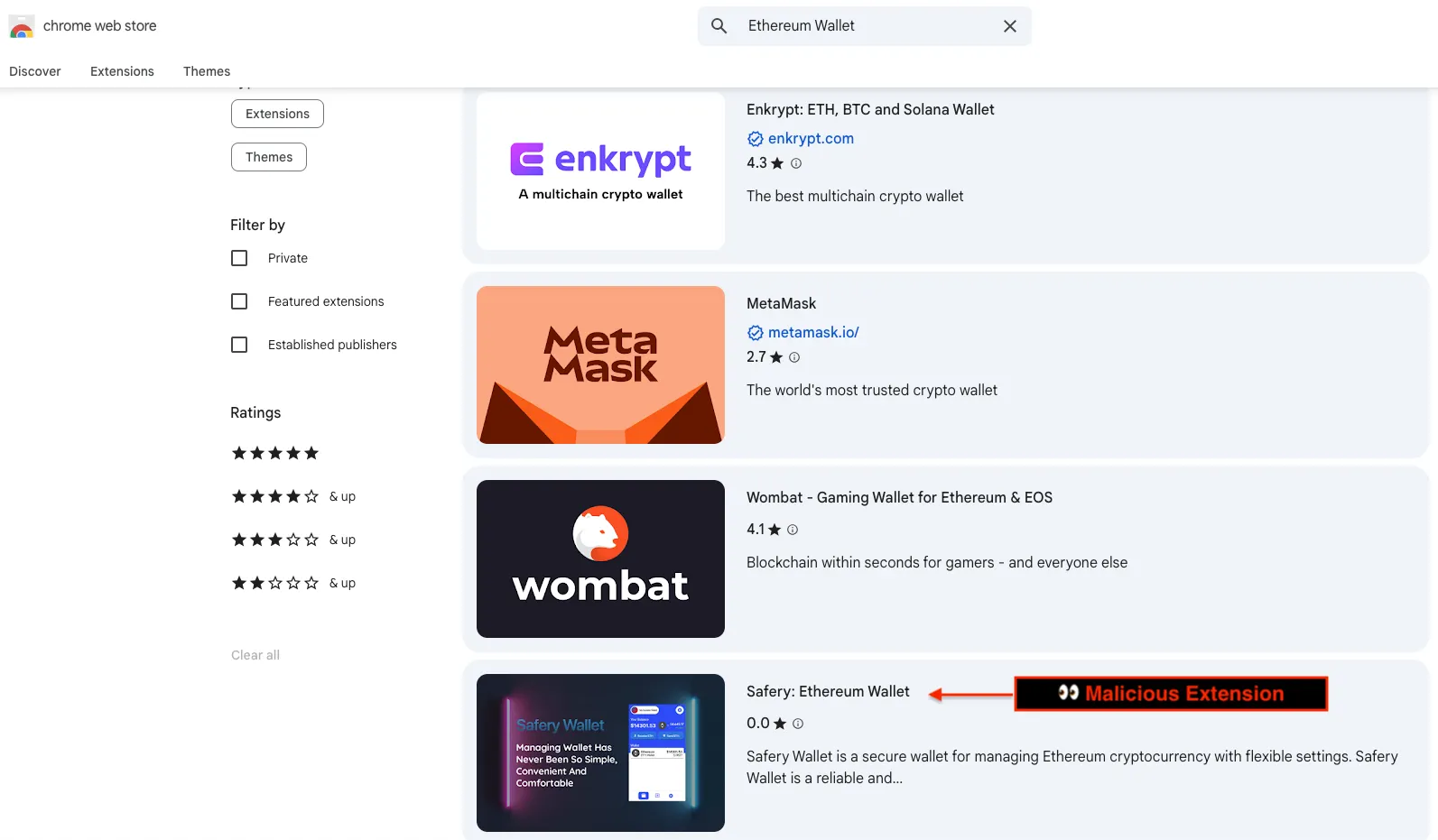
The extension’s deceptive appearance amplifies its threat. When searching “Ethereum Wallet” on the Chrome Web Store, Safery appears as the fourth result, positioned alongside legitimate wallets like MetaMask and Enkrypt.
SaferyThe developer’s privacy disclosure falsely claims no user data collection and that private keys remain on the device assurances that directly contradict the extension’s actual functionality.
The attack chain is seamless. When users enter a valid seed phrase during login or wallet creation, the extension encodes it into synthetic Sui addresses and broadcasts microtransactions from the hardcoded threat actor wallet.
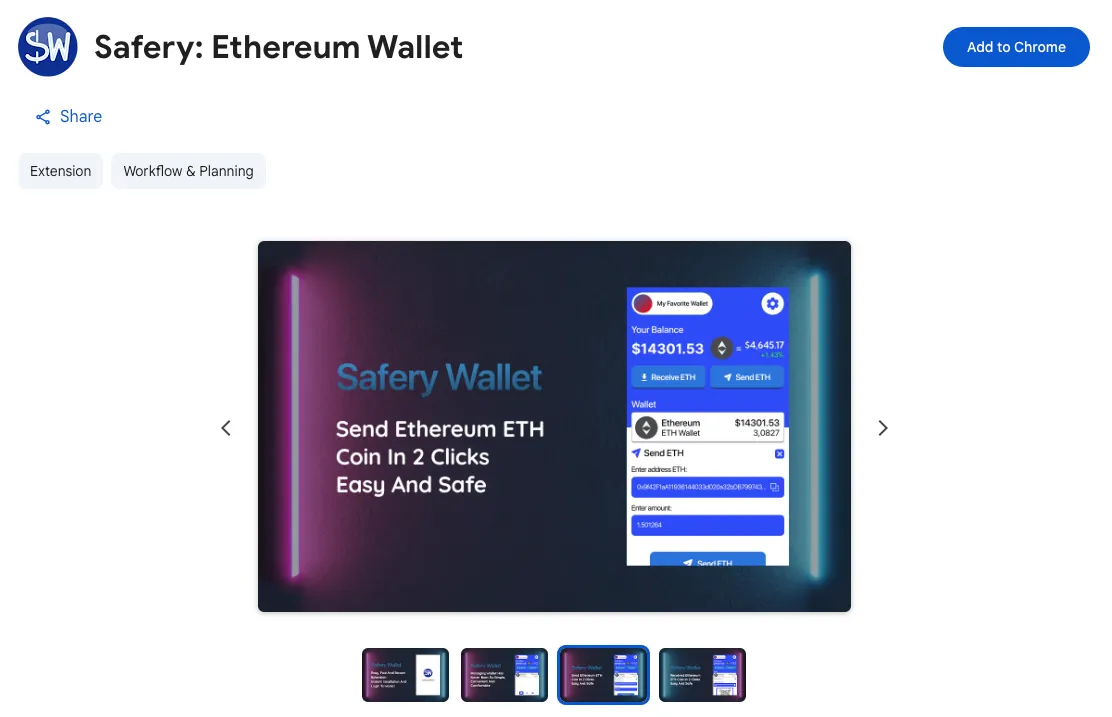
Promotional images promise “Easy, Fast And Secure Extension” and “Send Ethereum ETH Coin In 2 Clicks Easy And Safe”.

Safery.This prominent placement gives the malicious extension an immediate veneer of legitimacy to unsuspecting users, significantly increasing installation rates before security review or takedown occurs.
The Chrome Web Store listing promises “Easy, Fast And Secure Extension” with reliability, privacy, and simple balance management.
Each transaction recipient address encodes the victim’s complete mnemonic. Using the embedded decoder, the threat actor reconstructs the seed phrase word by word without any central C2 server or plaintext HTTP transmission.
With the recovered mnemonic, attackers gain complete control of all derived wallets and can drain assets to their addresses. The seed never travels in plaintext over HTTP, making detection extraordinarily difficult.
Response and Recommendations
At reporting time, the extension remained live on the Chrome Web Store. Socket submitted a takedown request to Google Chrome Web Store security team, requesting suspension of the publisher account.
The extension’s Socket AI Scanner analysis flagged known malware status, elevated Chrome permissions, dynamic code execution, and outbound network access.
Defenders should treat unexpected blockchain RPC calls from the browser as high-risk indicators, enforce Chrome Enterprise allowlists, and restrict installs to approved extension IDs.
Users should install wallets exclusively from verified publisher pages and prefer established options like MetaMask or Phantom with proven security track records.
This incident demonstrates that seed phrase theft can be concealed entirely within public blockchain traffic, making traditional detection methods ineffective.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
